[ad_1]
Sprawl occurs
Software program improvement organizations evolve. Groups develop. The variety of tasks will increase. Tech stacks change. Know-how and administration selections have turn into extra decentralized.
All through this evolution, the group’s AppSec instrument portfolio additionally grows. In dynamic organizations, this will result in “instrument sprawl.” A sprawling AppSec instrument portfolio consists of many level options, acquired by completely different groups at completely different instances to serve completely different (or, unknowingly, overlapping) functions. Sprawling instruments lead to knowledge silos with completely different terminology, task guidelines, and resolutions. This case ends in a wasted IT funds, and worse but, it may make it prohibitively time-consuming to combine, prioritize, and resolve threats.
In case your AppSec tooling is sprawling, and you’re feeling that it has outgrown your means to handle it successfully, it’s price investing the effort and time to get it below management. Doing so will provide help to:
- Acquire full visibility and end-to-end traceability of your software program provide chain from the primary line of code to manufacturing.
- See the place there are gaps or overlaps in your safety tooling.
- Lower your expenses by eliminating instruments that don’t yield incremental worth.
- Make safety an integral a part of the event course of as an alternative of an afterthought.
- Enhance safety alerts’ signal-to-noise ratios with automated triage and prioritization.
- Cut back guide work and automate protecting actions, all from a single location.
Listed below are 3 ways how OX’s Lively ASPM Platform helps to get your AppSec instrument sprawl below management so you possibly can maximize safety, productiveness, and ROI in your tooling investments:
1: Combine safety alerts to get rid of silos
One of many first issues you need to resolve to get a deal with on instrument sprawl is lack of visibility. That’s why you need to combine alerts out of your instruments right into a centralized place. Gaining centralized visibility into safety points makes safe improvement sooner and more practical:
- Improve signal-to-noise ratio; focus builders on points that matter.
- Catch safety points earlier within the improvement course of.
- Cut back elevating redundant or premature safety points.
- Keep away from delaying releases by over-prioritizing hygiene points,
- See associated points throughout instruments that point out a real assault kill chain.
Construct vs. Purchase
