[ad_1]
Knowledge loss prevention (DLP) greatest practices are ideas that assist stop intentional or unintentional knowledge erasure. By following these tips, organizations can scale back the detrimental affect of knowledge loss and shortly resume operations after an incident. This additionally protects delicate knowledge and minimizes authorized and reputational points. Discover some real-world cases under and uncover when and learn how to use DLP procedures for optimum knowledge safety.
When Ought to You Incorporate a DLP Technique?
If you happen to or your online business handles delicate knowledge, operates in regulated industries, or suffers from repeated cybersecurity threats, it’s time to judge the necessity for DLP methods. Proofpoint’s 2024 knowledge loss panorama report reveals 84.7% of enterprises have skilled knowledge loss, with a median of 15 incidents per firm per yr, underscoring the significance of correctly implementing DLP strategies. Take into account these elements:
- Delicate knowledge dealing with: Decide whether or not your organization handles prospects’ personally identifiable data (PII), proprietary software program code, product designs, or every other distinctive creations essential in your firm’s aggressive edge.
- Business-specific guidelines: Verify related rules regularly to confirm knowledge safety compliance, and use DLP to guard delicate knowledge and scale back regulatory dangers.
- Knowledge storage: Establish whether or not your group’s knowledge storage is on-premises or cloud-based. Analyze the storage’s safety protocols and scalability.
- Potential threats: Conduct threat assessments, vulnerability scans, and penetration testing to judge potential threats and weaknesses.
- Firm sources: Study your finances allocations and IT infrastructure capabilities. Decide whether or not there are sufficient monetary and expertise sources to undertake and maintain efficient DLP initiatives.
12 Knowledge Loss Prevention Greatest Practices
A knowledge loss prevention coverage lays the groundwork, however the effectiveness of knowledge safety hinges on adopting globally accepted greatest practices. These are values to be enforced and maintained, not simply duties to be accomplished. From tailoring your DLP coverage to selling a collaborative tradition contained in the group, discover these established practices for a stronger knowledge safety strategy.
Tailor Your DLP Coverage
This strategy begins with a radical examination of the varieties of knowledge that your online business handles. Categorize this knowledge in line with its sensitivity stage, taking into thoughts elements similar to confidentiality and regulatory compliance. Carry out a assessment of industry-specific guidelines to confirm compliance along with your coverage framework. Then, consider present community safety measures to find any gaps or redundancy that needs to be corrected.
By modifying your DLP coverage on this means, you may develop an efficient plan that meets your group’s particular necessities and improves general knowledge safety efforts. Aligning the coverage with {industry} rules reduces compliance dangers whereas avoiding potential penalties or authorized difficulties. Moreover, personalizing the coverage allows you to deal with threats and vulnerabilities particular to your online business.

Select the Proper DLP Answer
To decide on one of the best DLP answer, conduct intensive analysis on suppliers to find out their capabilities and compatibility along with your group’s necessities. Be sure that the instruments you buy are according to knowledge administration requirements, regulatory wants, and your monetary limits. To make an knowledgeable choice, consider options, scalability, and integration capabilities.
Take into account these prime three DLP merchandise:
- Forcepoint DLP: Greatest general possibility for visibility and international compliance (30-day free trial)
- Clumio Defend and Uncover: Greatest for AWS enterprise environments (14-day free trial)
- Proofpoint Enterprise DLP: Greatest for standalone electronic mail safety (contact free of charge trial)
Choosing the proper DLP answer ensures efficient knowledge safety, compliance with guidelines, and a diminished threat of knowledge breaches. It maximizes useful resource utilization by investing in merchandise that concentrate on particular safety wants, therefore bettering your group’s general cybersecurity posture.
