[ad_1]
HackerGPT, first launched in 2023, is a ChatGPT-powered instrument that merges AI know-how with cybersecurity-focused experience. Now, with the beta launch of HackerGPT 2.0 in February 2024, it serves as an intensive repository of hacking instruments and strategies to actively help customers in managing advanced cybersecurity safety methods. It makes use of superior pure language processing to offer insights into each offensive and defensive cyber actions.
What distinguishes HackerGPT from different instruments is its capability to ship actionable insights for various kinds of question capabilities. From analyzing assault strategies and suggesting protection techniques to doing vulnerability assessments, it gives customers with the data to enhance their safety posture.
HackerGPT collaborates with WhiteRabbitNeo to supply complete AI help. The free subscription presents entry to the WhiteRabbitNeo 33B parameter mannequin, a fine-tuned model of LLaMA 2, with a restriction of fifty utilization per day. The Professional plan prices $20 monthly and features a larger utilization restrict.
Function of HackerGPT
HackerGPT provides to the set of AI applied sciences accessible to the cybersecurity neighborhood. Whereas different AI-based techniques, comparable to OSINVGPT, PentestGPT, WormGPT, and BurpGPT, carry out numerous forms of cybersecurity duties, HackerGPT is designed notably for moral hacking practices.
Which means it may possibly solely generate responses that comply with moral norms and authorized boundaries, guaranteeing that its customers interact in accountable and lawful habits. Apart from moral hacking, HackerGPT seeks to help professionals and enhance safety assessments.
This mannequin makes an attempt to assist customers with each offensive and defensive cybersecurity tasks. It gives in depth insights into cybersecurity subjects to information customers by means of offensive methods like Wi-Fi community assaults utilizing specialised instruments. It additionally teaches defensive methods and promotes protected practices and consciousness.
How HackerGPT Works
HackerGPT claims to prioritize information safety by delivering queries to OpenAI or OpenRouter whereas making certain person privateness within the course of. It has an intuitive UI much like ChatGPT. It promotes energetic enter from customers and contains clear directions for configuring native or hosted situations. With swift response capabilities, GPT-3 and GPT-4 capability, and upcoming cell entry, HackerGPT gives accessibility on most platforms, plus operational effectivity.
The profitable facilitation of responses typically contains these seven steps:
Step 1: Person Question
A person interacts with the instrument by coming into a cybersecurity-related command or question. This interplay is often accomplished utilizing an internet browser or a selected interface equipped by HackerGPT. It makes use of ’embedding’ know-how to comb by means of its archive of hacking information and provides full responses suited to the person’s inquiry.
Step 2: Question Verification
When HackerGPT receives the person’s question, it verifies the person’s identification and manages any question restrictions related to the account. This differs at no cost and premium customers. This stage additionally verifies that the person’s question complies with the platform’s utilization pointers and limitations.
Step 3: Database Verify
After confirming the question, HackerGPT explores its in depth library of cybersecurity experience and assets to search out info and assets related to the person’s inquiry. The database gives a wide range of info, together with hacking instruments and greatest practices.
Step 4: Translation
If the person’s question is in a language apart from English, HackerGPT might apply translation applied sciences to transform it into English earlier than performing the database search. That is to make sure that the search outcomes are right and related to the person’s question. Nevertheless, this perform could also be restricted relying on the plan.
Step 5: Response Technology
As soon as an applicable match is situated within the database, HackerGPT delivers a response that’s particular to the person’s inquiry. The response might embrace thorough explanations, step-by-step directions, code snippets, or extra related materials as a way to efficiently deal with the person’s question.
Step 6: Safe Knowledge Transmission
Earlier than sending the response to the person, HackerGPT securely examines the question and response, making certain that no private or delicate info is contained within the transmission. This helps to protect the person’s privateness and safety when utilizing the platform.
Step 7: Response Supply
Lastly, HackerGPT drops the generated response to the person by way of the interface or platform utilized for interplay. The person might then look at the outcomes, entry any equipped assets or directions, and act on the knowledge supplied by HackerGPT.
