[ad_1]
Posted on
by
Joshua Lengthy

In Could and September 2023, we wrote about earlier variants of Atomic Stealer. This malware—often known as Atomic macOS Stealer or AMOS for brief—is designed to exfiltrate delicate information from contaminated Macs. It’s distributed within the type of Trojan horses, reminiscent of pirated or “cracked” variations of apps.
This week, stories have emerged of two completely different new variants of Atomic Stealer. Right here’s every part it is advisable to learn about them and easy methods to keep protected.
Atomic Stealer distributed via malicious Google Advertisements
One of many new Atomic Stealer variants, described by Jérôme Segura, has been confirmed to be distributed within the wild through Google Advertisements poisoning. A risk actor paid Google for high placement, with sponsored adverts that mimicked the true adverts of the Notion productiveness software program. These adverts appeared instantly above the precise search outcomes; for those who weren’t cautious, you would have inadvertently visited a malware distribution web site as a substitute of touchdown on the true software program developer’s web site.
If a sufferer clicked on a hyperlink within the malicious advert, they might be redirected to a faux Notion homepage which might supply Mac or Home windows malware disguised as Notion software program. The Home windows malware was a stealer referred to as Rhadamanthys, and the Mac malware was a brand new Atomic Stealer variant.

An OSX/AtomicStealer Computer virus, masquerading as Notion productiveness software program.
Notably, this Atomic Stealer variant has very low detection on the multi-engine single file scanning web site VirusTotal; solely 6 out of 60 engines detect it, whereas different variants (like those described beneath) sometimes have not less than 20 detections.
A second variant disguised as a “Crack Installer”
One other variant, described by Andrei Lapusneanu, disguises itself as an unspecified “Crack Installer.” If a sufferer follows the instructions from the disk picture, and does a “proper click on” and clicks Open, a Mach-O app runs. Like with the primary variant, this app is a dropper, which means it can try to obtain and execute an extra stage of the malware.
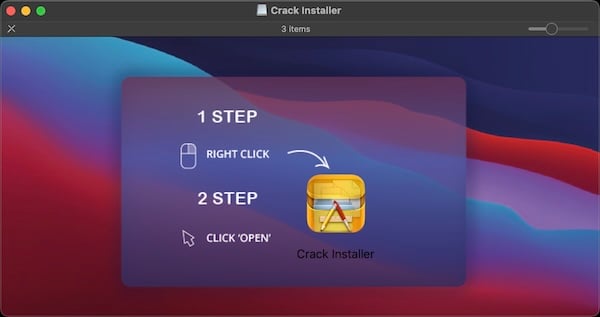
One other OSX/AtomicStealer Trojan, disguised as a “Crack Installer”
The following stage is a Python script that does all the standard issues one expects stealer malware to do; it makes an attempt to collect and exfiltrate browser information reminiscent of saved passwords, cookies, autofill textual content, and cryptocurrency wallets. It makes use of AppleScript code just like that utilized in RustDoor malware seen earlier in February. This Atomic Stealer variant makes an attempt to ship the stolen information to an IP handle that has beforehand been linked to Home windows malware referred to as Amadey.
How can I maintain my Mac secure from malware?
For those who use Intego VirusBarrier, you’re shielded from this malware. Intego detects these samples as OSX/Stealer.ext, virus/OSX/Agent.mysf, virus/OSX/AVA.Agent.amos, virus/OSX/AVF.Agent.tfcg, virus/OSX/AVI.Agent.dkaa, and related names.
 Intego VirusBarrier X9, included with Intego’s Mac Premium Bundle X9, is a strong answer designed to guard in opposition to, detect, and remove Mac malware.
Intego VirusBarrier X9, included with Intego’s Mac Premium Bundle X9, is a strong answer designed to guard in opposition to, detect, and remove Mac malware.
For those who consider your Mac could also be contaminated, or to forestall future infections, it’s finest to make use of antivirus software program from a trusted Mac developer. VirusBarrier is award-winning antivirus software program, designed by Mac safety consultants, that features real-time safety. It runs natively on each Intel- and Apple silicon-based Macs, and it’s appropriate with Apple’s present Mac working system, macOS Sonoma.
For those who use a Home windows PC, Intego Antivirus for Home windows can maintain your pc shielded from malware.
How can I study extra?
For added technical particulars and indicators of compromise (IOCs) for these Atomic Stealer variants, you may learn Jérôme Segura’s write-up and social media publish, and Andrei Lapusneanu’s write-up.
We mentioned the resurgence of Atomic Stealer—in addition to Google’s regarding ineptitude at stopping overt copycat adverts that hyperlink to malware websites—on episode 333 of the Intego Mac Podcast.
Make sure to additionally take a look at our 2024 Apple malware forecast and our earlier Mac malware articles from 2024 and earlier.
 Every week on the Intego Mac Podcast, Intego’s Mac safety consultants focus on the most recent Apple information, together with safety and privateness tales, and supply sensible recommendation on getting probably the most out of your Apple units. Make sure to comply with the podcast to be sure you don’t miss any episodes.
Every week on the Intego Mac Podcast, Intego’s Mac safety consultants focus on the most recent Apple information, together with safety and privateness tales, and supply sensible recommendation on getting probably the most out of your Apple units. Make sure to comply with the podcast to be sure you don’t miss any episodes.
It’s also possible to subscribe to our e-mail publication and maintain an eye fixed right here on The Mac Safety Weblog for the most recent Apple safety and privateness information. And don’t neglect to comply with Intego in your favourite social media channels: ![]()
![]()
![]()
![]()
![]()
![]()
![]()
About Joshua Lengthy
Joshua Lengthy (@theJoshMeister), Intego’s Chief Safety Analyst, is a famend safety researcher, author, and public speaker. Josh has a grasp’s diploma in IT concentrating in Web Safety and has taken doctorate-level coursework in Data Safety. Apple has publicly acknowledged Josh for locating an Apple ID authentication vulnerability. Josh has performed cybersecurity analysis for greater than 25 years, which has usually been featured by main information retailers worldwide. Search for extra of Josh’s articles at safety.thejoshmeister.com and comply with him on Twitter/X, LinkedIn, and Mastodon.
View all posts by Joshua Lengthy →
[ad_2]