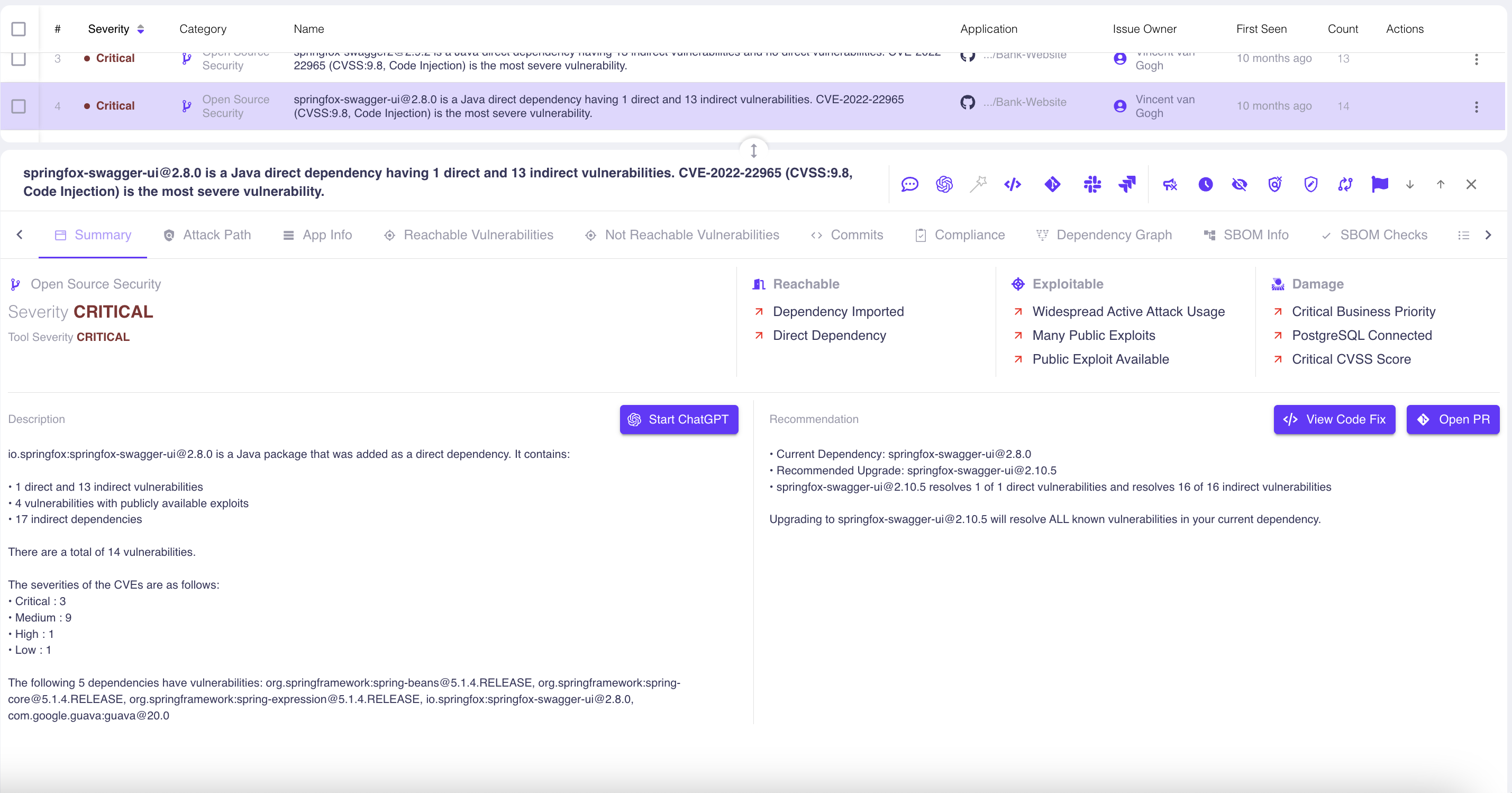
Integrating safety points out of your AppSec instruments right into a central dashboard is a good suggestion. We see corporations try to construct these in-house, however the success fee is low. Integrating so many programs is pricey and time-consuming. The sooner and more cost effective path to a centralized view of software program provide chain safety points is by way of a turnkey system. Search for a supplier that may give you all the data you want in a single, easy-to-view interface.
Utilizing our platform for instance, as you possibly can see within the OX dashboard above, hundreds of points from a number of instruments for a number of software program tasks are aggregated and displayed. Whether or not you construct or purchase, having this visibility is critically necessary. It’s a prerequisite for the following step in managing safety tooling in your software program provide chain.
Step 2: Automate subject triage, prevention, and backbone
It’s not unusual to see hundreds of alerts raised by tooling within the software program provide chain; it’s so noisy that builders typically ignore alerts. Automation can resolve the prioritization drawback by rising your alerting signal-to-noise ratio and in addition automating escalation and backbone for sooner, safer software program supply.
