[ad_1]
The FBI’s takedown of the LockBit ransomware group final week got here as LockBit was making ready to launch delicate information stolen from authorities laptop programs in Fulton County, Ga. However LockBit is now regrouping, and the gang says it can publish the stolen Fulton County information on March 2 until paid a ransom. LockBit claims the cache contains paperwork tied to the county’s ongoing prison prosecution of former President Trump, however courtroom watchers say teaser paperwork printed by the crime gang counsel a complete leak of the Fulton County information may put lives in danger and jeopardize numerous different prison trials.
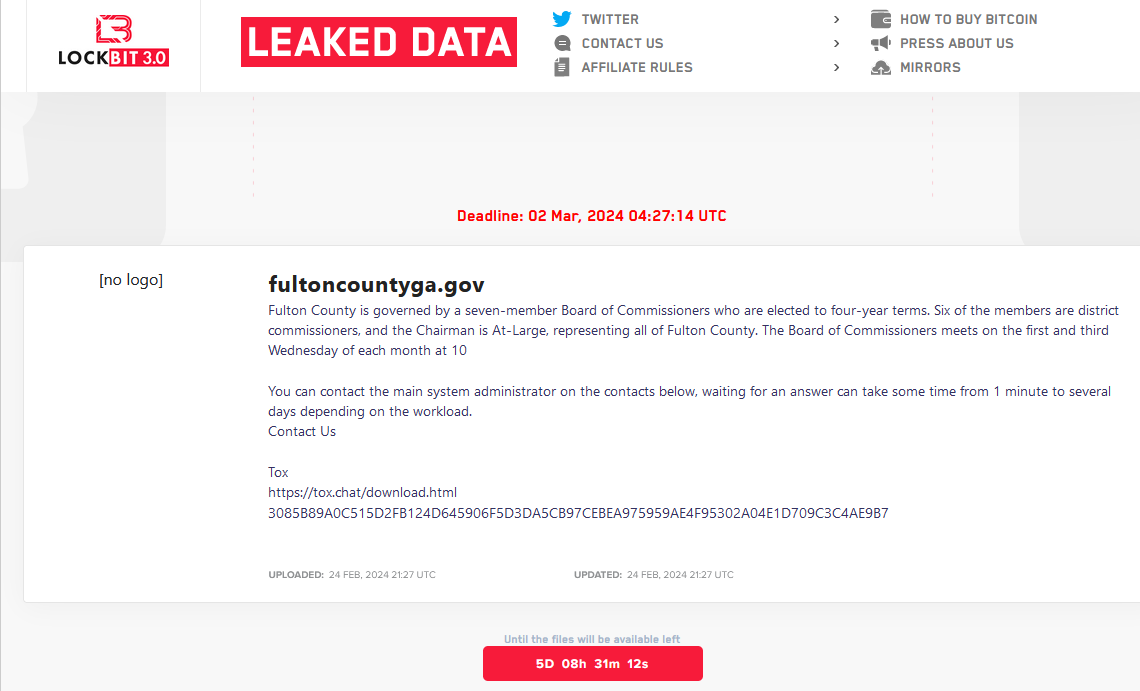
A brand new LockBit web site itemizing a countdown timer till the promised launch of information stolen from Fulton County, Ga.
In early February, Fulton County leaders acknowledged they had been responding to an intrusion that prompted disruptions for its cellphone, e mail and billing programs, in addition to a variety of county providers, together with courtroom programs.
On Feb. 13, the LockBit ransomware group posted on its sufferer shaming weblog a brand new entry for Fulton County, that includes a countdown timer saying the group would publish the info on Feb. 16 until county leaders agreed to barter a ransom.
“We are going to reveal how native buildings negligently dealt with data safety,” LockBit warned. “We are going to reveal lists of people chargeable for confidentiality. Paperwork marked as confidential might be made publicly obtainable. We are going to present paperwork associated to entry to the state residents’ private information. We purpose to offer most publicity to this case; the paperwork might be of curiosity to many. Conscientious residents will carry order.”
