[ad_1]
The China-based risk actor often called Mustang Panda is suspected to have focused Myanmar’s Ministry of Defence and Overseas Affairs as a part of twin campaigns designed to deploy backdoors and distant entry trojans.
The findings come from CSIRT-CTI, which stated the actions happened in November 2023 and January 2024 after artifacts in reference to the assaults have been uploaded to the VirusTotal platform.
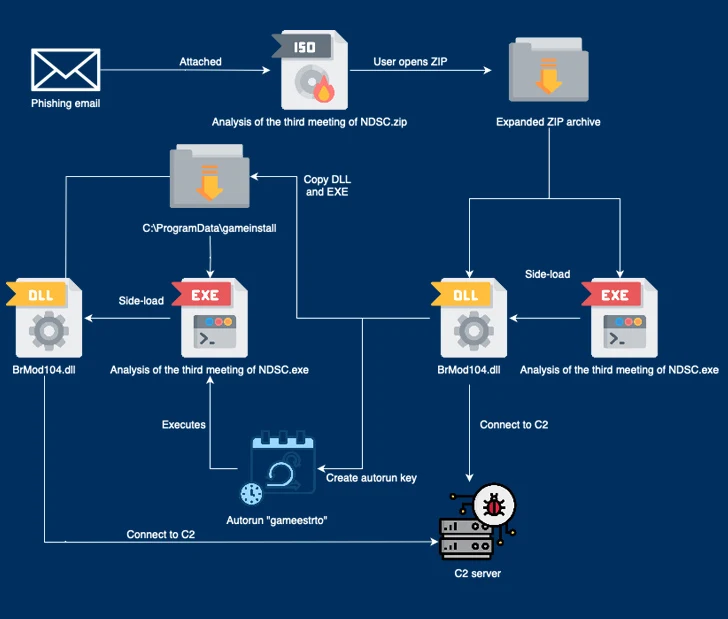
“Essentially the most distinguished of those TTPs are the usage of authentic software program together with a binary developed by engineering agency Bernecker & Rainer (B&R) and a part of the Home windows 10 improve assistant to sideload malicious dynamic-link libraries (DLLs),” CSIRT-CTI stated.
Mustang Panda, energetic since at the very least 2012, can also be acknowledged by the cybersecurity neighborhood beneath the names BASIN, Bronze President, Camaro Dragon, Earth Preta, HoneyMyte, RedDelta, Purple Lich, Stately Taurus, and TEMP.Hex.
In current months, the adversary has been attributed to assaults focusing on an unnamed Southeast Asian authorities as effectively because the Philippines to ship backdoors able to harvesting delicate info.
The November 2023 an infection sequence begins with a phishing e-mail bearing a booby-trapped ZIP archive attachment containing a authentic executable (“Evaluation of the third assembly of NDSC.exe”) that is initially signed by B&R Industrial Automation GmbH and a DLL file (“BrMod104.dll”).
The assault takes benefit of the truth that the binary is vulnerable to DLL search order hijacking to side-load the rogue DLL and subsequently set up persistence and get in touch with with a command-and-control (C2) server and retrieve a identified backdoor known as PUBLOAD, which, in flip, acts as a customized loader to drop the PlugX implant.
“The risk actors try to disguise the [C2] site visitors as Microsoft replace site visitors by including the ‘Host: www.asia.microsoft.com’ and ‘Consumer-Agent: Home windows-Replace-Agent’ headers,” CSIRT-CTI famous, mirror a Could 2023 marketing campaign disclosed by Lab52.
However, the second marketing campaign noticed earlier this month employs an optical disc picture (“ASEAN Notes.iso”) containing LNK shortcuts to set off a multi-stage course of that makes use of one other bespoke loader known as TONESHELL to possible deploy PlugX from a now-inaccessible C2 server.
It is price noting {that a} related assault chain attributed to Mustang Panda was beforehand unearthed by EclecticIQ in February 2023 in intrusions aimed toward authorities and public sector organizations throughout Asia and Europe.
“Following the insurgent assaults in northern Myanmar [in October 2023], China has expressed concern relating to its impact on commerce routes and safety across the Myanmar-China border,” CSIRT-CTI stated.
“Stately Taurus operations are identified to align with geopolitical pursuits of the Chinese language authorities, together with a number of cyberespionage operations towards Myanmar prior to now.”
[ad_2]