[ad_1]
Malicious hackers are concentrating on individuals within the cryptocurrency area in assaults that begin with a hyperlink added to the goal’s calendar at Calendly, a preferred utility for scheduling appointments and conferences. The attackers impersonate established cryptocurrency buyers and ask to schedule a video convention name. However clicking the assembly hyperlink offered by the scammers prompts the person to run a script that quietly installs malware on macOS programs.
KrebsOnSecurity not too long ago heard from a reader who works at a startup that’s searching for funding for constructing a brand new blockchain platform for the Internet. The reader spoke provided that their title not be used on this story, so for the sake of simplicity we’ll name him Doug.
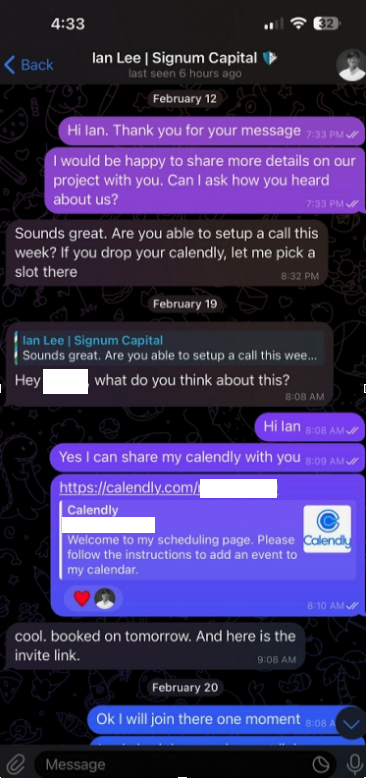
Being within the cryptocurrency scene, Doug can be energetic on the moment messenger platform Telegram. Earlier this month, Doug was approached by somebody on Telegram whose profile title, picture and outline stated they have been Ian Lee, from Signum Capital, a well-established funding agency primarily based in Singapore. The profile additionally linked to Mr. Lee’s Twitter/X account, which options the identical profile picture.
The investor expressed curiosity in financially supporting Doug’s startup, and requested if Doug might make time for a video name to debate funding prospects. Positive, Doug stated, right here’s my Calendly profile, e book a time and we’ll do it then.
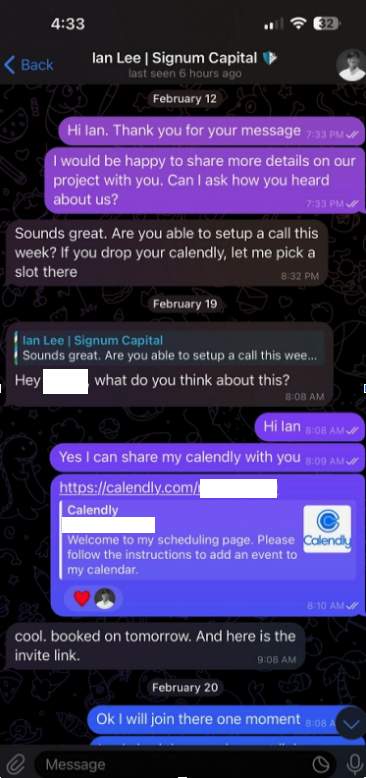
When the day and time of the scheduled assembly with Mr. Lee arrived, Doug clicked the assembly hyperlink in his calendar however nothing occurred. Doug then messaged the Mr. Lee account on Telegram, who stated there was some sort of expertise situation with the video platform, and that their IT individuals urged utilizing a special assembly hyperlink.
Doug clicked the brand new hyperlink, however as an alternative of opening up a videoconference app, a message appeared on his Mac saying the video service was experiencing technical difficulties.
“A few of our customers are dealing with points with our service,” the message learn. “We’re actively engaged on fixing these issues. Please discuss with this script as a brief answer.”
Doug stated he ran the script, however nothing appeared to occur after that, and the videoconference utility nonetheless wouldn’t begin. Mr. Lee apologized for the inconvenience and stated they must reschedule their assembly, however he by no means responded to any of Doug’s follow-up messages.
It didn’t daybreak on Doug till days later that the missed assembly with Mr. Lee may need been a malware assault. Going again to his Telegram consumer to revisit the dialog, Doug found his potential investor had deleted the assembly hyperlink and different bits of dialog from their shared chat historical past.
