[ad_1]
SaaS safety checklists are frameworks for shielding knowledge and purposes in cloud-based environments. They function benchmarks for upholding sturdy safety necessities, evaluating present instruments, and assessing potential options. These checklists embrace safety requirements and finest practices for SaaS and cloud purposes, and B2B SaaS suppliers use them to ensure that their options match buyer safety requirements.
Free SaaS Safety Guidelines Template
Every group’s SaaS safety guidelines varies — some are customizable to satisfy particular calls for, whereas others are {industry} or use-case particular. To start, you need to use a pattern guidelines to evaluate your SaaS instruments or discover new options, then regulate it to your group’s wants. We’ve designed a customizable template that can assist you develop your personal SaaS safety guidelines. Click on the picture beneath to obtain the total template.

When you’ve finalized your guidelines, reply ‘Sure’ to every guidelines merchandise if the listed coverage, characteristic, or performance is offered and correctly set. In any other case, verify ‘No’ if any facet is lacking or not totally fulfilled.
Information Safety & Risk Detection Framework
The information safety and menace detection framework serves as the inspiration for knowledge safety plans, defending mental property, buyer knowledge, and worker data. This framework ensures that applicable authentication measures, encryption methods, knowledge retention insurance policies, and backup procedures are in place.
Decide which threats and vulnerabilities have an effect on your agency and its SaaS apps. Widespread threats embrace misconfigurations, cross-site scripting assaults, and knowledge breaches. This step reduces the dangers of unlawful entry, knowledge loss, and regulatory noncompliance, in addition to protects the integrity and safety of delicate data inside SaaS purposes.
Inquiries to Reply
Contemplate these inquiries to confirm your group’s knowledge safety and menace detection methods:
- Are multi-factor authentication methods required for person entry?
- Is knowledge encrypted in transit and at relaxation?
- Are entry controls and least privilege rules efficiently carried out?
- Is person entry to knowledge routinely checked and assessed for compliance?
- Are your knowledge loss prevention (DLP) options efficient at stopping unlawful sharing?
- Do you perceive the potential dangers related with every supplier’s integration factors?
- Is there systematic monitoring in place for frequent threats?
Methods to Guarantee Information Safety & Risk Prevention
To check the effectivity of your SaaS platform’s knowledge safety and menace prevention technique, carry out these beneficial protocols:
- Encrypt knowledge: Make it possible for any knowledge saved in your SaaS utility’s databases is encrypted at relaxation. Information transferred between customers’ units and your servers needs to be secured throughout transit utilizing protocols similar to transport layer safety.
- Implement sturdy entry controls: Make use of methods for verifying person identities. To scale back the danger of unauthorized entry to delicate knowledge, customers ought to solely be supplied with the extent of entry required to carry out their duties throughout the program.
- Conduct frequent safety audits and penetration testing: Detect and resolve any vulnerabilities earlier than they’re exploited by fraudulent actors to reduce the chance of knowledge breaches.
- Implement sturdy monitoring mechanisms: Steady monitoring and incident response techniques detect suspicious exercise or unlawful entry makes an attempt in actual time. Safety breaches have a decrease affect when they’re detected and responded to on time.
- Keep up to date with safety finest practices: Sustain with the newest safety finest practices and replace your safety processes and insurance policies regularly to align with rising threats and regulatory necessities.
Right here’s the info safety and menace prevention part of our template:

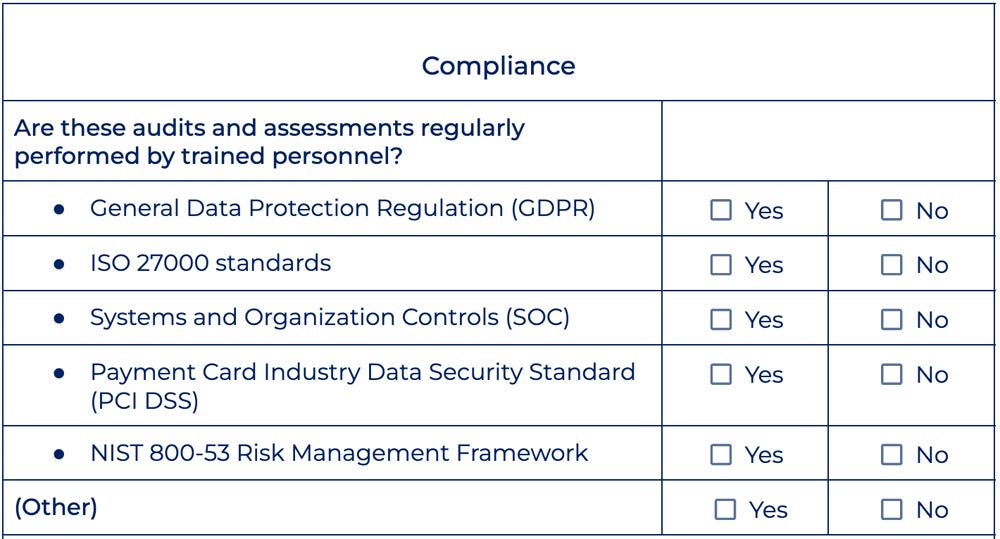
Compliance
Understanding regulatory compliance requirements helps organizations meet authorized and regulatory necessities. Failure to adjust to these requirements dangers organizations of authorized issues, fines, or reputational harm. SaaS programs often deal with delicate consumer data, and compliance covers this by defending knowledge safety, reduces dangers, and fosters belief amongst stakeholders.
