[ad_1]
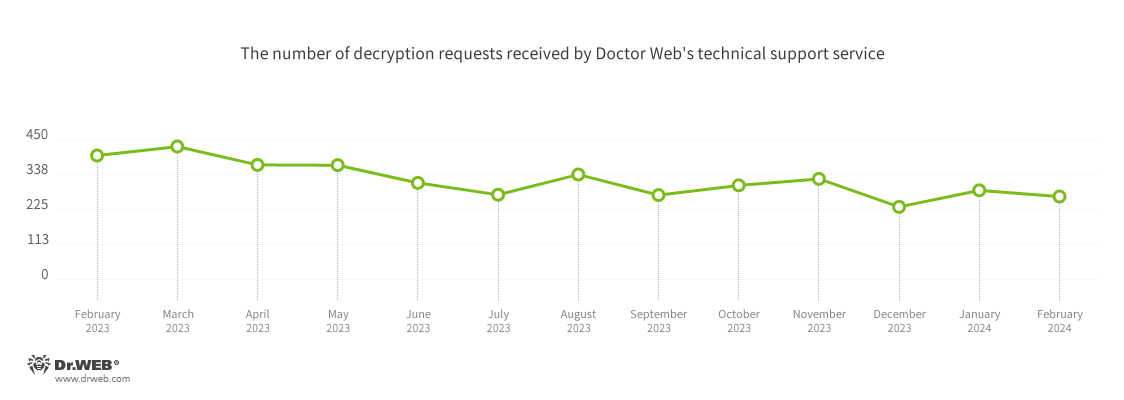
The variety of consumer requests to decrypt recordsdata affected by encoder trojans decreased by 7.02%, in comparison with the earlier month. The most typical malware behind the ransom assaults had been Trojan.Encoder.3953 (18.27% of incidents), Trojan.Encoder.37369 (9.14% of incidents), and Trojan.Encoder.26996 (8.12% of incidents).
Within the cellular threats division, Android.HiddenAds adware trojans had been once more probably the most generally detected malware, with extremely elevated exercise.
Principal developments in February
- A rise within the complete variety of threats detected
- The predominance of malicious scripts and phishing paperwork in malicious electronic mail visitors
- A lower within the variety of consumer requests to decrypt recordsdata affected by encoder trojans
- A rise within the variety of Android.HiddenAds adware trojans on protected units
Based on Physician Net’s statistics service
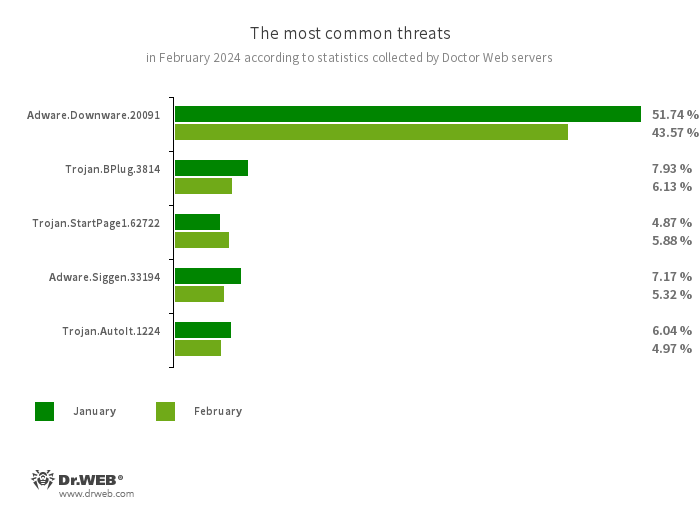
The most typical threats in February:
- Adware.Downware.20091
- Adware that always serves as an middleman installer of pirated software program.
- Trojan.BPlug.3814
- The detection identify for a malicious part of the WinSafe browser extension. This part is a JavaScript file that shows intrusive advertisements in browsers.
- Trojan.StartPage1.62722
- A computer virus that may modify the house web page within the browser settings.
- Adware.Siggen.33194
- The detection identify for a freeware browser that was created with an Electron framework and has a built-in adware part. This browser is distributed through varied web sites and loaded onto customers’ computer systems once they strive downloading torrent recordsdata.
- Trojan.AutoIt.1224
- The detection identify for a packed model of the Trojan.AutoIt.289 malicious app, written within the AutoIt scripting language. This trojan is distributed as a part of a gaggle of a number of malicious functions, together with a miner, a backdoor, and a self-propagating module. Trojan.AutoIt.289 performs varied malicious actions that make it tough for the principle payload to be detected.