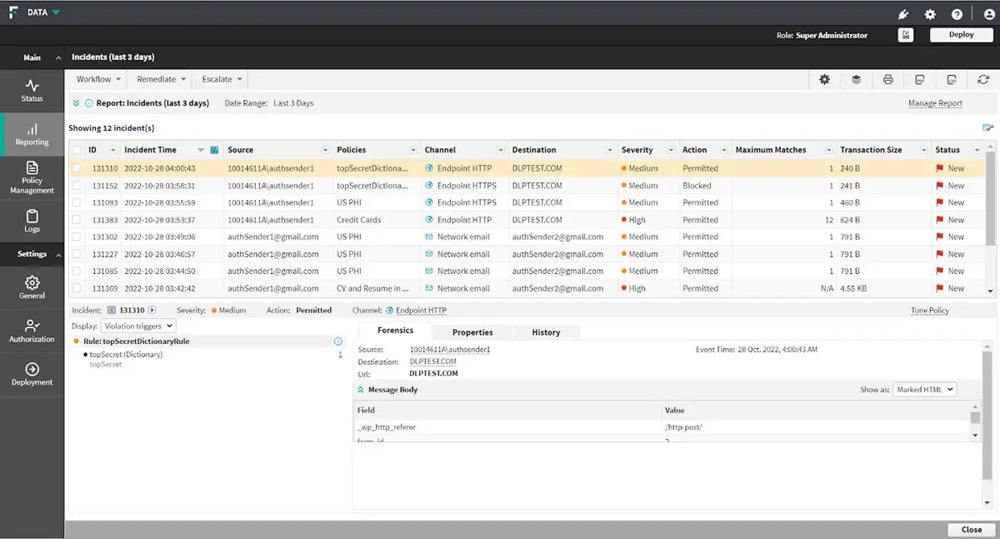
If you happen to’re on the lookout for extra choices, take a look at our complete information on the prime DLP options.
Prioritize & Classify Knowledge
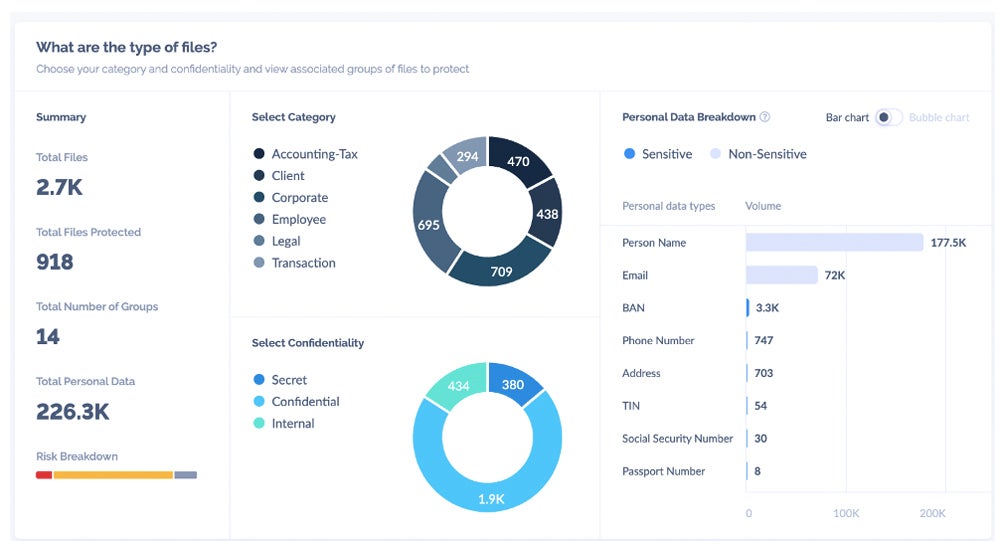
To efficiently prioritize and classify knowledge, perceive the regulatory necessities and potential penalties on delicate data. Decide important knowledge sorts, similar to mental property and private data, to steer protection sources the place they’re most required. Classify knowledge by context to make it simpler to handle and monitor. Conduct content material evaluation to enhance security measures.
This strategy allows centered protection methods, guaranteeing that sources are allotted effectively to safeguard crucial data. It simplifies knowledge administration operations and enhances monitoring capabilities, thus enhancing general knowledge safety posture. Periodic assessment permits companies to answer altering knowledge landscapes and rising threats whereas retaining robust safety measures over time.
Prepare Staff on Their Roles in Knowledge Safety
To provoke worker knowledge safety coaching, first look at the group’s specific threat panorama and regulatory necessities. Customise coaching supplies to handle these particular considerations, together with knowledge dealing with protocols, password administration, and phishing try identification. Use cybersecurity coaching instruments, seminars, on-line programs, and simulations to efficiently interact workers and reinforce basic community safety ideas.
Organizations that spend money on worker knowledge safety coaching can significantly mitigate the danger of knowledge breaches and reduce the potential penalties of safety incidents. Nicely-informed staff can higher establish and reply to safety threats. Moreover, adopting DLP methods alongside coaching actions improves the group’s potential to implement safety rules and detect suspicious conduct, consequently strengthening cybersecurity defenses.