But on Feb. 16, the entry for Fulton County was faraway from LockBit’s web site with out clarification. This often solely occurs after the sufferer in query agrees to pay a ransom demand and/or enters into negotiations with their extortionists.
Nonetheless, Fulton County Fee Chairman Robb Pitts stated the board determined it “couldn’t in good conscience use Fulton County taxpayer funds to make a cost.”
“We didn’t pay nor did anybody pay on our behalf,” Pitts stated at an incident briefing on Feb. 20.
Simply hours earlier than that press convention, LockBit’s numerous web sites had been seized by the FBI and the U.Ok.’s Nationwide Crime Company (NCA), which changed the ransomware group’s homepage with a seizure discover and used the present design of LockBit’s sufferer shaming weblog to publish press releases concerning the legislation enforcement motion.

The feds used the present design on LockBit’s sufferer shaming web site to function press releases and free decryption instruments.
Dubbed “Operation Cronos,” the trouble concerned the seizure of practically three-dozen servers; the arrest of two alleged LockBit members; the discharge of a free LockBit decryption device; and the freezing of greater than 200 cryptocurrency accounts regarded as tied to the gang’s actions. The federal government says LockBit has claimed greater than 2,000 victims worldwide and extorted over $120 million in funds.
UNFOLDING DISASTER
In a prolonged, rambling letter printed on Feb. 24 and addressed to the FBI, the ransomware group’s chief LockBitSupp introduced that their sufferer shaming web sites had been as soon as once more operational on the darkish net, with contemporary countdown timers for Fulton County and a half-dozen different latest victims.
“The FBI determined to hack now for one cause solely, as a result of they didn’t need to leak data fultoncountyga.gov,” LockBitSupp wrote. “The stolen paperwork comprise quite a lot of fascinating issues and Donald Trump’s courtroom instances that would have an effect on the upcoming US election.”

A display screen shot launched by LockBit displaying numerous Fulton County file shares that had been uncovered.
LockBit has already launched roughly two dozen recordsdata allegedly stolen from Fulton County authorities programs, though none of them contain Mr. Trump’s prison trial. However the paperwork do seem to incorporate courtroom data which can be sealed and shielded from public viewing.
George Chidi writes The Atlanta Goal, a Substack publication on crime in Georgia’s capital metropolis. Chidi says the leaked information thus far features a sealed file associated to a baby abuse case, and a sealed movement within the homicide trial of Juwuan Gaston demanding the state flip over confidential informant identities.
Chidi cites stories from a Fulton County worker who stated the confidential materials contains the identities of jurors serving on the trial of the rapper Jeffery “Younger Thug” Williams, who’s charged together with 5 different defendants in a racketeering and gang conspiracy.
“The screenshots counsel that hackers will be capable to give any lawyer defending a prison case within the county a beginning place to argue that proof has been tainted or witnesses intimidated, and that the discharge of confidential data has compromised instances,” Chidi wrote. “Choose Ural Glanville has, I’m advised by workers, been working feverishly behind the scenes during the last two weeks to handle the unfolding catastrophe.”
LockBitSupp additionally denied assertions made by the U.Ok.’s NCA that LockBit didn’t delete stolen information as promised when victims agreed to pay a ransom. The accusation is an explosive one as a result of no person pays a ransom in the event that they don’t imagine the ransomware group will maintain up its finish of the cut price.
The ransomware group chief additionally confirmed data first reported right here final week, that federal investigators managed to hack LockBit by exploiting a identified vulnerability in PHP, a scripting language that’s extensively utilized in Net improvement.
“As a result of my private negligence and irresponsibility I relaxed and didn’t replace PHP in time,” LockBitSupp wrote. “On account of which entry was gained to the 2 primary servers the place this model of PHP was put in.”