Widespread compliance requirements embrace GDPR, which governs knowledge processing for EU members; PCI DSS, which ensures secure bank card transactions; and NIST 800-53 for IT threat administration. ISO 27000 is a typical for data safety and SOC is for sustaining shopper knowledge integrity and safety throughout a number of dimensions.
Inquiries to Reply
Test when you adhere to those frequent compliance requirements:
- Do you conduct frequent audits and evaluations to ensure steady compliance with relevant regulatory requirements and frameworks?
- Are you in compliance with the Basic Information Safety Regulation (GDPR) for the gathering and processing of EU member knowledge?
- Is your agency in compliance with the Cost Card Business Information Safety Normal (PCI DSS) to guard cardholder knowledge throughout transactions?
- Do you employ the NIST 800-53 Threat Administration Framework to look at IT dangers?
- Are you in compliance with ISO 27000 data safety administration requirements for securing third-party knowledge, monetary data, mental property, and worker knowledge?
- Have you ever carried out Programs and Group Controls (SOC) to make sure buyer knowledge integrity, confidentiality, and availability in accordance with SOC framework standards?
Methods to Confirm Compliance Requirements Adherence
Listed here are some tips that can assist you resolve whether or not your online business must adjust to sure requirements:
- Test the applicability: Set up whether or not your organization handles delicate knowledge or conducts transactions topic to regulatory requirements similar to GDPR or PCI DSS. Analysis whether or not a particular compliance is required in your sector.
- Determine the consumer necessities: In case your purchasers or companions demand compliance, ensure that your group fulfills their standards to be able to proceed enterprise partnerships.
- Evaluation your authorized obligations: Decide whether or not your group is topic to any authorized mandates based mostly on its location or jurisdiction, and contemplate the potential authorized implications of noncompliance.
- Conduct a cost-benefit evaluation: Do a radical examine of the prices and advantages of compliance to be able to make knowledgeable choices constant together with your group’s strategic targets and goals.
- Contemplate voluntary compliance: Contemplate implementing {industry} finest practices to enhance knowledge safety and set up belief with stakeholders even when compliance just isn’t required. Then, study the dangers related with knowledge safety and privateness.
- Preserve transparency and communication: Clarify your group’s strategy to knowledge safety and privateness to prospects, companions, and stakeholders. Transparency about your safety insurance policies may also help construct confidence and credibility.