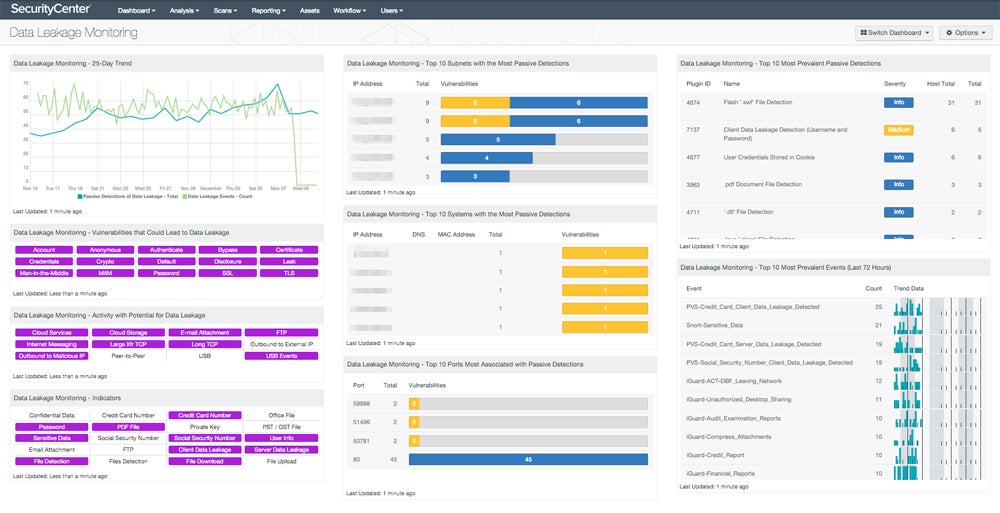
Use Monitoring Instruments for Knowledge Visibility
For continued knowledge visibility, start by deploying monitoring applied sciences that monitor knowledge journey throughout the group’s community. Decide the place knowledge originates, the way it’s saved, and the place it’s transported. Actual-time knowledge loss prevention methods repeatedly monitor knowledge flows, permitting companies to catch and react to any suspicious exercise or potential knowledge breaches.
As well as, regularly refining and modifying these monitoring methods reduces false alarms and assures exact detection of safety incidents. By conserving all saved knowledge seen, organizations could proactively detect and resolve doable safety considerations earlier than they develop into full-fledged knowledge breaches.
Restrict Knowledge Entry
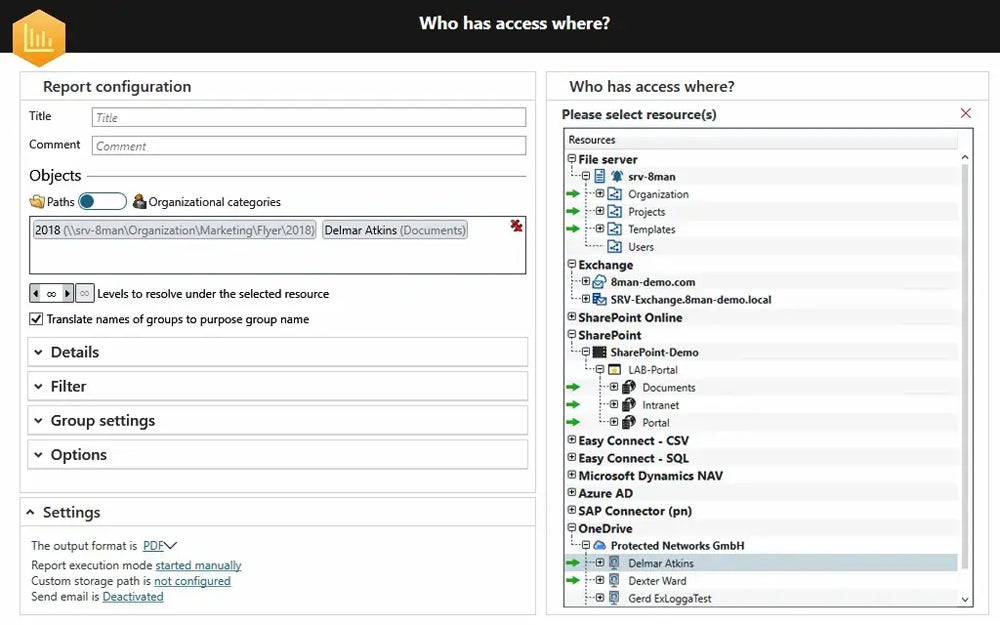
To scale back the hazard of unauthorized entry and breaches, this method adheres to the precept of least privilege, offering people entry to solely the data they want. Use entry restrictions and conduct common assessments to make sure that permissions are acceptable for the consumer’s job. Common audits, robust entry controls, and early permission revocations assist to restrict the dangers related to modifications in consumer intent.