To provide you an thought of what’s attainable, let’s have a look at how automation performs an necessary function in minimizing noise within the setting utilizing OX Safety for instance…
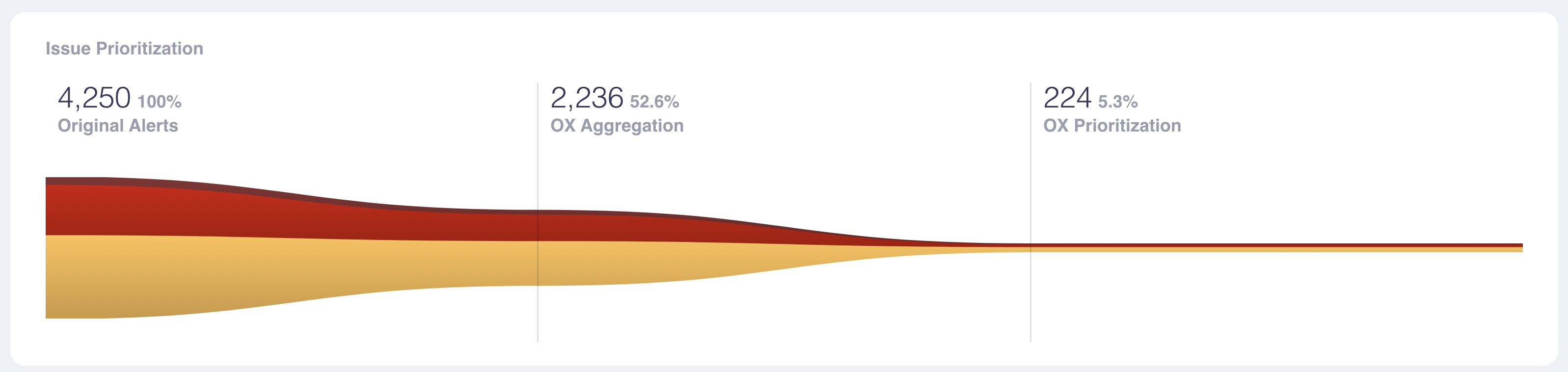
Automate subject triage and prioritization
Each time you create a brand new construct, OX produces a information graph for the construct that aggregates all the various safety points in your pipeline. OX deduplicates points and in addition prioritizes them by their potential enterprise impression. As you possibly can see under, hundreds of unique alerts are targeted down to a couple hundred that want probably the most pressing consideration:
The prioritized dangers and misconfigurations are organized by OX, utilizing the open-source framework OSC&R for context (extra on OSC&R later). This makes the severity and possession of the problems clearer to everybody. This readability helps get rid of severe safety points earlier within the improvement course of and in addition ensures that selections to dam releases for safety causes are well-rationalized and understood by the group.
Automate subject decision and prevention
