[ad_1]
Final week, a brand new model of the Bazar Loader Area Era Algorithm (DGA) appeared. I already analyzed two earlier variations, so I’m protecting this publish quick.
The DGA nonetheless makes use of the eponymous .bazar high stage area, however the second stage domains are shorter with 8 characters as an alternative of 12 for the earlier variations:
liybelac.bazar
izryudew.bazar
biymudqe.bazar
fuicibem.bazar
biykonem.bazar
aqtielew.bazar
yptaonem.bazar
exyxtoca.bazar
iqfisoew.bazar
aguponew.bazar
exogelqe.bazar
exybonyw.bazar
etymonac.bazar
I analysed the next pattern with out a lot obfuscation. There are various different samples which have further reverse engineering counter measures akin to junk code, however a fast comparability revealed no useful variations.
- MD5
- c6502d4dd27a434167686bfa4d183e89
- SHA1
- bddbceefe4185693ef9015d0a535eb7e034b9ec3
- SHA256
- 35683ac5bbcc63eb33d552878d02ff44582161d1ea1ff969b14ea326083ea780
- Measurement
- 336 KB (344576 Bytes)
- Compile Timestamp
- 2020-12-10 13:05:18 UTC
- Hyperlinks
- MalwareBazaar, Malpedia, Cape, VirusTotal
- Filenames
- 1ld.3.v1.exe, 35683ac5bbcc63eb33d552878d02ff44582161d1ea1ff969b14ea326083ea780 (VirusTotal)
- Detections
- Virustotal: 8/72 as of 2020-12-11 02:58:32 – Win64/Bazar.Y (ESET-NOD32), Backdoor.Win32.Bazdor.co (Kaspersky), Trojan.Win64.BAZALOADER.SMYAAJ-A (TrendMicro), Trojan.Win64.BAZALOADER.SMYAAJ-A (TrendMicro-HouseCall)
Unpacking the pattern results in this:
- MD5
- e44cfd6ecc1ea0015c28a75964d19799
- SHA1
- cb294c79b5d48840382a06c4021bc2772fdbcf63
- SHA256
- 52e72513fe2a38707aa63fbc52dabd7c7d2c5809ed7e27f384315375426f57bf
- Measurement
- 96 KB (98816 Bytes)
- Compile Timestamp
- 2020-12-09 10:16:56 UTC
- Hyperlinks
- MalwareBazaar, Malpedia, Cape, VirusTotal
- Filenames
- content material.28641.20903.13470.9122.7127 (VirusTotal)
- Detections
- Virustotal: 4/75 as of 2020-12-15 21:30:37
Reverse Engineering
Aside from the frequent dynamic loading of Home windows API capabilities and encrypted strings, Bazar Loader depends on arithmetic substitution through identities to obfuscate the code. The next relationship is especially usually used:
$$ a oplus b = (sim a cdot b) + (a cdot sim b) $$
The identical obfuscation can also be utilized by Zloader. It makes the code very laborious to learn. Here’s a small snippet from the DGA:
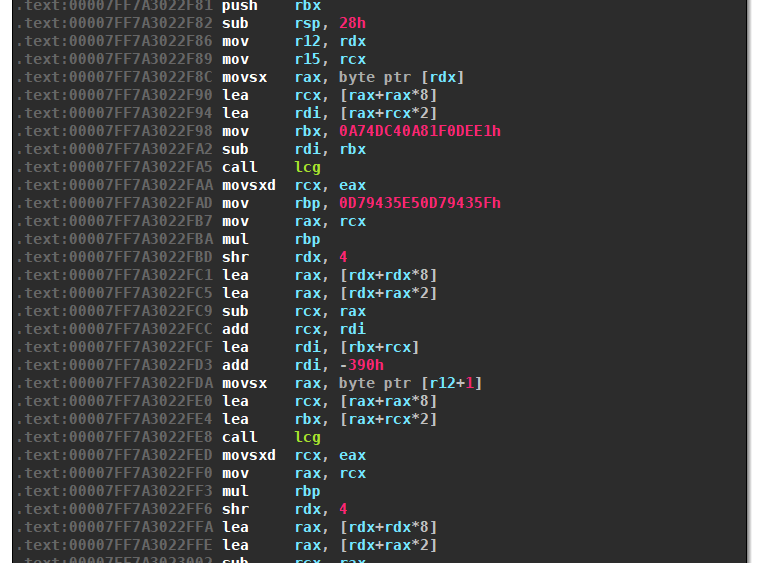
Hex Ray’s decompiler additionally produces actually messy code as a result of the arithmetic identities will not be simplified:
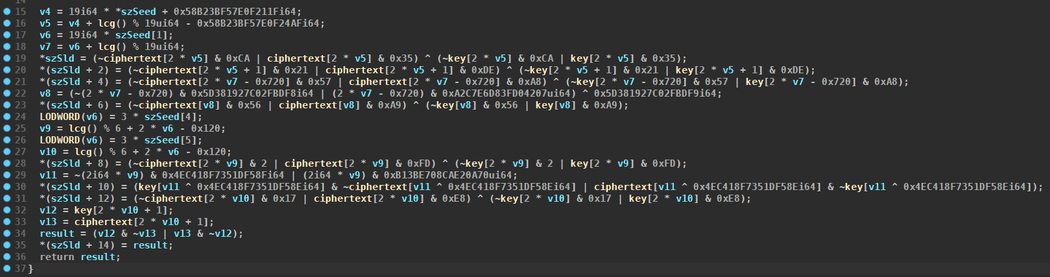
The DGA makes use of the present month and yr because the seed. The seed is saved as a string, and its 4 ASCII characters are the idea for choosing 4 character pairs. These 4 pairs are joined to kind the 8 second stage characters.