Encrypt Knowledge
This follow entails utilizing knowledge encryption instruments to maintain delicate knowledge confidential and protected from unlawful entry or exploitation, even when the system is misplaced or stolen. Encrypt knowledge at relaxation with encryption algorithms and safe storage strategies. To encrypt knowledge in transit, make use of safe encryption and communication protocols similar to Transmission Management Protocol (TCP) and Transport Layer Safety (TLS).
Listed here are some choices for knowledge encryption instruments:
- 7-Zip: Greatest for worldwide use (free to obtain)
- AxCrypt: Greatest for Simplified Enterprise File Sharing (30-day free trial)
- NordLocker: Greatest for Cloud-Primarily based Enterprise File Sharing (14-day free trial)
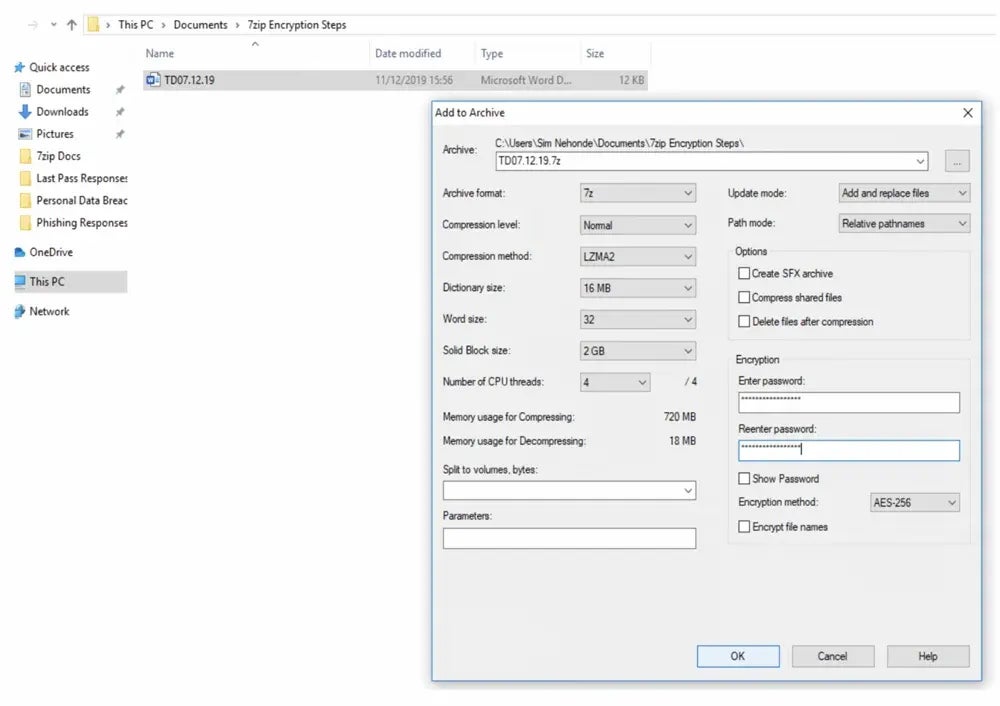
Discover different various options by studying our assessment on the greatest encryption software program and instruments.
Make use of Authentication Strategies for All Customers & Gadgets
A zero belief strategy rejects any kind of inherent belief and requires continuous verification of all customers and units. Implement stringent entry guidelines, multi-factor authentication, and steady monitoring to authenticate all entry makes an attempt, no matter prior belief standing. This technique examines all community site visitors and entry makes an attempt to cut back the chance of unauthorized entry or exploitation.
Implement the 3-2-1 Backup Rule
When making use of the 3-2-1 backup rule, ensure you have three copies of your knowledge: one major and two backups. Preserve these copies on two separate varieties of media: laborious disks, cloud storage, and tape backups. Then, preserve one duplicate offshore to guard in opposition to localized disasters similar to fires, floods, and theft.