Beneath is the compliance part of our guidelines:
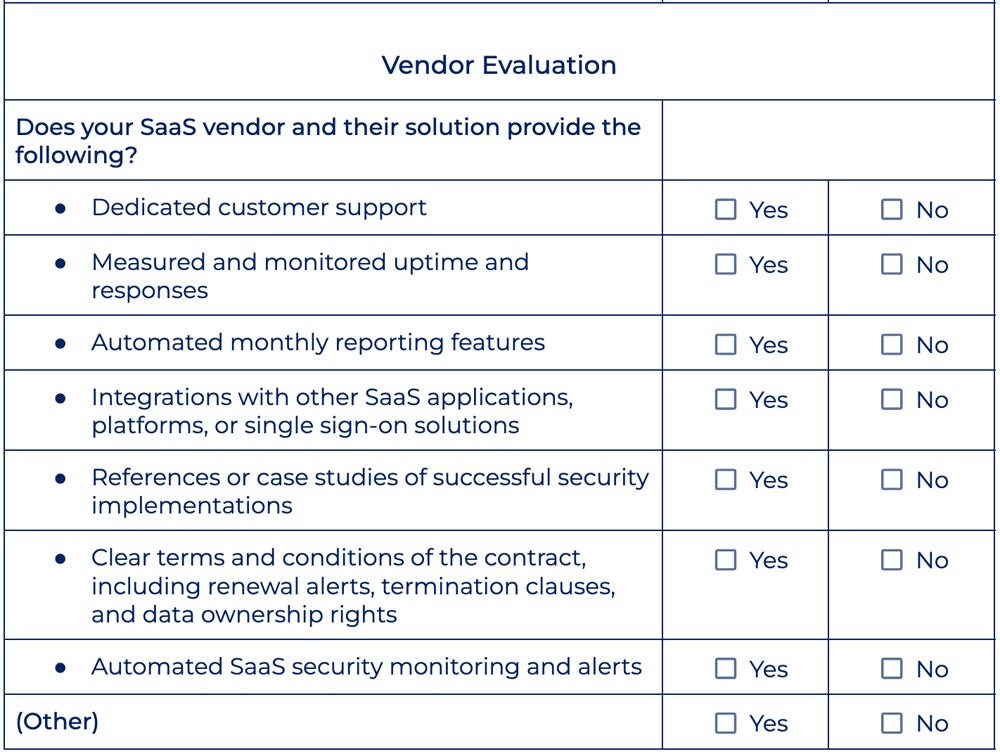
SaaS Vendor Analysis
When assessing SaaS distributors, contemplate quite a lot of elements, together with service metrics similar to uptime, response time, and buyer help availability. Study price components like license phrases, worth, {and professional} service charges. Moreover, assess options together with integrations, single sign-on (SSO) assist, reporting capabilities, contract circumstances, and the seller’s means to produce actionable insights and proposals.
Inquiries to Reply
To judge your SaaS vendor, ask your self these questions:
- Does the seller supply devoted buyer assist and what’s their availability?
- What are the SaaS service’s uptime and response time assurances, and the way are they decided and monitored?
- Are there automated month-to-month reporting options that present perception into safety efficiency and compliance?
- What integrations does the seller present with different SaaS apps, platforms, and single sign-on options?
- Can the seller give references or case research that present efficient safety deployments in related organizations?
- What are the contract’s phrases and circumstances, together with renewal notices, termination provisions, and knowledge possession rights?
- Do your cloud suppliers present automated SaaS safety monitoring and alerts?
Methods to Consider Your SaaS Vendor
Each vendor answer your group makes use of ought to match together with your wants. Do the next to check its suitability:
- Test the seller’s privateness insurance policies: Inquire concerning the vendor’s knowledge encryption processes, each at relaxation and through transit. Evaluation the seller’s privateness insurance policies to see how they deal with and safe shopper knowledge, similar to knowledge retention and sharing.
- Assess vendor answer’s safety features: Consider the seller’s safety controls and entry administration options to see how they stop undesirable entry to your knowledge. Search for options similar to RBAC, MFA, SSO, and audit logs.
- Contemplate safety certifications in analysis: Search for SaaS distributors who’ve obtained crucial safety certifications, observe {industry} requirements and laws, and supply options to handle compliance.
- Discover incident response and knowledge breach insurance policies: Inquire concerning the vendor’s options for detecting, reporting, and responding to safety points, in addition to their communication protocols for alerting prospects about any breaches or vulnerabilities.
- Safety infrastructure and redundancy: Test the seller’s knowledge facilities, community structure, backup and catastrophe restoration plans, and uptime assurances. Affirm that the seller makes use of industry-standard safety applied sciences and processes.