LockBitSupp’s FBI letter stated the group saved copies of its stolen sufferer information on servers that didn’t use PHP, and that consequently it was capable of retain copies of recordsdata stolen from victims. The letter additionally listed hyperlinks to a number of new situations of LockBit darkish internet web sites, together with the leak web page itemizing Fulton County’s new countdown timer.
LockBit’s new information leak web site guarantees to launch stolen Fulton County information on March 2, 2024, until paid a ransom demand.
“Even after the FBI hack, the stolen information might be printed on the weblog, there is no such thing as a probability of destroying the stolen information with out cost,” LockBitSupp wrote. “All FBI actions are aimed toward destroying the repute of my associates program, my demoralization, they need me to go away and stop my job, they need to scare me as a result of they can’t discover and remove me, I can’t be stopped, you cannot even hope, so long as I’m alive I’ll proceed to do pentest with postpaid.”
DOX DODGING
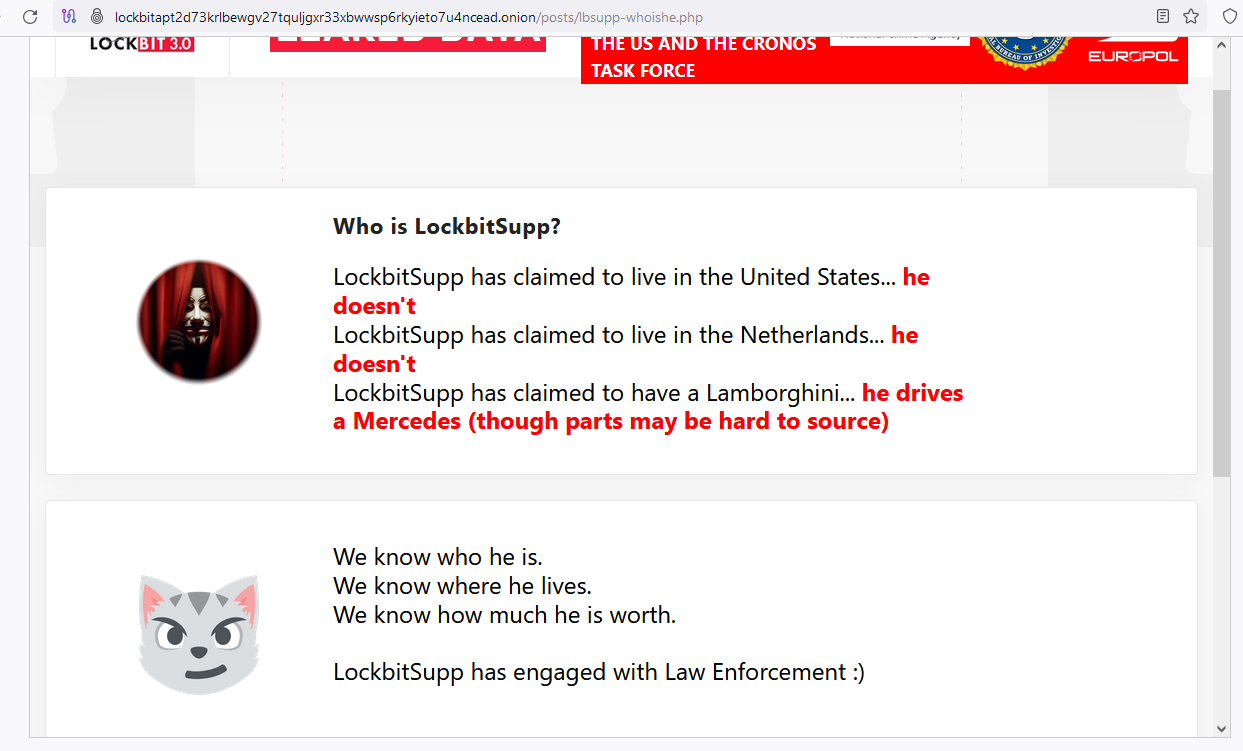
In January 2024, LockBitSupp advised XSS discussion board members he was disillusioned the FBI hadn’t provided a reward for his doxing and/or arrest, and that in response he was inserting a bounty on his personal head — providing $10 million to anybody who may uncover his actual title.
