[ad_1]
Over the previous few years, containers have emerged as a cornerstone expertise, enabling scalability, effectivity, and constant environments throughout growth, testing, and manufacturing. Nonetheless, the rise of containers has additionally launched new safety challenges, notably round managing vulnerabilities that may compromise your complete utility stack.
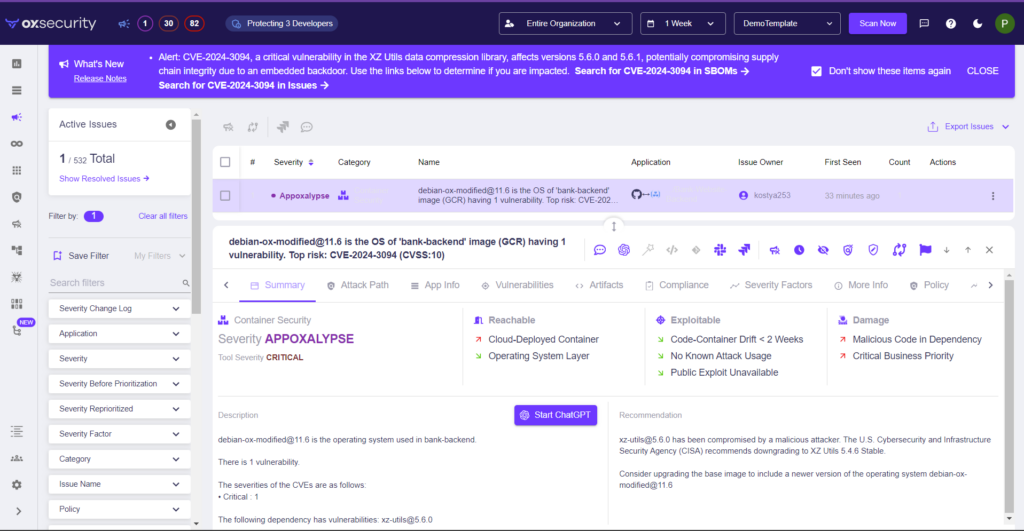
By now, you’ve heard concerning the discovery of malicious code embedded in XZ Utils variations 5.6.0 and 5.6.1, recognized beneath CVE-2024-3094. Given XZ Utils’ widespread utilization for compression and decompression in Linux distributions, the vulnerability primarily threatens container pictures relatively than user-side code. This incident underscores the essential significance of container safety/scanning at the side of lively utility safety posture administration (ASPM) in safeguarding in opposition to such vulnerabilities.
Bridging the Hole with Contextual Evaluation
One key benefit of integrating Container scanning along with your AppSec practices is the flexibility to carry out contextual evaluation. This course of hyperlinks container vulnerabilities immediately again to the supply code, shedding mild on the place an issue lies, who launched it, and the way it may be successfully remediated. By making a direct linkage between container points and supply code vulnerabilities, organizations can bridge the hole between container safety and code-level points, making vulnerabilities extra actionable and remediation extra exact.
Streamlined Triage and Prioritization
Containers, by their nature, inherit severity elements and different attributes from their corresponding code repositories. This relationship permits for a extra nuanced evaluation of danger, factoring in components similar to container drift, the utilization of weak features, and the general affect of the problem. Moreover, with Energetic ASPM there customers entry reachability evaluation which permits the platform to know {that a} container is deployed and create an assault path from cloud to code. Because of this, prioritization relies on a complete visibility into the vulnerability context, together with its origins within the code. This streamlined method to triage and prioritization ensures that efforts are targeted on essentially the most essential vulnerabilities based mostly on their severity and the context during which they exist.
Automating the Response to Vulnerabilities
Integrating Container scanning with Energetic ASPM affords a transparent path from vulnerability identification to decision, enabling organizations to automate the triage and prioritization course of. Automation on this context covers figuring out the place fixes have to be utilized, who’s answerable for them, and the precise actions required to remediate points. This degree of automation considerably reduces guide effort, accelerates response occasions, and enhances the general safety posture of the appliance stack.
Addressing Key Challenges
Handbook Triage Work
Historically, figuring out a vulnerability inside a container concerned an in depth guide effort to hint it again to its supply code origins. This proved time-consuming and sometimes required extra precision to know the problem’s true severity and context totally. The combination of Container scanning addresses this problem by offering an automatic, correct linkage between container vulnerabilities and the corresponding supply code, enhancing each effectivity and efficacy in vulnerability administration.
Actionability of Points
Safety instruments usually overwhelm customers with many points that want actionable insights. That is notably true for vulnerabilities which can be a part of a base picture and never immediately tied to the appliance code. By establishing a direct connection between container points and the code, vulnerabilities evolve from alerts to actionable gadgets with clear paths to decision, enhancing the actionability of safety insights.
Siloed Safety Practices
The complexity of containers extends past technical challenges, as a number of groups contribute to the code: from DevOps, who construct the bottom picture and supply person directions, to builders, who commit the appliance code, underscoring the multifaceted nature of container safety.
Regardless of this container safety has historically operated in isolation from the broader utility safety context. This siloed method has led to missed alternatives for holistic danger administration. The combination of Container scanning with Energetic ASPM breaks down these silos, fostering a extra built-in and sensible method to managing safety dangers throughout your complete utility stack.
Conclusion
The combination of container scanning marks a big development within the discipline of vulnerability administration. Organizations can improve their safety posture in a panorama more and more dominated by containerized functions by offering contextual evaluation, streamlining triage and prioritization, and automating the response to vulnerabilities. Breaking down the silos between container safety and supply code evaluation paves the best way for a extra complete, environment friendly, and sensible method to securing functions in opposition to the ever-evolving risk panorama.
Begin a free trial in the present day to strive container scanning within the OX Energetic ASPM Platform.
The submit Container Scanning: A Path to Enhanced Vulnerability Administration appeared first on OX Safety.
*** This can be a Safety Bloggers Community syndicated weblog from OX Safety authored by Melissa Goldberger. Learn the unique submit at: https://www.ox.safety/container-scanning-a-path-to-enhanced-vulnerability-management/
[ad_2]