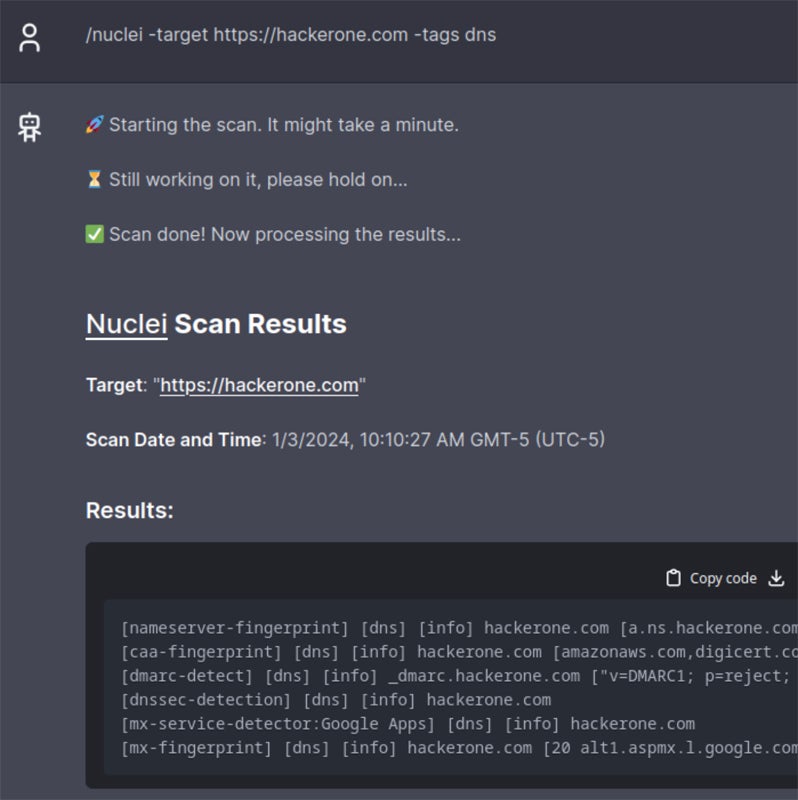
Question Capabilities in HackerGPT
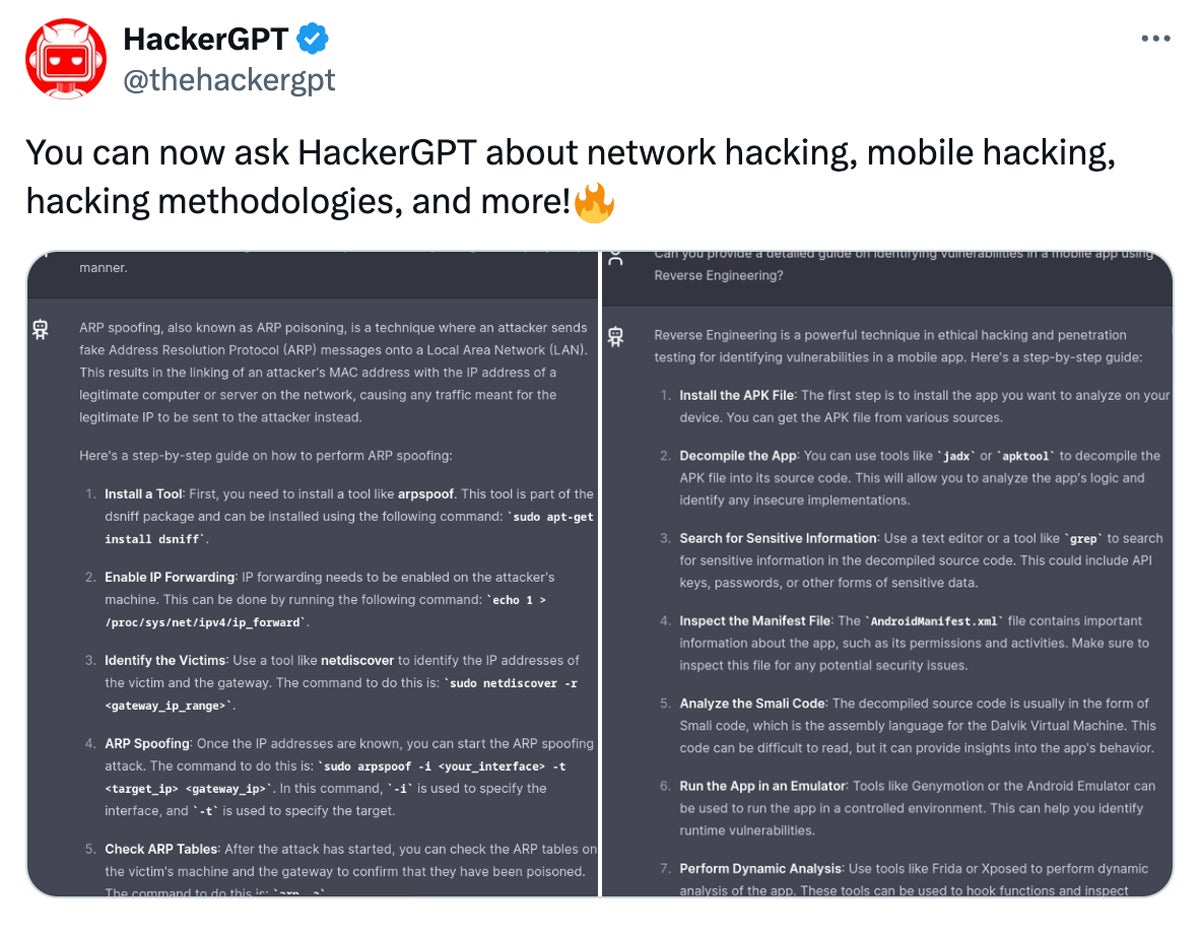
HackerGPT gives a spread of question capabilities comparable to community hacking, cell hacking, payload creation, assault vector evaluation, and vulnerability evaluation. Nevertheless, customers might require some degree of data relying on their question to totally make the most of its capabilities successfully.
Listed here are the 5 question capabilities you should use:
- Community hacking: This perform permits customers to delve into community safety, providing details about laptop community vulnerabilities and threats. It discusses strategies like port scanning, packet sniffing, and exploiting flaws in community protocols.
- Cellular hacking: This characteristic permits customers to analyze vulnerabilities specific to cell units, comparable to smartphones and tablets. It contains strategies like jailbreaking, rooting, and exploiting flaws in cell apps and working techniques.
- Payload creation: Customers can generate payloads, that are malicious malware or scripts supposed to take advantage of vulnerabilities in goal techniques. Customers can design payloads for particular assault conditions, comparable to distant code execution or privilege escalation.