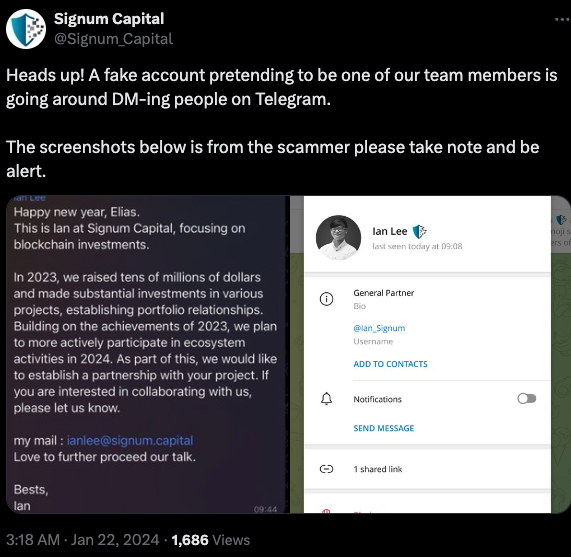
In a publish to its Twitter/X account final month, Signum Capital warned {that a} faux profile pretending to be their worker Mr. Lee was attempting to rip-off individuals on Telegram.
The file that Doug ran is an easy Apple Script (file extension “.scpt”) that downloads and executes a malicious trojan made to run on macOS programs. Sadly for us, Doug freaked out after deciding he’d been tricked — backing up his essential paperwork, altering his passwords, after which reinstalling macOS on his laptop. Whereas this a superbly sane response, it means we don’t have the precise malware that was pushed to his Mac by the script.
However Doug does nonetheless have a replica of the malicious script that was downloaded from clicking the assembly hyperlink (the net host serving that hyperlink is now offline). A search in Google for a string of textual content from that script turns up a December 2023 weblog publish from cryptocurrency safety agency SlowMist about phishing assaults on Telegram from North Korean state-sponsored hackers.
“When the challenge group clicks the hyperlink, they encounter a area entry restriction,” SlowMist wrote. “At this level, the North Korean hackers coax the group into downloading and operating a ‘location-modifying’ malicious script. As soon as the challenge group complies, their laptop comes beneath the management of the hackers, resulting in the theft of funds.”
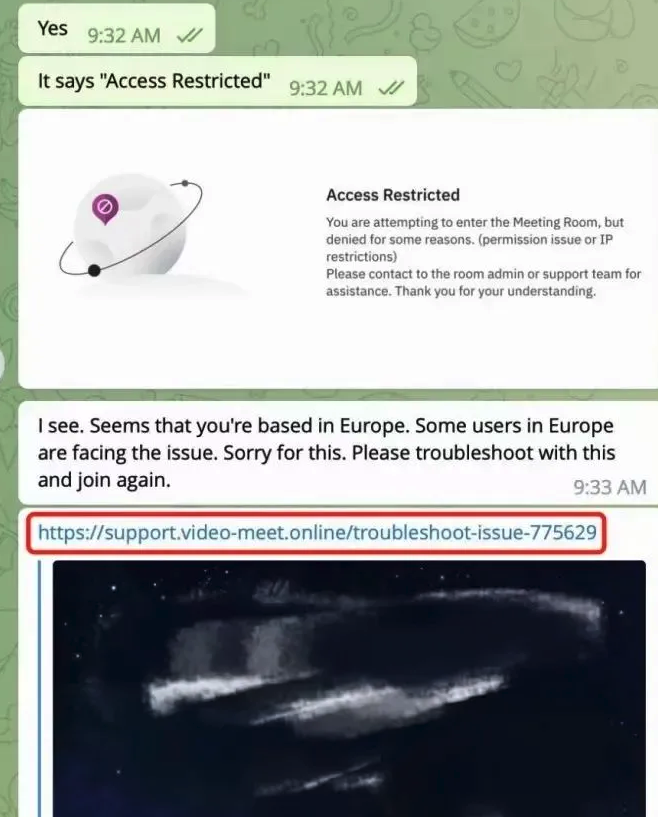
Picture: SlowMist.
