[ad_1]
September 22, 2023
With the latest leaks of database fragments from plenty of banks, fraudsters now have entry to clients’ private info. The criminals use this info to achieve the belief of their victims. Pretending to be financial institution assist employees, the criminals report that suspicious exercise has been detected on the sufferer’s account, which may lead to a lack of cash. To forestall theft, the sufferer allegedly wants to put in a “safety” utility on their system. The attackers counsel that they go to the app retailer and seek for apps like “Sberbank assist”, “VTB assist” and the like.
Supply: nakopi-deneg.ru
Actually, till just lately, the highest Google Play outcomes for such search phrases had been purposes comparable to AweSun Distant Desktop, RustDesk Distant Desktop, and AnyDesk Distant Desktop. This case is because of the truth that the applying rating system in Google Play takes under consideration the applying that customers click on on after getting into their search question. Thus, the extra individuals seek for an utility utilizing the key phrases “assist bank_name” and mistakenly click on the hyperlink for a distant administration utility, the extra Google Play will advocate such an utility to customers.
It must be famous that in and of themselves, distant administration utilities aren’t malicious. They grow to be an issue when they’re used to carry out unlawful actions.
After the app is put in, the scammers ask the sufferer for a singular identifier after which take full management of the system. Entry to the system permits them to make funds and transfers from the sufferer’s account. Sadly for the sufferer, will probably be unimaginable to show the hack and revoke the fee order in such a state of affairs, as a result of from the financial institution’s viewpoint, it was the client’s system that interacted with the fee system.
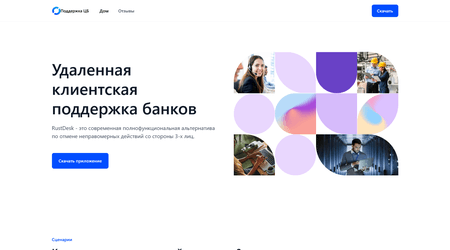
Google has now eliminated the RustDesk utility from the Google Play retailer. In consequence, the attackers have moved their actions to their very own community assets and at the moment are encouraging victims to go to websites comparable to hххps://помощникбанков[.]рф.
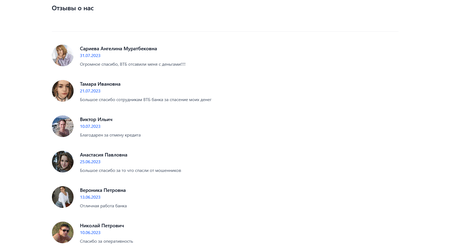
On such websites, potential victims are prompted to obtain the now-familiar RustDesk utility. On some websites, to make the downloaded purposes extra convincing, the names and icons are changed with these of a specific financial institution. A bit with testimonials from “glad customers” additionally delivers an extra reassuring psychological impact.
Dr.Net antivirus detects the RustDesk utility as Instrument.RustDesk.1.origin and its modifications as Android.FakeApp.1426. For extra safety, the URL filter element of Dr.Net antivirus blocks entry to malicious web sites, stopping customers from falling prey to scams.
Physician Net wish to remind you:
- Be cautious about accepting calls from banks and different organizations.
- By no means set up applications in your gadgets at another person’s request.
- Don’t share codes from SMS or push notifications with anybody.
- Don’t speak to “financial institution representatives”. In the event that they inform you unauthorized prices had been made to your account, grasp up. If you wish to make it possible for every part is okay, name the financial institution your self utilizing the quantity in your card.
Learn extra about Instrument.RustDesk.1.origin
Learn extra about Android.FakeApp.1426
Indicators of compromise:
- помощникбанков[.]рф
- поддержкабанка[.]рф
- поддержка-банка[.]рф
- цбподдержка[.]рф
- поддержкацб[.]рф
- 24поддержка[.]рф
- sha1:2fcee98226ef238e5daa589fb338f387121880c6
- sha1:f28cb04a56d645067815d91d079b060089dbe9fe
- sha1:9a96782621c9f98e3b496a9592ad397ec9ffb162
- sha1:535ecea51c63d3184981db61b3c0f472cda10092
- sha1:ee406a21dcb4fe02feb514b9c17175ee95625213
[ad_2]