After the NCA and FBI seized LockBit’s web site, the group’s homepage was retrofitted with a weblog entry titled, “Who’s LockBitSupp? The $10M query.” The teaser made use of LockBit’s personal countdown timer, and advised the actual id of LockBitSupp would quickly be revealed.
Nonetheless, after the countdown timer expired the web page was changed with a taunting message from the feds, nevertheless it included no new details about LockBitSupp’s id.
On Feb. 21, the U.S. Division of State introduced rewards totaling as much as $15 million for data resulting in the arrest and/or conviction of anybody taking part in LockBit ransomware assaults. The State Division stated $10 million of that’s for data on LockBit’s leaders, and as much as $5 million is obtainable for data on associates.
In an interview with the malware-focused Twitter/X account Vx-Underground, LockBit workers asserted that authorities had arrested a few small-time gamers of their operation, and that investigators nonetheless have no idea the real-life identities of the core LockBit members, or that of their chief.
“They assert the FBI / NCA UK / EUROPOL have no idea their data,” Vx-Underground wrote. “They state they’re prepared to double the bounty of $10,000,000. They state they’ll place a $20,000,000 bounty of their very own head if anybody can dox them.”
TROUBLE ON THE HOMEFRONT?
Within the weeks main as much as the FBI/NCA takedown, LockBitSupp turned embroiled in numerous high-profile private and enterprise disputes on the Russian cybercrime boards.
Earlier this yr, somebody used LockBit ransomware to contaminate the networks of AN-Safety, a honored 30-year-old safety and know-how firm based mostly in St. Petersburg, Russia. This violated the golden rule for cybercriminals based mostly in Russia and former soviet nations that make up the Commonwealth of Unbiased States, which is that attacking your personal residents in these nations is the surest technique to get arrested and prosecuted by native authorities.
LockBitSupp later claimed the attacker had used a publicly leaked, older model of LockBit to compromise programs at AN-Safety, and stated the assault was an try and smear their repute by a rival ransomware group generally known as “Clop.” However the incident little doubt prompted nearer inspection of LockBitSupp’s actions by Russian authorities.
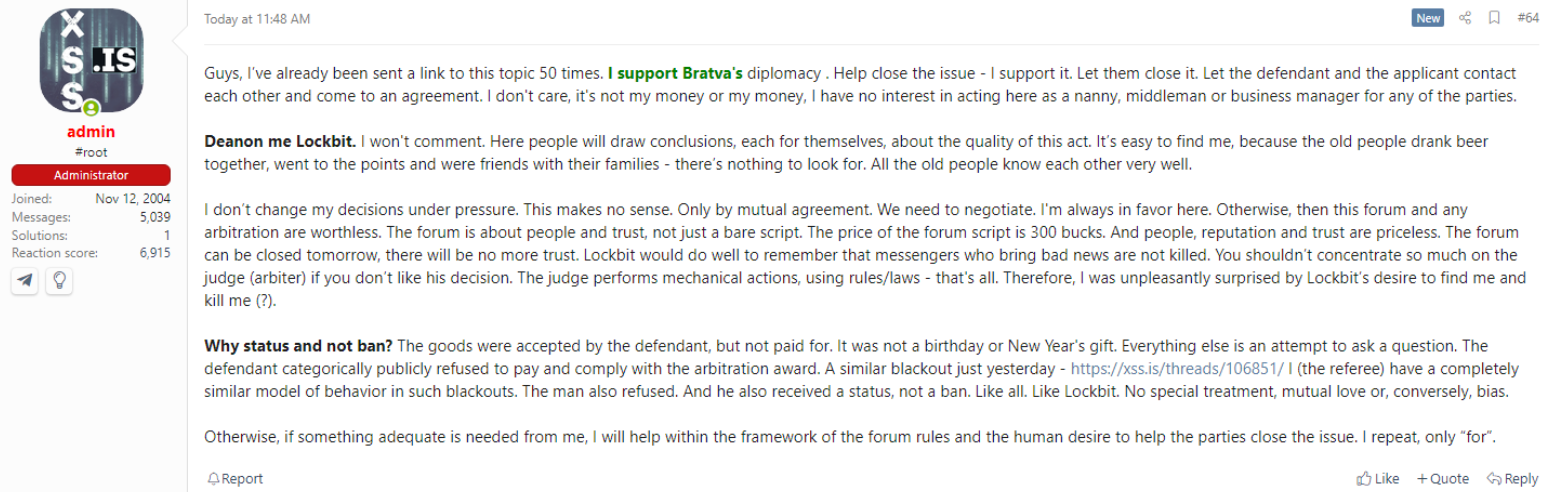
Then in early February, the administrator of the Russian-language cybercrime discussion board XSS stated LockBitSupp had threatened to have him killed after the ransomware group chief was banned by the neighborhood. LockBitSupp was excommunicated from XSS after he refused to pay an arbitration quantity ordered by the discussion board administrator. That dispute associated to a grievance from one other discussion board member who stated LockBitSupp just lately stiffed him on his promised share of an unusually giant ransomware payout.
