[ad_1]
Within the ever-evolving digital info panorama, databases are the muse of quite a few purposes and programs, holding a money cow of useful info. As corporations considerably rely on these info databases, defending and trying out information sources in case of a safety violation or transgression turns into important. That is the place Database Forensics Restoration Providers enter play, supplying an important assortment of gadgets plus methods to unwind the secrets and techniques hid inside these digital safes.
Recognizing Database Forensics: Recognizing Digital Hints
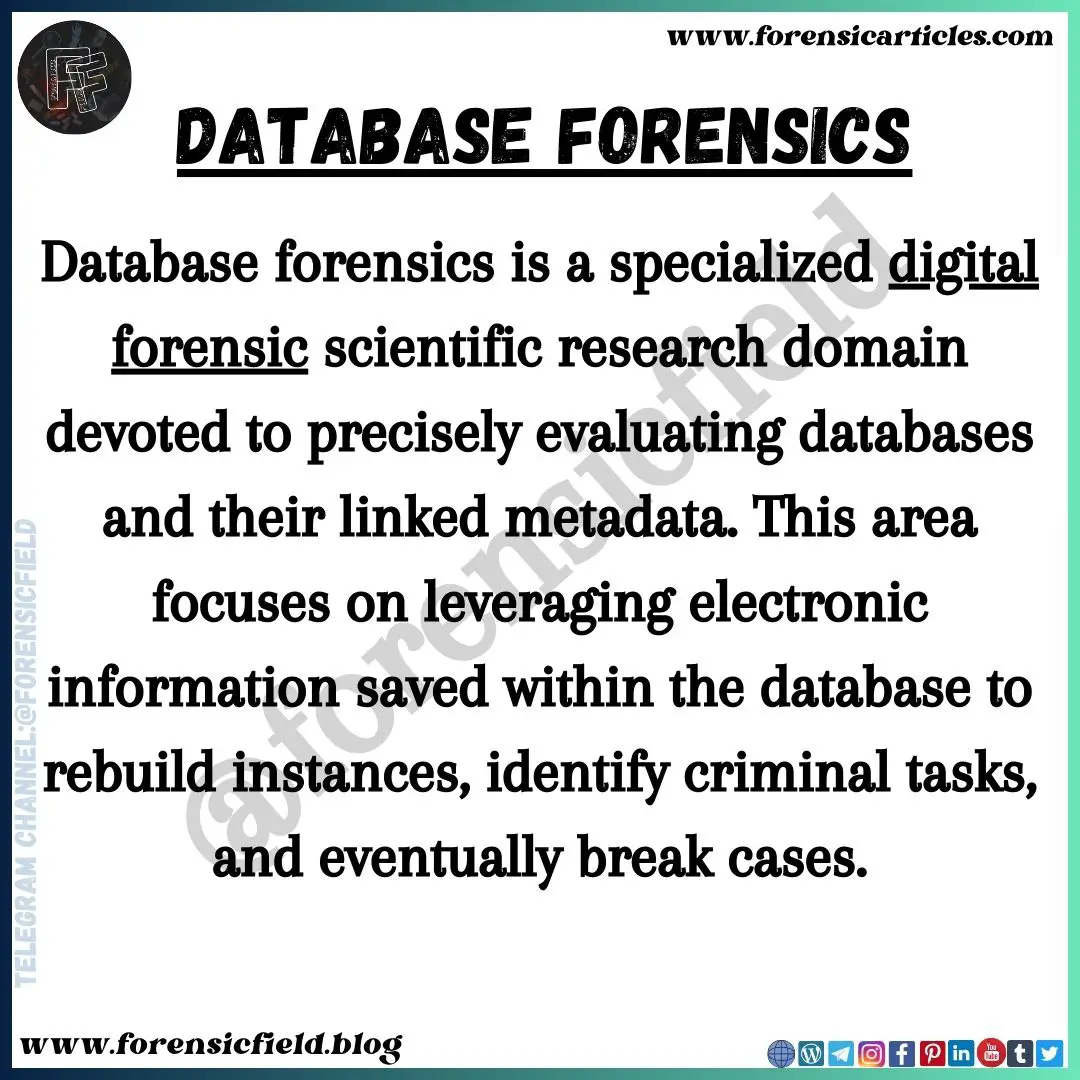
Database forensics is a specialised digital forensic scientific analysis area devoted to exactly evaluating databases and their linked metadata. This space focuses on leveraging digital info saved throughout the database to rebuild cases, determine felony duties, and ultimately break instances.
Essentially, database forensics shares commonalities with pc system forensics, sticking to well-established forensic methods and utilizing investigatory methods targeting each the elements of the database in addition to their metadata. Reside logical gadgets could also be crucial, particularly when contemplating cached info’s presence in an internet server’s RAM.
An important factor of forensic analysis in a database contains checking and confirming timestamps related to the improve time of a row in a relational desk. This examination is crucial for establishing the actions of a database particular person’s actions and integrating an in depth understanding of the events beneath examination.
Database forensics is crucial in unwinding digital concepts stored inside information sources utilizing an organized method to take a look at and consider digital proof. It stands alongside pc system forensics, prolonging its focus on the specialised world of knowledge sources and metadata and guaranteeing an entire examination of digital info to repair cases and cope with cybercrime.
Database Forensic Investigation Course of
Getting on an information supply investigatory examination entails a exact and arranged process important for revealing digital proof and addressing cases. The journey with information supply forensics usually adheres to 4 very important phases:
1. Acquisition & Restoration:
Step one in any database forensics investigation is buying and therapeutic info. This entails accessing eliminated or hard-to-reach paperwork, which prepares for succeeding evaluations. A restoration course of is crucial to making sure the honesty of the information supply paperwork. This motion is particularly important when entailing financial felony actions equivalent to web buy scams or money laundering, the place information can also be eliminated and harmed.
