[ad_1]
On February 15th, the Cybersecurity and Infrastructure Safety Company (CISA) and the Multi-State Data Sharing & Evaluation Middle (MS-ISAC) issued an advisory highlighting the outcomes of their incident response investigation right into a state authorities group’s community whose delicate information together with host/person particulars and different pertinent metadata had been posted to the darkish net. Detailed details about this investigation and the related techniques, strategies, and procedures (TTPs) are listed in Risk Actor Leverages Compromised Account of Former Worker to Entry State Authorities Group.
Technical Particulars
The advisory reveals that the state authorities group was notified that a number of paperwork containing delicate community and person information had been out there for buy on a darkish net brokerage web site. CISA and MS-ISAC revealed that unknown risk actors had been capable of entry these delicate paperwork by leveraging the stolen credentials and meant to promote this information on the darkish net for a revenue. The thorough investigation (carried out on the organizational on-prem setting and their Azure deployment), revealed that these stolen credentials belonged to a former worker who could not have been correctly faraway from the organizational Energetic Listing (AD). Investigation revealed the next particulars:
- Primarily based on the log information, risk actors had been capable of first join from an unknown digital machine (VM) to the sufferer’s on-prem community by leveraging IP addresses belonging to the interior digital non-public community (VPN). Their main goal of doing so was to mix in with legit site visitors and keep undetected.
- Risk actors had been capable of acquire entry by leveraging the credentials of a former worker who had admin-level entry. These credentials had been possible stolen in a separate information breach. This former worker had entry to 2 digital servers together with the organizational SharePoint and one other on their earlier workstation. The workstation was virtualized from a bodily workstation utilizing the Veeam Bodily to Digital (P2V) perform throughout the backup software program.
- Risk actors had been then capable of receive the credentials of one other worker from the digital SharePoint server. These new credentials had world area administrator entry which enabled the risk actors to entry the organizational on-premises AD in addition to the Azure AD.
- By a connection from the VM, the risk actor carried out LDAP queries of the AD, possible utilizing the open-source instrument “AdFind.exe” to gather person, host, and belief relationship data. These LDAP queries had been additionally used to generate the textual content file containing the stolen information that was supplied on the market on the darkish net.
- Risk actors additionally used each units of stolen credentials to carry out additional community and repair discovery by connecting to a mess of providers on the organizational community.
- There have been no indications the risk actor additional compromised the group by transferring laterally from the on-premises setting to the Azure setting.
Essential Be aware for SafeBreach Clients – Protection for AA24-046A (State Authorities Assault)
As quickly as particulars had been made out there, the SafeBreach Labs groups mapped present assaults within the Hacker’s Playbook to this US-CERT instantly. It is very important observe that present SafeBreach prospects already had FULL protection in opposition to the entire TTPs recognized within the advisory. Please run/ re-run the assaults listed beneath to make sure your environments are protected in opposition to these TTPs.
Current Behavioral Assaults Associated to CERT Alert
- #7211 – Accumulate Azure credentials (Home windows)
- #7005 – Create function task (Azure)
- #6800 – Area Controller discovery utilizing person credentials
- #6799 – Area Controller discovery utilizing interactive session token
- #6581 – Uncover area computer systems utilizing LDAP methodology
- #6578 – Uncover area customers utilizing LDAP methodology
- #6550 – Agentless lateral motion by way of SMB and RCE, utilizing Impersonated person
- #6513 – Agentless lateral motion by way of SMB and RCE, utilizing Mimikatz
- #6483 – Agentless lateral motion by way of SMB and RCE, utilizing Token duplication
- #5671 – Agentless lateral motion by way of Home windows Distant Administration
- #2306 – Area Belief Discovery
- #1339 – Distant command execution by PSExec
What You Ought to Do Now
SafeBreach prospects can now validate their safety controls in opposition to these TTPs in a number of methods.
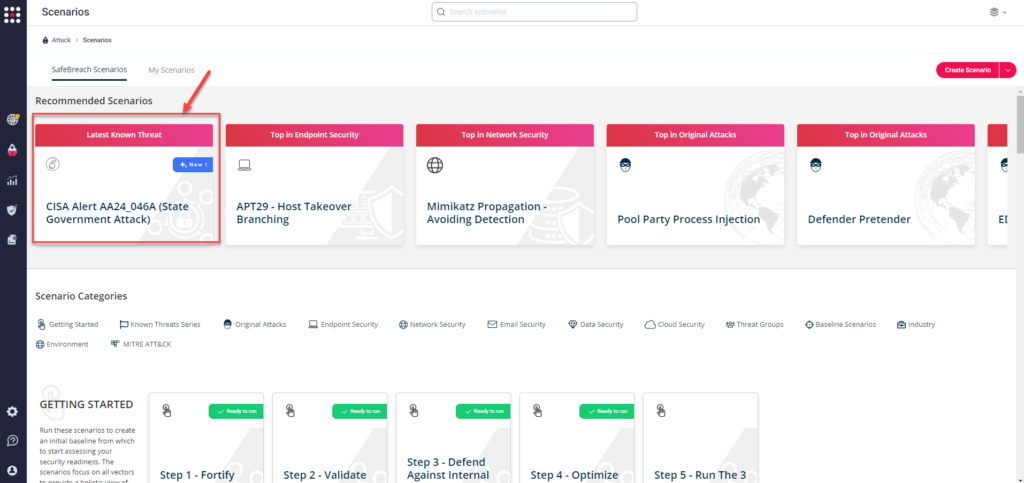
Technique 1 – You'll be able to go to the “SafeBreach Eventualities” web page and select the AA24_046A (State Authorities Assault) state of affairs from the record of accessible eventualities.