SlowMist says the North Korean phishing scams used the “Add Customized Hyperlink” function of the Calendly assembly scheduling system on occasion pages to insert malicious hyperlinks and provoke phishing assaults.
“Since Calendly integrates nicely with the every day work routines of most challenge groups, these malicious hyperlinks don’t simply increase suspicion,” the weblog publish explains. “Consequently, the challenge groups might inadvertently click on on these malicious hyperlinks, obtain, and execute malicious code.”
SlowMist stated the malware downloaded by the malicious hyperlink of their case comes from a North Korean hacking group dubbed “BlueNoroff, which Kaspersky Labs says is a subgroup of the Lazarus hacking group.
“A financially motivated risk actor carefully linked with Lazarus that targets banks, casinos, fin-tech corporations, POST software program and cryptocurrency companies, and ATMs,” Kaspersky wrote of BlueNoroff in Dec. 2023.
The North Korean regime is thought to make use of stolen cryptocurrencies to fund its army and different state tasks. A current report from Recorded Future finds the Lazarus Group has stolen roughly $3 billion in cryptocurrency over the previous six years.
Whereas there’s nonetheless way more malware on the market at present concentrating on Microsoft Home windows PCs, the prevalence of information-stealing trojans aimed toward macOS customers is rising at a gradual clip. MacOS computer systems embrace X-Defend, Apple’s built-in antivirus expertise. However specialists say attackers are continually altering the looks and habits of their malware to evade X-Defend.
“Current updates to macOS’s XProtect signature database point out that Apple are conscious of the issue, however early 2024 has already seen a variety of stealer households evade identified signatures,” safety agency SentinelOne wrote in January.
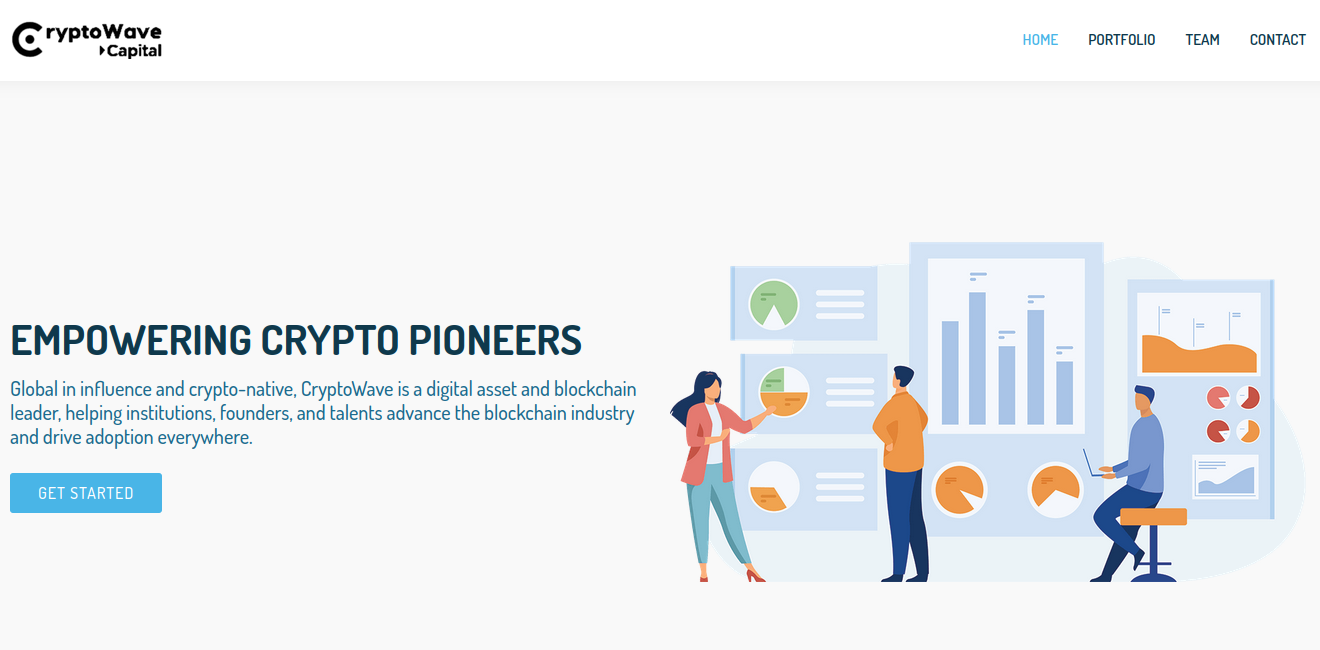
In keeping with Chris Ueland from the risk looking platform Hunt.io, the Web tackle of the faux assembly web site Doug was tricked into visiting (104.168.163,149) hosts or very not too long ago hosted about 75 completely different domains, a lot of which invoke phrases related to videoconferencing or cryptocurrency. These domains point out this North Korean hacking group is hiding behind a variety of phony crypto corporations, just like the six-month-old web site for Cryptowave Capital (cryptowave[.]capital).