A number of copies of knowledge on completely different media permit redundancy, decreasing the prospect of whole knowledge loss as a result of {hardware} failures or cyberattacks. Storing one copy offsite protects in opposition to disasters, guaranteeing that knowledge remains to be accessible even when the first location is compromised.

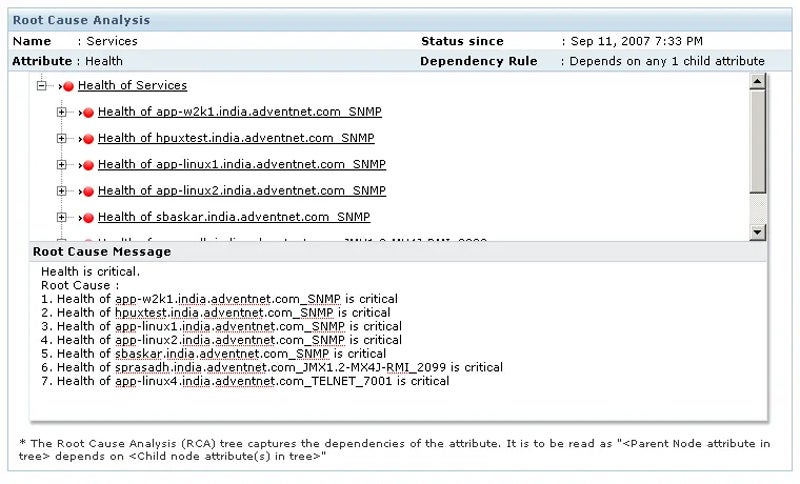
Use the 5-Whys Root Trigger Evaluation (RCA) Technique
To do that technique, establish the issue and ask “why” to disclose its underlying causes. Repeat the process iteratively, at the least 5 instances, delving deeper with every “why” till the underlying trigger is found. Then, create fixes that efficiently deal with the basis trigger. Use automation instruments that will help you carry out root trigger evaluation quicker.
This technique offers companies with higher insights into their difficulties, leading to simpler downside fixing. It encourages a radical analysis of issues, permitting groups to handle not simply the signs but in addition the basis causes. This technique additionally promotes a tradition of continuous growth, which prevents comparable issues from occurring sooner or later.
Overview & Refine the DLP Technique
To look at and modify your present DLP strategy, begin by securing important knowledge units and figuring out gaps. Develop knowledge identification efforts and be sure that DLP options are often up to date to counter rising dangers. Conduct safety audits to evaluate controls and detect flaws, after which prioritize corrective actions. Use the teachings realized to find out the long run enhancements required to guard in opposition to knowledge loss threats.
Improve Collaboration Amongst Inside Customers
Contain all stakeholders within the group’s knowledge safety actions. Everybody, from senior administration to front-line workers, is accountable for sustaining a radical knowledge safety coverage. Encourage common talks, coaching, and consciousness workshops to assist combine DLP practices into the group’s tradition. An efficient DLP implementation requires participation and cooperation from all customers to efficiently meet the corporate targets and necessities.
3 Actual Examples of DLP Greatest Practices in Motion
DLP is extra than simply principle; lapses in DLP can lead to disastrous penalties. Knowledge loss threats have endured over time, as evidenced by incidents such because the Cloudflare breach in 2023, GitLab’s database failure in 2017, and the Toy Story incident in 1998. Analyzing previous knowledge loss occurrences means that you can assess the severity of potential dangers and the effectiveness of their current DLP measures. Discover these real-life examples for added insights.
Cloudflare’s Thanksgiving Cyberattack
Incident: On Thanksgiving 2023, an intruder exploited stolen credentials to get entry to Cloudflare’s Atlassian server, attempting to infiltrate their international infrastructure. Regardless of gaining access to inside paperwork, Cloudflare’s Zero Belief structure prevented extra community traversals and knowledge compromise. No consumer knowledge was misplaced. Cloudflare responded by rotating greater than 5,000 manufacturing credentials, triaging 4,893 computer systems, and changing {hardware} in a brand new knowledge heart.
DLP greatest follow: Zero belief structure — Cloudflare’s Zero Belief expertise halted the attacker’s makes an attempt to take advantage of compromised credentials by prohibiting lateral motion and proscribing entry, stopping knowledge breaches and minimizing harm.