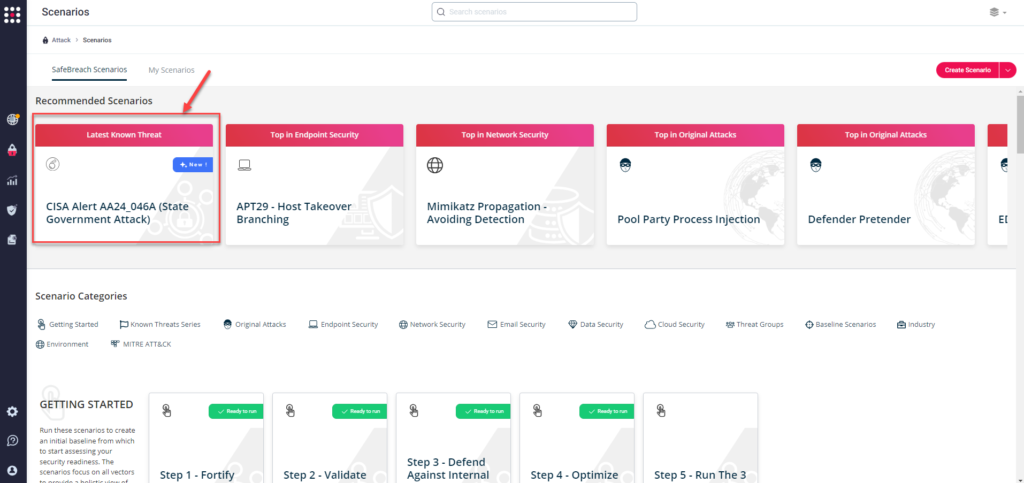
Technique 2 – From the Assault Playbook, choose and filter assaults associated to US-CERT Alert AA24_046A (State Authorities Assault). Moreover, you may confer with the record above as effectively to make sure a complete degree of protection.
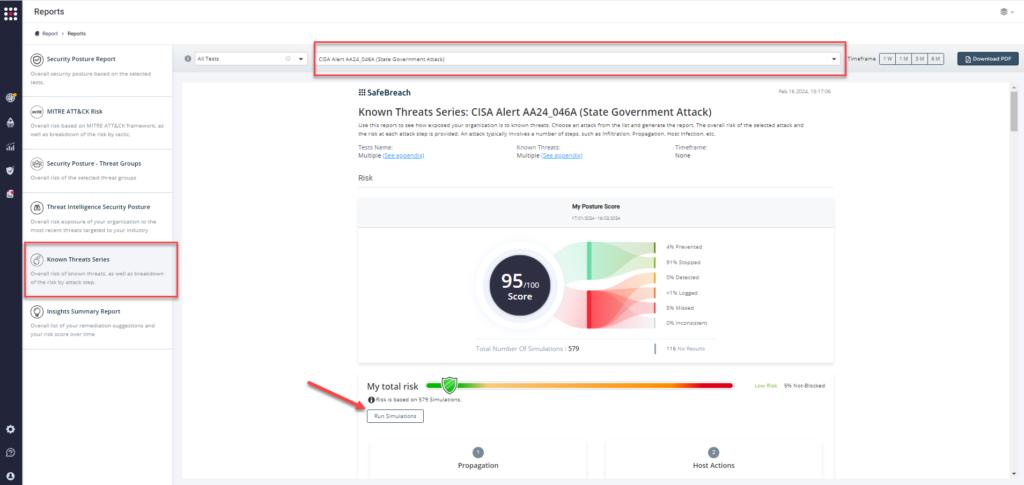
Technique 3 – From the Recognized Assault Sequence report, choose the AA24_046A (State Authorities Assault) report and choose Run Simulations which is able to run all assault strategies.
NOTE – CISA recommends regularly validating your safety program, at scale, in a manufacturing setting to make sure optimum efficiency in opposition to rising risk of superior cyber threats. Extra suggestions embody:
- Evaluate present administrator accounts to find out their necessity and solely preserve administrator accounts which are important for community administration.
- Prohibit the usage of a number of administrator accounts for one person.
- Create separate administrator accounts for on-premises and Azure environments to phase entry.
- Use phishing-resistant multifactor authentication (MFA).
- Set up coverage and process for the immediate removing of pointless accounts and teams from the enterprise, particularly privileged accounts.
- Consider Tenant Settings.
- Assess the Safety Configuration of Azure Surroundings.
- Consider Conditional Entry Insurance policies.
- For detailed details about mitigations and incident response, please refer to the complete advisory.
[ad_2]