In an announcement shared with KrebsOnSecurity, Calendly stated it was conscious of a majority of these social engineering assaults by cryptocurrency hackers.
“To assist stop these sorts of assaults, our safety group and companions have carried out a service to mechanically detect fraud and impersonations that might result in social engineering,” the corporate stated. “We’re additionally actively scanning content material for all our clients to catch a majority of these malicious hyperlinks and to stop hackers earlier on. Moreover, we intend so as to add an interstitial web page warning customers earlier than they’re redirected away from Calendly to different web sites. Together with the steps we’ve taken, we suggest customers keep vigilant by conserving their software program safe with operating the most recent updates and verifying suspicious hyperlinks by way of instruments like VirusTotal to alert them of potential malware. We’re constantly strengthening the cybersecurity of our platform to guard our clients.”
The growing frequency of recent Mac malware is an effective reminder that Mac customers shouldn’t rely on safety software program and instruments to flag malicious information, that are ceaselessly bundled with or disguised as legit software program.
As KrebsOnSecurity has suggested Home windows customers for years, a great rule of security to reside by is that this: For those who didn’t go searching for it, don’t set up it. Following this mantra heads off a substantial amount of malware assaults, whatever the platform used. While you do resolve to put in a bit of software program, be sure to are downloading it from the unique supply, after which hold it up to date with any new safety fixes.
On that final entrance, I’ve discovered it’s a good suggestion to not wait till the final minute to configure my system earlier than becoming a member of a scheduled videoconference name. Even when the decision makes use of software program that’s already on my laptop, it’s usually the case that software program updates are required earlier than this system can be utilized, and I’m a type of bizarre individuals who likes to assessment any adjustments to the software program maker’s privateness insurance policies or person agreements earlier than selecting to put in updates.
Most of all, confirm new contacts from strangers earlier than accepting something from them. On this case, had Doug merely messaged Mr. Lee’s actual account on Twitter/X or contacted Signum Capital instantly, he would found that the actual Mr. Lee by no means requested for a gathering.
For those who’re approached in an analogous scheme, the response from the would-be sufferer documented within the SlowMist weblog publish might be the most effective.
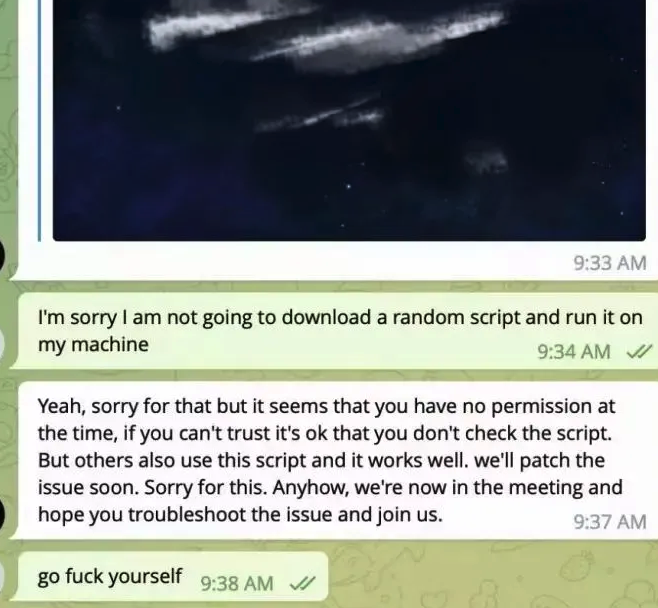
Picture: SlowMist.
Replace: Added remark from Calendly.
[ad_2]