[ad_1]
Graham Cluley Safety Information is sponsored this week by the parents at Cynet. Because of the nice workforce there for his or her assist!

Thorough, impartial checks are an important useful resource as cybersecurity leaders and their groups consider distributors’ talents to protect in opposition to more and more refined threats to their group. And maybe no evaluation is extra extensively trusted than the annual MITRE Engenuity ATT&CK Evaluations: Enterprise.
This analysis is crucial for testing distributors as a result of it’s nearly unattainable to guage cybersecurity distributors primarily based on their very own efficiency claims. Together with vendor reference checks and proof of worth evaluations (POV) — a stay trial — of their atmosphere, the MITRE Engenuity outcomes add further goal enter to holistically assess cybersecurity distributors.
On this piece, we’ll unpack MITRE Engenuity’s most up-to-date methodology to check safety distributors in opposition to real-world threats, provide our interpretation of the outcomes and establish the highest takeaways rising from the analysis of Cynet’s all-in-one safety resolution.
How does MITRE Engenuity take a look at distributors throughout the analysis?
The MITRE Engenuity ATT&CK Analysis is carried out by MITRE Engenuity and checks the endpoint safety options in opposition to a simulated assault sequence primarily based on real-life approaches taken by well-known superior persistent menace (APT) teams. The MITRE Engenuity ATT&CK Evaluations: Enterprise examined 29 vendor options by emulating the assault sequences of Turla, a classy Russia-based menace group recognized to have contaminated victims in over 45 nations.
An necessary caveat is that MITRE doesn’t rank or rating vendor outcomes. As a substitute, the uncooked take a look at knowledge is printed together with some fundamental on-line comparability instruments. Patrons then use that knowledge to guage the distributors primarily based on their group’s distinctive priorities and desires. The collaborating distributors’ interpretations of the outcomes are simply that — their interpretations.
So, how do you interpret the outcomes?
That’s an amazing query — one which lots of people are asking themselves proper now. The MITRE Engenuity ATT&CK Evaluations: Enterprise outcomes aren’t introduced in a format that many people are used to digesting ( you, magical graph with quadrants).
And impartial researchers usually declare “winners” to lighten the cognitive load of determining which distributors are the highest performers. On this case, figuring out the “finest” vendor is subjective. Which, for those who don’t know what to search for, can really feel like a trouble for those who’re already annoyed with making an attempt to evaluate which safety vendor is the proper match in your group.
With these disclaimers issued, let’s now overview the outcomes themselves to check and distinction how collaborating distributors carried out in opposition to Turla.
MITRE Engenuity ATT&CK Outcomes Abstract
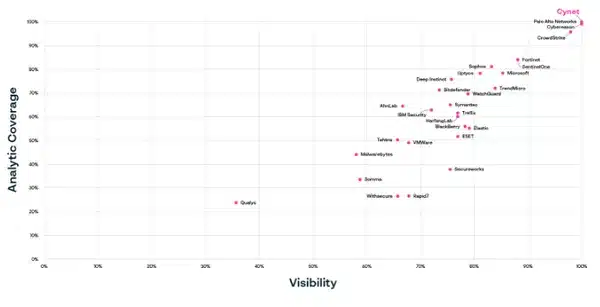
The next tables current Cynet’s evaluation and calculation of all vendor MITRE Engenuity ATT&CK Evaluations: Enterprise take a look at outcomes for a very powerful measurements: General Visibility, Detection Accuracy, and General Efficiency. There are numerous different methods to take a look at the MITRE outcomes, however we think about these to be most indicative of an answer’s potential to detect threats.
General Visibility is the full variety of assault steps detected throughout all 143 sub-steps. Cynet defines Detection High quality as the proportion of assault sub-steps that included “Analytic Detections – those who establish the tactic (why an exercise could also be taking place) or method (each why and the way the method is going on).
Moreover, it’s necessary to take a look at how every resolution carried out earlier than the seller adjusted configuration settings resulting from lacking a menace. MITRE permits distributors to reconfigure their programs to try to detect threats that they missed or to enhance the knowledge they provide for detection. In the true world we don’t have the luxurious of reconfiguring our programs resulting from missed or poor detection, so the extra real looking measure is detections earlier than configuration adjustments are applied.