GitLab’s 300 GB Knowledge Loss
Incident: In 2017, GitLab skilled an 18-hour outage brought on by a database sync failure. Engineers tried guide re-sync, mistaking it for a spam assault and by chance dropping 300GB of current consumer knowledge, which affected tasks, feedback, and new accounts.
DLP greatest follow: GitLab’s emphasis on common database safety practices like backups and catastrophe restoration processes helps to cut back the affect of knowledge loss. Regardless of preliminary difficulties, a latest database snapshot saved throughout an engineer’s testing enabled the immediate restoration of misplaced knowledge.
Toy Story 2’s Unintentional File Deletion
Incident: Throughout a file cleanup, Toy Story 2’s database repository was put in danger when an animator by chance deleted Toy Story 2’s root folder, erasing all of the film’s knowledge. Fortunately, a technical director salvaged the movie as she had backup copies of the repository on her personal laptop. Whereas newer, unbacked information have been misplaced, main parts have been recovered, saving the challenge from cancellation or the necessity to begin over.
DLP greatest follow: Common backup and immutable storage options — whereas backup copies spared the Toy Story 2 challenge from catastrophe, newer information have been misplaced as a result of a scarcity of backups. Implementing the 3-2-1 backup method, which included redundant copies on completely different mediums, might have prevented knowledge loss. Moreover, utilizing an immutable storage answer would’ve saved all of the information intact.
Find out how to Implement a Knowledge Loss Prevention Technique in 5 Steps
To stop unlawful knowledge entry or leakage, efficient DLP methods should embrace a clearly outlined scope, knowledge safety consciousness and governance efforts, use circumstances mapping, dependencies identification and enchancment, and a gradual DLP implementation. This enables enterprises to guard their belongings, adjust to legal guidelines, and scale back dangers to their fame and operations.
1. Outline the Program’s Scope
To find out this system’s scope, prioritize dangers, and establish knowledge that wants safety, similar to mental property. Knowledge stream mapping means that you can hint knowledge origins, locations, and functions. To successfully assist this system, undertake safety insurance policies which might be according to DLP goals. This ensures tailor-made safety, minimal disruptions, and efficient alignment of safety measures with enterprise goals.
2. Provoke Consciousness & Governance Efforts
Talk knowledge practices, advantages, and penalties to all stakeholders. Refine knowledge dealing with processes by establishing acceptable norms and procedures. Then, work with the authorized and procurement groups to incorporate DLP necessities in contracts. Preserve open communication traces through a collaborative platform for continuous buyer enter and queries, supporting steady iteration as enterprise calls for change.
3. Map Your DLP Use Instances
First, decide the exact detection and context wants for every location. Then, resolve what varieties of DLP instruments are required to supply the required management. As a result of one supplier could not cowl all DLP parts, choose distributors who can safe knowledge throughout a number of recognized use circumstances, or combine it with different instruments. Earlier than choosing an answer, totally check it to confirm that it meets the wants of the enterprise and is efficient.
4. Deal with & Enhance Recognized Dependencies
Dependencies, whether or not technical or procedural, can scale back DLP efficacy. For instance, DLP suffers when customers have uncontrolled knowledge entry. Implement identification administration practices to restrict entry to knowledge primarily based on legitimate enterprise necessities. Moreover, make use of knowledge categorization to detect delicate knowledge and inform knowledge permissions, thereby bettering general DLP efficacy and knowledge safety.
5. Implement in Small Phases, Handle & Refine Over Time
To attenuate disturbance throughout large-scale rollouts, begin DLP implementation regularly, with a “monitoring solely” section to regulate insurance policies. Talk progress to customers, specializing in knowledge dealing with modifications. Transition to operational mode and gather metrics similar to resolved incidents and blocked knowledge cases to make sure continuous growth. Allocate sources to switch DLP insurance policies to satisfy evolving enterprise calls for and knowledge sorts.
Backside Line: Safe Your Operations with Knowledge Loss Prevention Greatest Practices
DLP greatest practices contain steady and proactive administration of knowledge safety. Organizations can accomplish complete knowledge safety by integrating these ideas into their on a regular basis operations. Constantly monitor, consider, and alter these methods as your organizational calls for change. To maintain knowledge safe, have a robust cybersecurity posture that entails a mixture of DLP and different varieties of safety options.
Combine DLP with safe storage and backup options for complete knowledge safety.
[ad_2]