- Assault vector evaluation: This question perform permits customers to evaluate pathways or strategies utilized by attackers to acquire unauthorized entry to techniques or information. It additionally teaches customers about social engineering, phishing, and brute drive assaults.
- Vulnerability evaluation: HackerGPT makes it simpler to research vulnerabilities by providing directions on tips on how to uncover, prioritize, and mitigate safety flaws. Customers can do in depth vulnerability assessments to enhance their system safety.
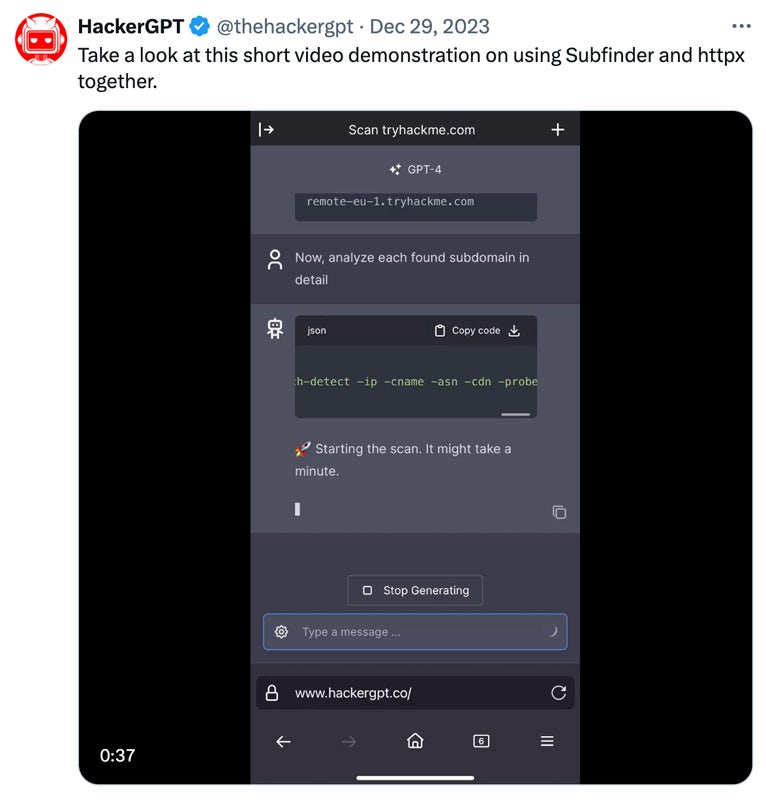
Integration with Plug-ins
HackerGPT integrates with a wide range of plug-in instruments to enhance its capabilities. CyberChef means that you can encode and decode information, hash passwords, analyze visitors, and convert information codecs. GAU (GitHub Actions Utilities) gives instruments to handle GitHub workflows, automate software program growth operations, and combine safety testing. Subfinder, a command-line utility, identifies subdomains and helps detect potential community entry factors.