One of many different issues with safety instruments sprawl is inconsistent task and backbone of points. A platform like OX solves this by by way of automated fixes and workflows, and in addition by offering suggestions and explanations to coach and empower your group:
It’s additionally necessary to leverage this intelligence throughout coding and configuration duties, not simply passively after the construct course of. Search for a platform that integrates into your builders’ IDEs, CI/CD, and different developer tooling to proactively stop points. Doing so streamlines your safe improvement course of:
3: Use the OSC&R framework to rationalize your instrument portfolio
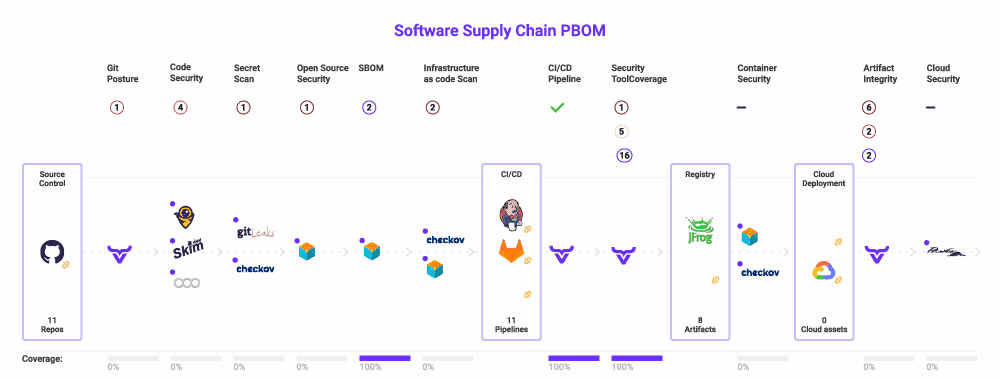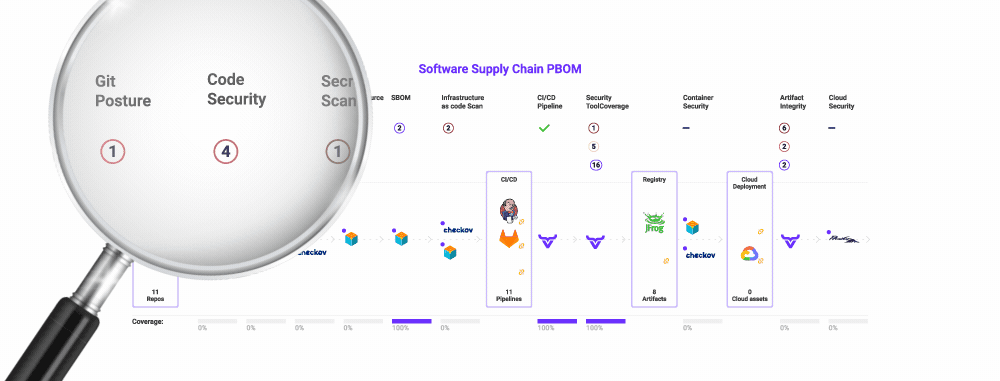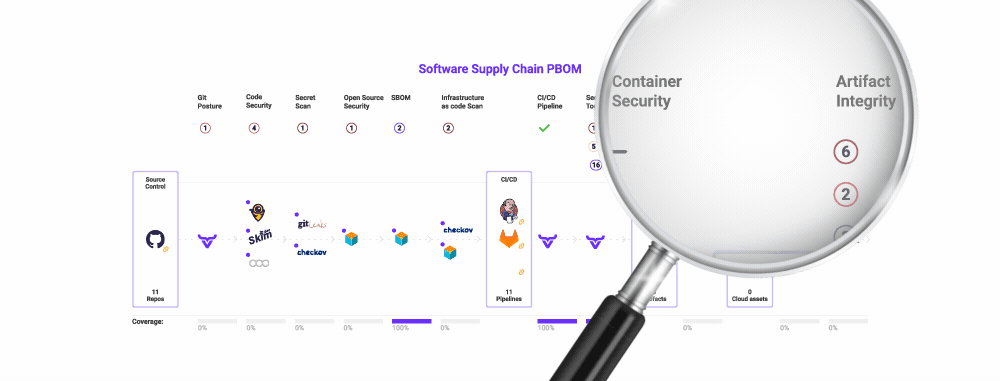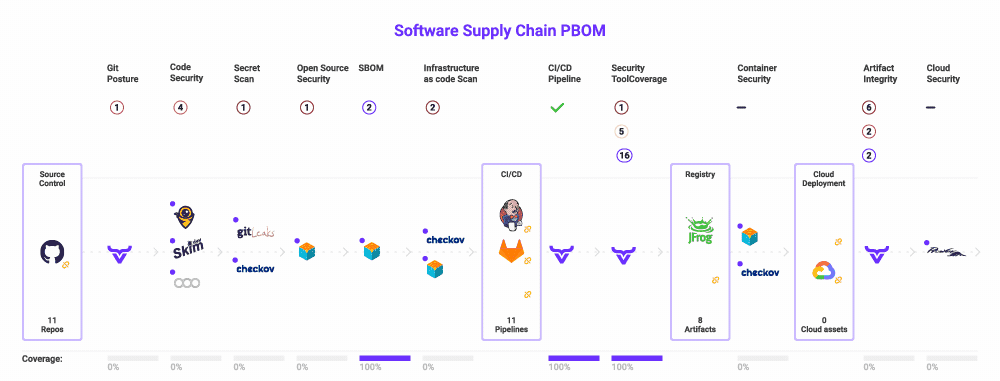
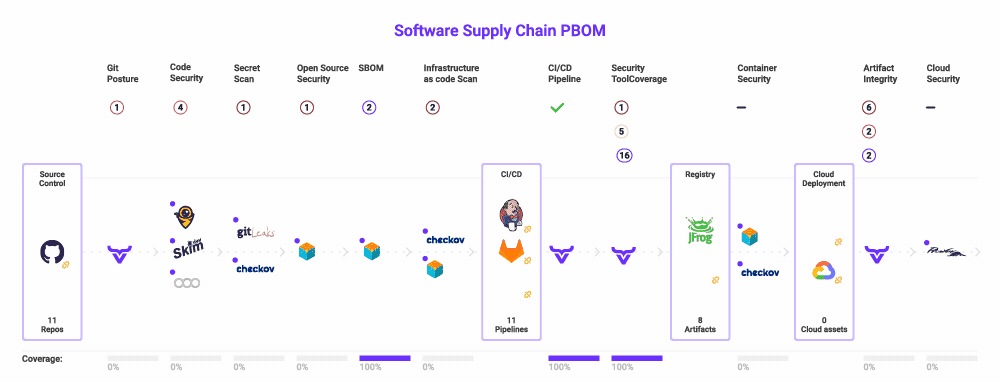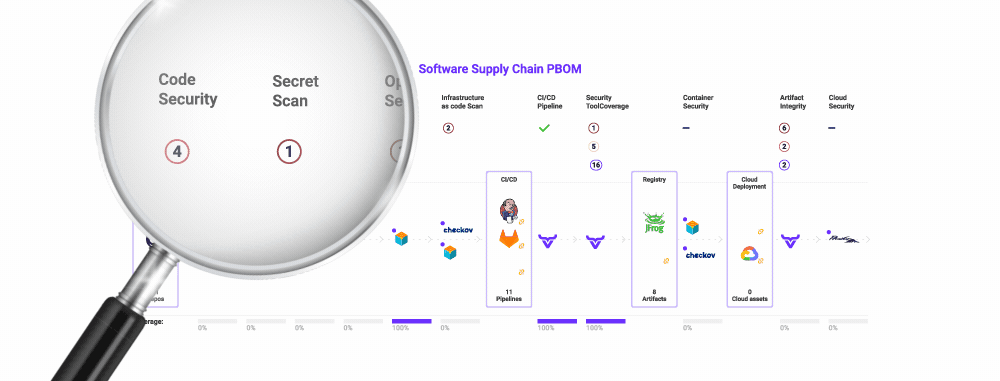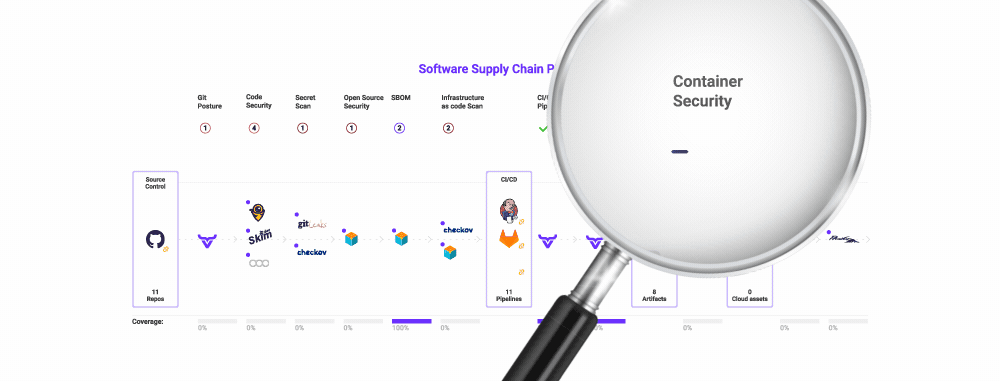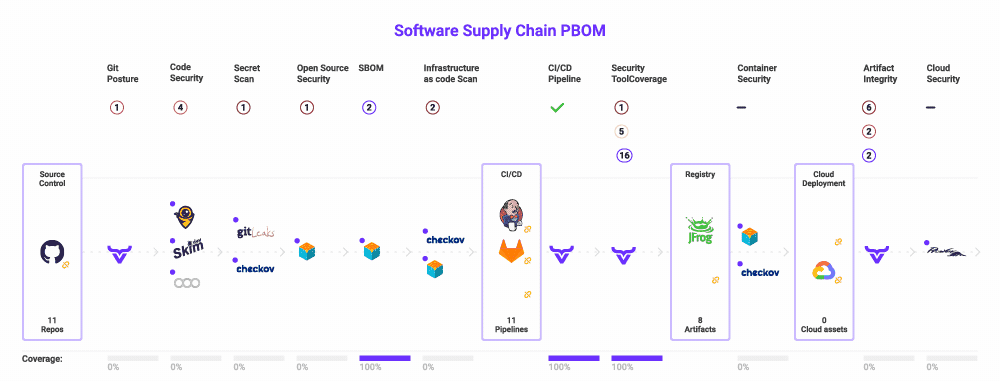
Lastly, you should guarantee you’re utilizing a framework that makes it clear what you should safe and which threats to look at. If in case you have this to your whole software program provide chain, you possibly can map your present instruments into it, revealing overlap and gaps in your danger protection.