INTERVIEW WITH LOCKBITSUPP
KrebsOnSecurity sought remark from LockBitSupp on the ToX prompt messenger ID listed in his letter to the FBI. LockBitSupp declined to elaborate on the unreleased paperwork from Fulton County, saying the recordsdata might be obtainable for everybody to see in just a few days.
LockBitSupp stated his workforce was nonetheless negotiating with Fulton County when the FBI seized their servers, which is why the county has been granted a time extension. He additionally denied threatening to kill the XSS administrator.
“I’ve not threatened to kill the XSS administrator, he’s blatantly mendacity, that is to trigger self-pity and injury my repute,” LockBitSupp advised KrebsOnSecurity. “It isn’t essential to kill him to punish him, there are extra humane strategies and he is aware of what they’re.”
Requested why he was so sure the FBI doesn’t know his real-life id, LockBitSupp was extra exact.
“I’m undecided the FBI doesn’t know who I’m,” he stated. “I simply imagine they’ll by no means discover me.”
It appears unlikely that the FBI’s seizure of LockBit’s infrastructure was by some means an effort to stave off the disclosure of Fulton County’s information, as LockBitSupp maintains. For one factor, Europol stated the takedown was the results of a months-long infiltration of the ransomware group.
Additionally, in reporting on the assault’s disruption to the workplace of Fulton County District Lawyer Fani Willis on Feb. 14, CNN reported that by then the intrusion by LockBit had endured for practically two and a half weeks.
Lastly, if the NCA and FBI actually believed that LockBit by no means deleted sufferer information, they needed to assume LockBit would nonetheless have at the least one copy of all their stolen information hidden someplace secure.
Fulton County continues to be attempting to recuperate programs and restore providers affected by the ransomware assault. “Fulton County continues to make substantial progress in restoring its programs following the latest ransomware incident leading to service outages,” reads the newest assertion from the county on Feb. 22. “Because the begin of this incident, our workforce has been working tirelessly to carry providers again up.”
Replace, Feb. 29, 3:22 p.m. ET: Simply hours after this story ran, LockBit modified its countdown timer for Fulton County saying they’d till the morning of Feb. 29 (right now) to pay a ransonm demand. When the official deadline neared right now, Fulton County’s itemizing was faraway from LockBit’s sufferer shaming web site. Requested concerning the removing of the itemizing, LockBit’s chief “LockBitSupp” advised KrebsOnSecurity that Fulton County paid a ransom demand. County officers have scheduled a press convention on the ransomware assault at 4:15 p.m. ET right now.
[ad_2]