[ad_1]
Microsoft lately launched a safety information replace that addresses chilling stories that attackers have been in a position to pivot from a check tenant to the C suite to acquire entry to emails being despatched and obtained. As well as, it got here to mild that HPE’s company mailboxes had been accessed utilizing an analogous exploit.
Each look like associated to a password spray assault in opposition to legacy electronic mail accounts that didn’t have multifactor authentication enabled. Let’s break down Microsoft’s put up and the way we are able to proactively forestall such assaults in our personal group.
Microsoft indicated that: “Midnight Blizzard [a Russian state-sponsored actor also known as NOBELIUM] utilized password spray assaults that efficiently compromised a legacy, non-production check tenant account that didn’t have multifactor authentication (MFA) enabled. In a password-spray assault, the adversary makes an attempt to signal into a big quantity of accounts utilizing a small subset of the preferred or more than likely passwords.”
Be sure multifactor authentication is enabled
One lesson to be realized from that is to make sure that multifactor authentication (MFA) is enabled on all the pieces and evaluate processes used for check accounts which have entry to your primary manufacturing Microsoft 365 tenant. Nowadays, MFA must be obligatory for any cloud service — don’t depend on only a password to guard any cloud asset.
In case your person base objects to MFA implementations, there are methods to make it extra palatable. With using conditional entry, you possibly can configure it such that MFA is just not mandated from a trusted location. However don’t get too complacent; if attackers achieve entry to a trusted location, conditional entry/whitelisting an IP handle to make sure your executives aren’t irritated with an MFA immediate might not be the way in which to go. Relying on the chance tolerance of your person base, it’s possible you’ll resolve that this coverage is just not smart.
Microsoft indicated that the assaults got here from IP addresses that didn’t seem dangerous. “The risk actor additional lowered the probability of discovery by launching these assaults from a distributed residential proxy infrastructure,” based on the replace. “These evasion strategies helped make sure the actor obfuscated their exercise and will persist the assault over time till profitable.”
Thus, regular defenses would haven’t flagged them as having come from dangerous places. You could want to contemplate putting in static IP addresses in residence settings for these people in your group more than likely to be focused by attackers. Using a static IP handle means you can establish and shield these accesses higher than mere residential residence IP addresses that will change over time.
Take note of the placement from which customers go online
Typically with an ISP it’s exhausting to find out the precise location from which a person is logging in. In the event that they entry from a cellphone, typically that geographic IP handle is in a serious metropolis many miles away out of your location. In that case, it’s possible you’ll want to arrange further infrastructure to relay their entry by a tunnel that’s higher protected and in a position to be examined. Don’t assume the dangerous guys will use a malicious IP handle to announce they’ve arrived at your door.
In accordance with Microsoft, “Midnight Blizzard leveraged their preliminary entry to establish and compromise a legacy check OAuth utility that had elevated entry to the Microsoft company setting. The actor created further malicious OAuth purposes.”
The attackers then created a brand new person account to grant consent within the Microsoft company setting to the actor-controlled malicious OAuth purposes. “The risk actor then used the legacy check OAuth utility to grant them the Workplace 365 Change On-line full_access_as_app position, which permits entry to mailboxes.”
That is the place my concern pivots from Microsoft’s lack of ability to proactively shield its processes to the bigger concern of our collective vulnerability in cloud implementations. Authentication has moved away from the standard username and password to application-based authentication that’s extra persistent. As well as, we frequently don’t perceive what we’re organising in a cloud setting and unintentionally depart permissions in such a state as to make it simpler for the attackers to achieve a foothold.
Configuring permissions to maintain management of entry parameters
Any person can create an app registration after which consent to graph permissions in addition to share any company knowledge. That you must arrange your tenant to require an utility administrator or cloud-application administrator to grant a person the fitting so as to add such a third-party OAuth-based app to the tenant somewhat than permitting customers to be self-service.