2. Inspection:
The evaluation stage begins when the important info is acquired and recouped. Accessing the focused database information is significant all through this section, permitting personal investigators to gather all of the wanted information for the subsequent analysis. Nonetheless, obstacles may emerge, notably when dealing with information supply paperwork secured by passwords, accounts, and different privateness actions. Eliminating these challenges is significant for an in depth examination.
3. Evaluation:
The guts of the examination hinges on the analysis stage. A whole evaluation of all supplied and typical databases is carried out to find out doable hints and directions for scenario splitting. The dependability of the analysis is crucial, making the method used on this stage an establishing consideration of the investigatory process. Discovering patterns and irregularities within the info is essential to assembling the issue of the digital felony offence beneath evaluation.
4. Reporting:
With the evaluations complete, the searches are assembled right into a digital forensic report. This report is an in depth referral, providing an aesthetic and an ordered map detailing suggestions and methods. It’s a guidebook for a lot deeper examinations and is likely to be utilized in lawsuits. Nonetheless, it’s essential to do not forget that fundamental sustaining gadgets may solely typically work clinically, probably making the database proof inadmissible in courtroom. It’s recommended that refined choices equivalent to Database Forensic Providers (DBF) be taken to overcome this impediment. This ensures a medical technique for database forensics, decreasing the hazard of proof failing to fulfil admissibility necessities.
The Necessities of Database Forensic Providers
- Information Restoration and Reconstruction: The preliminary step in any investigatory examination contains recovering and restoring endangered info. Investigatory professionals use revolutionary gadgets to acquire erased or harmed info, guaranteeing an in depth examination of the information supply.
- Achieve Entry to Logs Evaluation: Accessibility logs function an digital path, taping each communication with the information supply. Assessing these logs can expose unapproved achieve entry to questionable questions and the timeline of events inflicting a security incidence, recognizing that accessing the information supply and when is important for mapping the start of the violation.
- Buy Evaluation: Offers are the muse of database procedures. Investigation consultants examine these purchases to acknowledge irregularities, unapproved modifications, or doubtful patterns. This assists in growing the assailant’s modus operandi and comprehending the extent of harm.
- Metadata Examination: Metadata presents essential info concerning the framework in addition to the corporate of the database. Investigatory professionals study metadata to uncover modifications within the schema, alterations to permissions, and any unapproved changes which may have occurred all through the protection violation.
- Forensics Imaging: Producing a digital image of the jeopardized information supply is crucial for sustaining the soundness of the proof. This image permits personal investigators to collaborate on reproducing the preliminary database with out modifying the central useful resource, guaranteeing an in depth and actual analysis.
- Chain of Custody Documentation: An intensive chain of wardship is important within the forensic process. Right paperwork ensures that the gathered proof follows lawful proceedings. Investigatory consultants must videotape each motion of the examination, from info buy to analysis and protection.
- Collaboration with Authorized Specialists: Database forensics investigations usually result in lawsuits. Working with lawful specialists ensures that the examination complies with lawful wants and that looking out could be adequately supplied in courtroom if important.
In contrast to most popular digital forensic areas equivalent to video, audio, or cellular forensics, database forensics will not be regularly taken on. Performing database forensics requires data of database-related innovation; with out this experience, it may be examined and won’t produce permissible proof in courtroom. Nonetheless, utilizing medical gadgets plus database forensics programs has change into way more prevalent in the previous few years. Police, armed forces, and data corporations in quite a few nations generally use Database Forensics Options all through the development of databases.
A number of Selection Questions
1. What’s the major focus of database forensics?
- A. Analyzing Web visitors
- B. Evaluating databases and their metadata
- C. Recovering deleted emails
- D. Analyzing social media exercise
2. Which section of the database forensic investigation includes making a digital Forensic Report?
- A. Acquisition & Restoration
- B. Inspection
- C. Evaluation
- D. Reporting
3. What’s the important goal of Information Restoration and Reconstruction in investigatory examinations?
- A. Accessing deleted social media posts
- B. Recovering and restoring endangered info
- C. Analyzing Web looking historical past
- D. Analyzing e-mail threads
4. Why is the examination of metadata essential in database forensic investigations?
- A. To trace textual content messages
- B. To uncover adjustments in database construction and permissions
- C. To research video information
- D. To assessment audio recordings
5. What’s the major position of collaboration with Authorized Specialists in database forensics investigations?
- A. Dealing with social media accounts
- B. Offering authorized recommendation on private issues
- C. Making certain compliance with authorized necessities and courtroom shows
- D. Analyzing gaming actions
Solutions
- 1. Reply: B
- 2. Reply: D
- 3. Reply: B
- 4. Reply: B
- 5. Reply: C
Writer Bio
Mr. Vijay Mandora, Chairman & Managing Director of ECS Infotech Pvt. Ltd is a distinguished technocrat and first-generation entrepreneur with a Bachelor’s diploma in Engineering, specializing in Electronics and Telecommunications. His imaginative and prescient for environmental sustainability led to the institution of ECS Infotech, an organization devoted to the Reverse Logistics of Info Expertise, aiming to increase the lifespan of IT merchandise and set up world-class restore centres in India.
Moreover, ECS is ready to launch an e-waste centre to profit the federal government, society, and the IT business. A pioneer in Reverse Logistics and Inexperienced IT, Mr Mandora’s management is driving the launch of a state-of-the-art service centre for HDD and LCD in Ahmedabad, Gujarat.
Associated
[ad_2]