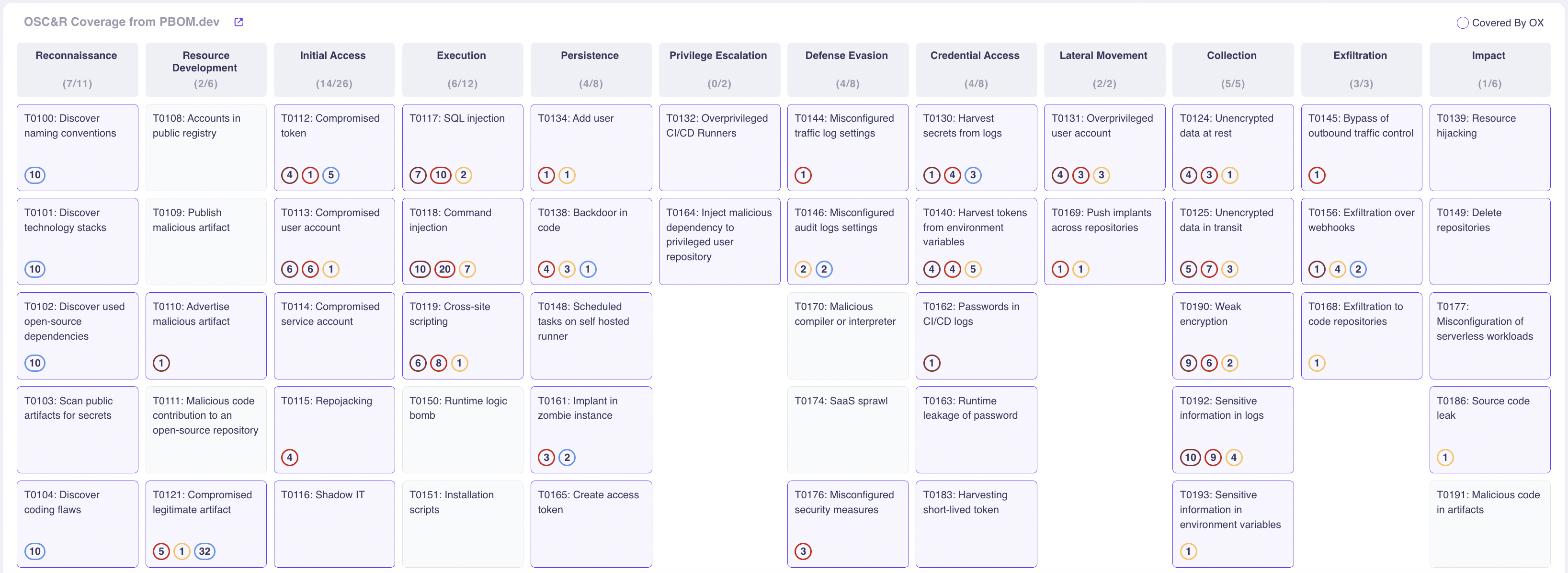
The excellent news is that this framework already exists. The Open Software program Provide Chain Assault Reference (OSC&R) is an business commonplace. It does for the software program provide chain what Mitre ATT&CK does for endpoint safety. As you possibly can see under, OSC&R paperwork the attainable assault factors and mechanisms for each a part of the software program provide chain:
With OSC&R, you possibly can map your AppSec tooling to the threats and make better-informed selections about which instruments to amass, retain, or finish of life. OX Safety automates this by scanning your setting and pipelines – from cloud to code. Whereas scanning, OX mechanically identifies which instruments you’re utilizing, and if further ones must be deployed so as to maximize your protection. It is best to now have an AppSec instrument portfolio that covers your software program provide chain with out gaps or overlap.
Get began at the moment
Getting your safety instruments sprawl below management may sound difficult, however dwelling with it’s not an choice for contemporary software program groups. OSC&R and intelligence and automation from OX Safety can assist!
The publish 3 ways to handle cybersecurity instrument sprawl in your software program provide chain appeared first on OX Safety.
*** It is a Safety Bloggers Community syndicated weblog from OX Safety authored by William Penfield. Learn the unique publish at: https://www.ox.safety/three-ways-to-manage-cybersecurity-tool-sprawl-in-your-software-supply-chain/
[ad_2]