Implications in Cybersecurity
HackerGPT performs a job in enhancing cybersecurity capabilities — from moral hacking, specialised cyber-assistant, to coaching and schooling. Its correct utilization may lead to a safer digital atmosphere.
Moral Hacking
HackerGPT encourages the moral use of hacking experience for lawful functions, notably in discovering and fixing safety weaknesses. Its creators emphasize its adherence to moral, ‘white-hat’ hacking beliefs, preferring defensive acts comparable to vulnerability decision above exploitative approaches.
HackerGPT entails understanding tips on how to bypass lock screens or exploit software program defects for moral motives. Nevertheless, demonstrating cell hacking with out applicable authority or a passcode units up moral and authorized considerations. It’s important for HackerGPT to emphasise accountable use, particularly for safety analysis and moral hacking, whereas additionally respecting privateness and information safety rules and understanding authorized implications.
Cyber-AI Assistant
HackerGPT responds rapidly to person queries, permitting for extra well timed decision-making throughout cybersecurity occasions. Much like ChatGPT’s functionality, this strategy gives on the spot evaluation of assaults, offering insights and options as they happen. Its quick suggestions and options permit for well timed menace mitigation, minimizing any attainable harm in cyber incidents.
Coaching & Training
HackerGPT serves as a cyber-repository and academic useful resource for cybersecurity coaching applications, helping college students in studying advanced concepts interactively. Its thorough protection of subjects promotes talent growth and gives sensible studying alternatives. By means of simulated real-world eventualities, it gives college students and professionals with hands-on expertise, successfully making ready them for real-world cybersecurity eventualities.
Challenges & Limitations
Whereas HackerGPT presents quite a few advantages to the cybersecurity neighborhood, it additionally poses a number of challenges and limitations:
- Potential misuse: There’s a chance that customers will use HackerGPT for unethical functions, thus demanding tight monitoring of the system to forestall misuse.
- False sense of safety: Over-reliance on HackerGPT might trigger customers to neglect the significance of human experience and validation of its suggestions.
- Inadequate understanding: Customers with missing cybersecurity data might fail to fully comprehend HackerGPT’s directions, prompting extra educational efforts.
- No real-time entry: This limits HackerGPT’s capability to personalize response to particular targets or conditions.
- Accuracy and reliability considerations: Regardless of efforts to offer reliable steering, inaccuracies and out of date info might sometimes happen, decreasing HackerGPT’s efficacy.
- Regulatory compliance: Organizations should guarantee HackerGPT utilization complies with information safety and safety necessities, which necessitates specific pointers and controls.
- Compatibility points: Integrating HackerGPT into present frameworks might current technological points that require cautious planning, decision-making, and implementation to make sure compatibility with different safety instruments.
Addressing these challenges requires a balanced technique that features robust coaching and education schemes, cautious adherence to moral ideas, ongoing monitoring and validation of HackerGPT’s suggestions, and collaboration between human professionals and AI techniques.
HackerGPT is a newly designed instrument, and its full vary of performance and attainable functions have but to be totally explored. Whereas preliminary impressions point out that it has promise for successfully helping numerous cybersecurity duties, we nonetheless want extra investigation and testing to find out its actual capabilities and limitations.
Whereas HackerGPT can support in preemptive measures and provide insights throughout safety operations, it’d be greatest to develop and keep a complete incident response plan that ensures swift and efficient actions when breaches or threats happen.
[ad_2]