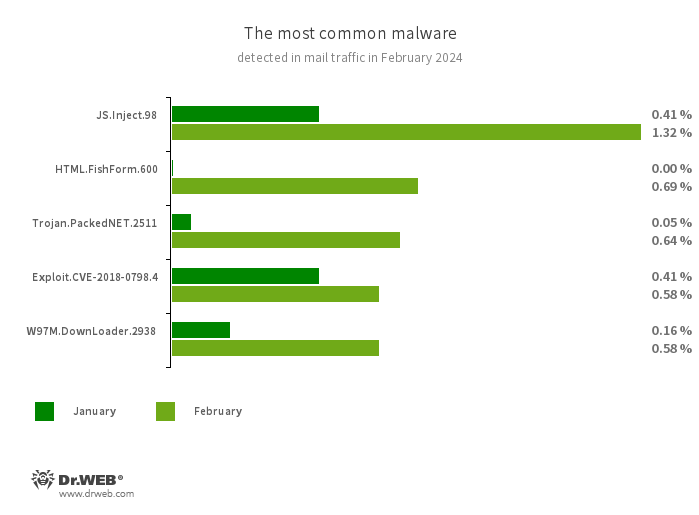
Statistics for malware found in electronic mail visitors
- JS.Inject
- A household of malicious JavaScripts that inject a malicious script into the HTML code of webpages.
- HTML.FishForm.365
- A webpage unfold through phishing emails. It’s a bogus authorization web page that mimics well-known web sites. The credentials a consumer enters on the web page are despatched to the attacker.
- Trojan.PackedNET.2511
- Malware written in VB.NET and guarded with a software program packer.
- Exploit.CVE-2018-0798.4
- An exploit designed to benefit from Microsoft Workplace software program vulnerabilities and permit an attacker to run arbitrary code.
- W97M.DownLoader.2938
- A household of downloader trojans that exploit vulnerabilities in Microsoft Workplace paperwork. They’ll additionally obtain different malicious packages to a compromised laptop.
Encryption ransomware
In February 2024, the variety of requests made to decrypt recordsdata affected by encoder trojans decreased by 7.02%, in comparison with January.
The most typical encoders of February:
- Trojan.Encoder.3953 — 18.27%
- Trojan.Encoder.35534 — 9.14%
- Trojan.Encoder.26996 — 8.12%
- Trojan.Encoder.29750 — 0.51%
- Trojan.Encoder.37400 — 0.51%
Harmful web sites
In February 2024, Physician Net’s Web analysts continued to establish undesirable web sites of assorted material. For instance, websites informing potential victims that some cash transfers had been allegedly ready for them had been standard with cybercriminals. To “obtain” these funds, customers should pay a financial institution switch “fee”. Hyperlinks to such web sites are distributed in varied methods, together with through posts on the Telegraph weblog platform.
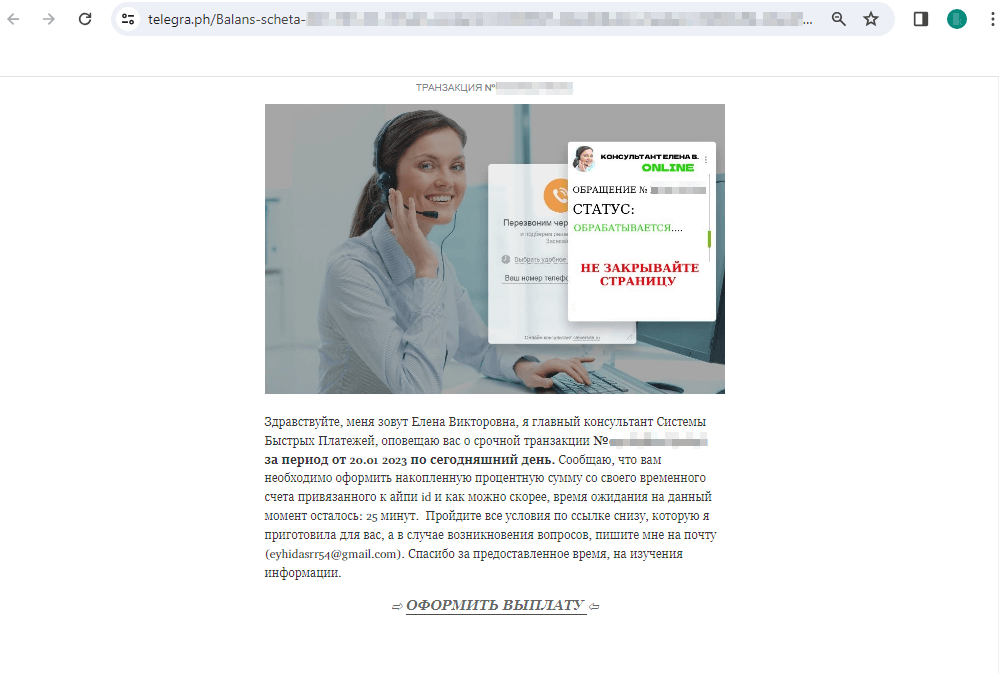
Under is an instance of 1 such publication. Potential victims are requested to “gather” the reward that they supposedly earned after taking part in a web-based retailer survey:
Upon clicking on the “GET A PAYMENT” (“ОФОРМИТЬ ВЫПЛАТУ”) hyperlink, the consumer is redirected to a rip-off web site of some non-existent “Worldwide Fee and Switch System” (“Международная Система Платежей и Переводов”), the place they’re supposedly capable of obtain the promised funds:
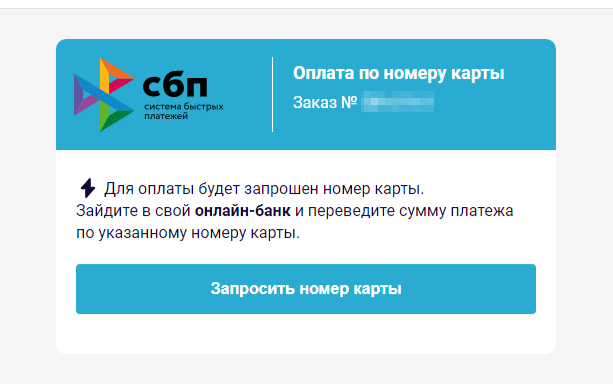
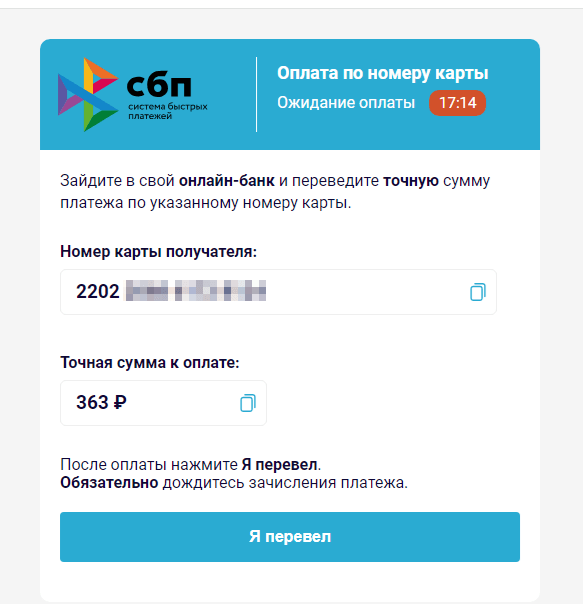
To “obtain” the cash, the consumer should first present private info, similar to their identify and electronic mail handle. Then, they should pay a “fee” through the official Sooner Funds System (“Система быстрых платежей”, “СБП”, or “SBP”) in order that the reward, which, the truth is, doesn’t exist, could be “transferred” to them. On the similar time, scammers ask the sufferer to pay the “fee” through a web-based financial institution, utilizing the desired financial institution card quantity; all that whereas, the Sooner Funds System permits transfers solely by cell phone quantity. On this case, the fraudsters might intentionally be speculating on a money-transfer technique that’s gaining reputation in Russia, relying on the low monetary literacy of customers. If the sufferer agrees to pay the “fee”, they’ll switch their very own cash on to the scammers’ financial institution card. Nonetheless, it’s potential that in an try to steal customers’ cash, malicious actors will really start utilizing the Sooner Funds System sooner or later.
Malicious and undesirable packages for cellular units
Based on detection statistics collected by Dr.Net for Android, in February, Android.HiddenAds ad-displaying trojans had been mostly detected as soon as once more. Their exercise elevated by 73.26%, in comparison with January. On the similar time, adware trojans from one other household, Android.MobiDash, attacked customers 58.85% much less typically.
The variety of Android.Spy adware trojan detections decreased by 27.33%, whereas banking trojan detections decreased by 18.77%. In the meantime, Android.Locker ransomware trojans had been detected 29.85% much less typically.
The next February occasions involving cellular malware are probably the most noteworthy:
- A major enhance within the exercise of Android.HiddenAds ad-displaying trojans,
- A lower within the variety of banking trojan and adware trojan assaults,
- A rise within the variety of ransomware trojan assaults.
To seek out out extra concerning the security-threat panorama for cellular units in February, learn our particular overview.
[ad_2]