How’d Cynet do?
Based mostly on Cynet’s evaluation, our workforce is happy with our efficiency in opposition to Turla within the 2023 MITRE Engenuity ATT&CK Evaluations: Enterprise, outperforming the vast majority of distributors in a number of key areas. Listed here are our prime takeaways:
- Cynet delivered 100% Detection (19 of 19 assault steps) with NO CONFIGURATION CHANGES
- Cynet delivered 100% Visibility (143 of 143 assault sub-steps) with NO CONFIGURATION CHANGES
- Cynet delivered 100% Analytic Protection (143 of 143 detections) with NO CONFIGURATION CHANGES
- Cynet delivered 100% Actual-time Detections (0 Delays throughout all 143 detections)
Let’s dive slightly deeper into Cynet’s evaluation of a number of the outcomes.
Cynet’s all-in-one safety resolution was a prime performer when evaluating each visibility and detection high quality. This evaluation illustrates how effectively an answer does in detecting threats and offering the context essential to make the detections actionable. Missed detections are an invite for a breach, whereas poor high quality detections create pointless work for safety analysts or probably trigger the alert to be ignored, which once more, is an invite for a breach.
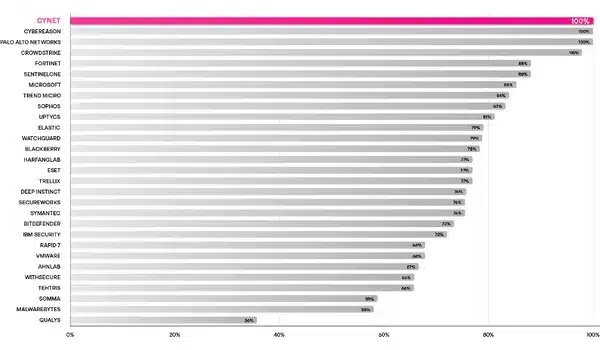
Cynet delivered 100% visibility and completely detected each one of many 143 assault steps utilizing no configuration adjustments. The next chart reveals the proportion of detections throughout all 143 assault sub-steps earlier than the distributors applied configuration adjustments. Cynet carried out in addition to two very giant, well-known, safety firms regardless of being a fraction of their measurement and much better than a number of the largest names in cybersecurity.
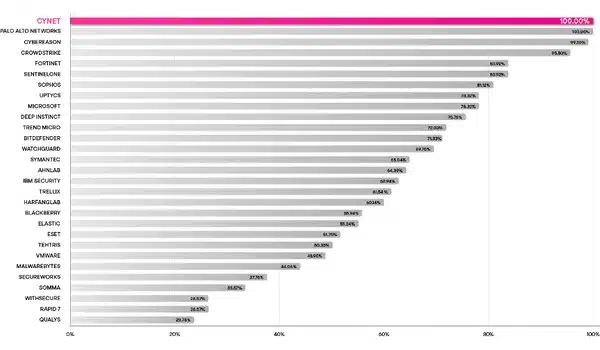
Cynet offered analytic protection for 100% of the 143 assault steps utilizing no configuration adjustments. The next chart reveals the proportion of detections that contained necessary normal, tactic or method data throughout the 143 assault sub-steps, once more earlier than configuration adjustments have been applied. Cynet carried out in addition to Palo Alto Networks, a $115 billion publicly traded firm with 50 occasions the variety of staff, and much better than many established, publicly traded manufacturers.
Nonetheless have questions?
On this on-demand webinar, Cynet CTO Aviad Hasnis and ISMG SVP Editorial Tom Area overview the newest MITRE ATT&CK outcomes and share professional recommendation for cybersecurity leaders to seek out the seller that most closely fits the precise wants of their group. Additionally they unpack Cynet’s efficiency throughout the checks and establish alternatives ot advance your workforce’s targets with the all-in-one safety resolution.
In the event you’re keen on sponsoring my website for every week, and reaching an IT-savvy viewers that cares about cybersecurity, you’ll be able to discover extra data right here.
[ad_2]



