[ad_1]
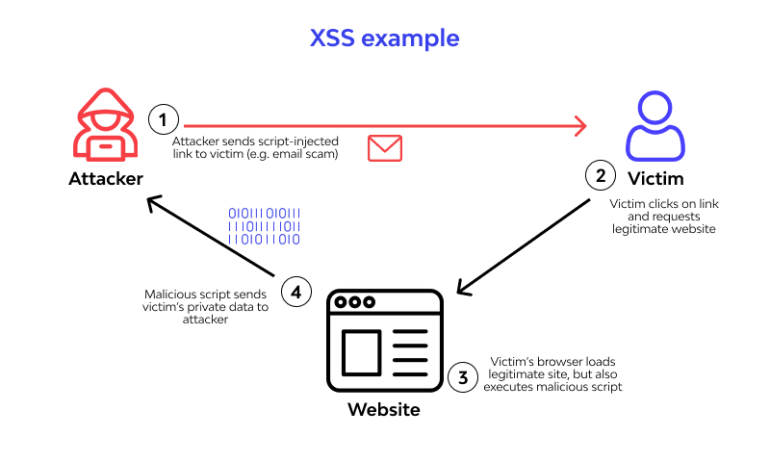
APIs (Software Programming Interfaces) have proliferated extensively, which will increase their susceptibility to varied vulnerabilities. Within the realm of net purposes, prime examples that stand out are SOAP (Easy Object Entry Protocol) and Representational State Switch (REST) APIs. Because of their inherent complexity and the dynamic nature of software program ecosystems, frequent vulnerabilities embrace insufficient authentication mechanisms and injection assaults reminiscent of SQL injection or cross-site scripting (XSS).

At Wallarm, we’ve been addressing API leaks for years, gaining deep insights into their causes and penalties. By way of this expertise, we’ve recognized three crucial elements behind a majority of those leaks.
“In our pursuit of innovation, understanding API leaks isn’t nearly knowledge safety – it’s about belief. By brazenly addressing vulnerabilities, we reinforce our buyer’s techniques and display integrity.”
– Ivan Novikov, CEO @ Wallarm
Formed by real-world experiences and the challenges our purchasers face, listed here are a number of important insights:
1. Unintentional Publicity Throughout Public Repositories
A standard pitfall we’ve encountered is the publicity of personal API specs (or supply code) throughout public repositories. When the Wallarm workforce was working with a buyer, an analogous scenario occurred when the corporate tried to streamline collaboration between distant builders utilizing GitHub. The shopper by accident pushed delicate API keys and documentation to a public repository.

This error gave attackers unfettered entry to their inside API mechanisms, resulting in unauthorized knowledge entry. Such incidents underscore the fragile stability between collaboration and safety.
2. Publicly Out there In-Improvement & Non-public APIs
One other important threat arises from the untimely publicity of in-development APIs to the general public. Whereas such APIs principally come geared up with debugging functionalities, they don’t seem to be absolutely secured and may develop into gateways for knowledge breaches.
The Wallarm workforce noticed such a situation unfold with an e-commerce shopper whose in-development API for order administration was uncovered to customers with out satisfactory safety measures. Because of this, attackers might entry and manipulate buyer knowledge, resulting in a extreme breach. This expertise highlighted the crucial want for securing APIs at each stage of their lifecycle.
3. Releasing Unverified Integration Instruments & Cell Apps
The push to launch cell apps, SDKs, and API scripts can generally bypass crucial safety verification steps. One case particularly that stands out for us concerned a monetary providers agency that launched a cell app with hard-coded API keys. When the app was decompiled, it uncovered delicate monetary knowledge that inevitably put consumer privateness in danger. Equally, a social media API’s SDK was launched with out correct safety checks, resulting in the extended publicity of dozens of consumer tokens.
These incidents illustrate the hazards of overlooking safety within the eagerness to facilitate API integration and utilization.

By way of years of addressing API leaks at Wallarm, these examples have been instrumental in refining our method to API safety. They function stark reminders of the significance of fixed vigilance, thorough complete safety practices, and the continual schooling for builders on safe coding practices.
At Wallarm, we have now constructed a strong answer to handle API leaks and shield enterprise clients of any dimension by revoking leaked tokens. On an analogous be aware, we additionally just lately launched our NIST CSF 2.0 Dashboard aimed toward helping companies in enhancing their cybersecurity frameworks and methods.
Wallarm’s dashboard helps you:
– Align with NIST CSF 2.0 tips for an enhanced safety posture
– Enhanced visibility, establish safety gaps, and provide tailor-made implementation safeguards
Uncover how Wallarm helps you safe your digital property successfully.
The submit High 3 API Leaks Recognized by Cybersecurity & InfoSec Consultants appeared first on Wallarm.
*** This can be a Safety Bloggers Community syndicated weblog from Wallarm authored by wlrmblog. Learn the unique submit at: https://lab.wallarm.com/top-3-api-leaks-identified-by-cybersecurity-infosec-experts/
[ad_2]