The listing of character pairs is generated by calculating the cartesian product of the consonants “bcdfghklmnpqrstvwxz” and vowels (with y) “aeiouy”. The product is calculated each methods, resulting in 19·6·2 character pairs. These pairs are then concatenated into a big string of 456 characters by utilizing a hardcoded sequence of random numbers:
qeewcaacywemomedekwyuhidontoibeludsocuexvuuftyliaqydhuizuctuiqow
agypetehfubitiaziceblaogolryykosuptaymodisahfiybyxcoleafkudarapu
qoawyluxqagenanyoxcygyqugiutlyvegahepovyigqyqibaeqynyfkiobpeepby
xaciyvusocaripfyoftesaysozureginalifkazaadytwuubzuvoothymivazyyz
hoevmeburedeviihiravygkemywaerdonoyryqloammoseweesuvfopiriboikuz
orruzemuulimyhceukoqiwfexuefgoycwiokitnuneroxepyanbekyixxiuqsias
The string is then encrypted utilizing a random xor key of the identical size.
Aside from the date-based seed, the DGA additionally makes use of a normal linear congruential generator (LCG) to choose the 4 character pairs. The LCG is seeded with the present processor tick depend and thus unpredictable. For the primary two character pairs, the random quantity is taken mod 19, and for the remaining two pairs mod 6. These numbers correspond to the size of the consonants and vowels array, however make no sense on this context. As a result of the random numbers are unpredictable, any mixture of the 19·19·6·6 = 12996 character pairs may very well be picked. Bazar Loader generates 10’000 domains per run, however doesn’t assure they’re distinctive. On common, 6975 distinctive domains are anticipated:
$$ mathbb{E} = 12996left( 1 – left(frac{12996-1}{12966}proper)^{10000} proper) = 6975 $$
Even with the quick ready time between resolving domains, the malware might want to run a very long time to get by the listing of domains.
Reimplementation in Python
The next Python code reveals how the domains are generated:
from itertools import product
from datetime import datetime
import argparse
from collections import namedtuple
Param = namedtuple('Param', 'mul mod idx')
pool = (
"qeewcaacywemomedekwyuhidontoibeludsocuexvuuftyliaqydhuizuctuiqow"
"agypetehfubitiaziceblaogolryykosuptaymodisahfiybyxcoleafkudarapu"
"qoawyluxqagenanyoxcygyqugiutlyvegahepovyigqyqibaeqynyfkiobpeepby"
"xaciyvusocaripfyoftesaysozureginalifkazaadytwuubzuvoothymivazyyz"
"hoevmeburedeviihiravygkemywaerdonoyryqloammoseweesuvfopiriboikuz"
"orruzemuulimyhceukoqiwfexuefgoycwiokitnuneroxepyanbekyixxiuqsias"
"xoapaxmaohezwoildifaluzihipanizoecxyopguakdudyovhaumunuwsusyenko"
"atugabiv"
)
def dga(date):
seed = date.strftime("%mpercentY")
params = [
Param(19, 19, 0),
Param(19, 19, 1),
Param(6, 6, 4),
Param(6, 6, 5)
]
ranges = []
for p in params:
s = int(seed[p.idx])
decrease = p.mul*s
higher = decrease + p.mod
ranges.append(listing(vary(decrease, higher)))
for indices in product(*ranges):
area = ""
for index in indices:
area += pool[index*2:index*2 + 2]
area += ".bazar"
yield area
if __name__ == "__main__":
parser = argparse.ArgumentParser()
parser.add_argument(
"-d", "--date", assist="date used for seeding, e.g., 2020-06-28",
default=datetime.now().strftime('%Y-%m-%d'))
args = parser.parse_args()
d = datetime.strptime(args.date, "%Y-%m-%d")
for area in dga(d):
print(area)
Listed below are all of the domains for December 2020, January 2021, February 2021, and March 2021.
Traits
The next desk summarizes the properties of the brand new Bazar Loader DGA.
| property | worth |
|---|---|
| sort | TDD (time-dependent-deterministic) |
| era scheme | arithmetic |
| seed | present date |
| area change frequency | each month |
| distinctive domains per 30 days | 12996 |
| sequence | random choice, would possibly decide domains a number of occasions |
| wait time between domains | 10 seconds |
| high stage area | .bazar |
| second stage characters | a-z, with out j |
| regex | [a-ik-z]{8}.bazar |
| second stage area size | 8 |
[ad_2]