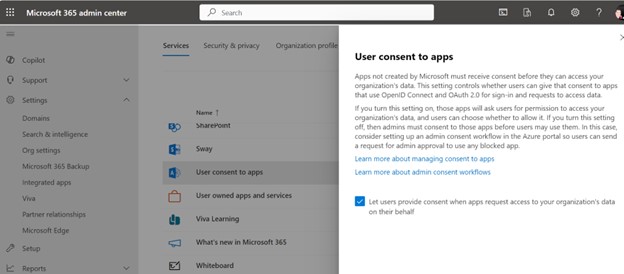
That is particularly the case in a company that manages delicate info of any form — all apps which might be added to the Microsoft 365 tenant must be manually accepted by an authorization course of. Within the Microsoft 365 Admin Middle choose Settings, then Org Settings, scroll all the way down to Consumer Consent to Apps.
Uncheck the field that enables customers to offer consent when apps request entry to your group’s knowledge on their behalf. You wish to vet purposes earlier than they get deployed to your customers. The method for the cloud isn’t any completely different.
Susan Bradley
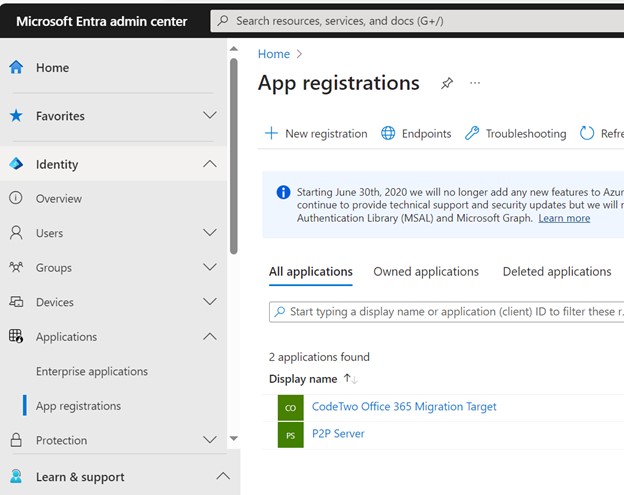
Subsequent go to Entra.microsoft.com in Utility Settings and search for App Registrations. Guarantee you may have recognized and acknowledged the purposes listed. Don’t panic when you see a P2PServer listed, it’s a placeholder of the primary AD joined machine. However vet and examine some other utility.
Susan Bradley
Subsequent, go into Consumer Settings and disable people who enable customers to register their very own purposes:
“Named Customers can register purposes” must be: No.
“Limit non-admin customers from creating tenants” must be: Sure.
“Customers can create safety teams” must be: No.
“Limit entry to the Microsoft Entra admin heart” must be: Sure.
You do need customers to submit admin consent requests when organising such an utility. Check the approval course of to make sure that the administrator you propose will get the immediate and vets the approval accordingly.
Make certain that any administrative person doesn’t register from a private machine. Make sure you at all times use a devoted secured machine for administrative work and no different machine.
Cloud purposes can grant doubtlessly harmful rights to customers
We now have inspired and used cloud purposes to make our lives simpler however they’ve additionally launched doubtlessly harmful rights. One other such position that could be abused within the AppRoleAssignment.ReadWrite.All MS Graph app position that bypasses the consent course of. This was by design and was meant for its implementation. Because of this, this app position is harmful when you don’t perceive the implications.
Too typically our builders and implementers have learn a weblog put up or used a advice with out actually understanding the dangers. Typically, we don’t return and audit how our cloud implementations are working, nor can we maintain a relentless evaluate of the altering defaults and introduction of latest safety defaults and options.
In mild of this case, you’ll wish to return and evaluate you probably have particularly assigned the AppRoleAssigment.ReadWrite.All that inadvertently gave greater privileges than you meant. A greater method to implement utility permissions is to keep away from utilizing this position and as a substitute use Consent Coverage.
The underside line is: don’t simply deploy new cloud applied sciences with out in search of cloud-hardening steerage as nicely. Evaluate the suggestions by CIS benchmarks, and different distributors that present Azure hardening recommendation. Don’t simply take the defaults supplied by the seller, clouds want hardening too — they don’t seem to be safe by default.
E-mail Safety, Risk and Vulnerability Administration, Vulnerabilities, Home windows Safety
[ad_2]