Take a more in-depth have a look at the SaaS vendor analysis guidelines beneath:
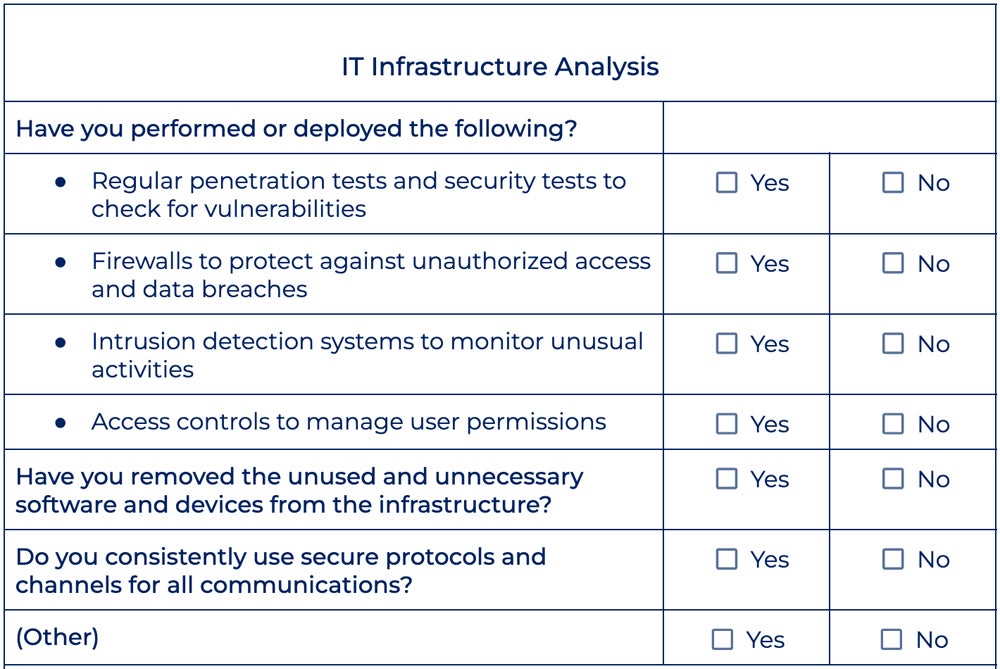
IT Infrastructure Evaluation
This part underscores the worth of investing in IT infrastructure safety. This consists of defending various technological property, similar to software program, {hardware}, units, and cloud assets, from potential safety flaws like malware, ransomware, theft, phishing assaults, and bots. Cloud infrastructure safety ought to particularly deal with layers similar to bodily property, purposes, networks, and knowledge for full safety towards safety threats.
Inquiries to Reply
When assessing your IT infrastructure, listed here are a number of key components to think about:
- Have common penetration and safety testing been carried out to establish vulnerabilities?
- Have all unused and pointless software program and gear been faraway from the infrastructure?
- Are safe protocols and channels utilized constantly throughout all communications?
- Are entry restrictions in place and periodically assessed to effectively handle person permissions?
- Are firewalls configured and maintained to forestall undesirable entry and knowledge breaches?
- Have intrusion detection programs been established and maintained in order that any safety dangers could be detected and addressed rapidly?
Methods to Conduct an IT Infrastructure Evaluation
Achieve insights into your infrastructure to make knowledgeable choices concerning the options your group wants. Observe these tips beneath:
- Create a software program and system stock: Make an entire checklist of all software program packages and units within the infrastructure. Determine any pointless or out of date software program and units by way of the stock course of.
- Consider the community structure: Decide whether or not the SaaS supplier makes use of community segmentation to separate consumer knowledge and apps from each other, decreasing the danger of unauthorized entry and lateral motion within the occasion of a safety breach.
- Assess the bodily safety measures: Consider entry controls, surveillance programs, and environmental controls. Test that the info facilities’ bodily safety meets {industry} necessities, in addition to their redundancy and failover capabilities.
- Evaluation storage and buyer knowledge safety strategies: Be sure that your supplier makes use of strong encryption methods and key administration practices to protect knowledge confidentiality and integrity.
- Study safety monitoring capabilities: Inquire concerning the instruments and procedures used to detect and reply to safety points in actual time, similar to intrusion detection programs (IDS) and safety data and occasion administration (SIEM) programs.
Discover the IT infrastructure evaluation portion of our safety guidelines:
Cybersecurity Coaching
Cybersecurity coaching is a workforce initiative that helps all staff establish threats and potential assaults. Social engineering, for instance, is a menace that makes use of human vulnerabilities for unlawful entry. Inside actors additionally play a considerable function in cybersecurity breaches. Ongoing coaching initiatives can cowl safety components past primary consciousness, enabling personnel to identify and mitigate attainable cyber dangers effectively.
Inquiries to Reply
Test the next to see in case your cybersecurity coaching insurance policies are correctly executed:
- Have staff been knowledgeable of dangerous cybersecurity behaviors, similar to accessing public Wi-Fi or unsecured private units for work-related duties?
- Is there cybersecurity coaching on finest practices, together with setting sturdy passwords in accordance with the group’s coverage?
- Have staff been knowledgeable of primary safety dangers like malware, phishing, and {hardware} loss, all of which make the most of human errors?
- Is multi-factor authentication established, and are workers instructed on the right way to use it?
- Is there a human-factor cybersecurity analysis technique in place to commonly study workforce cybersecurity threats?
- Are workers routinely assessed on their cybersecurity data and consciousness utilizing exams or simulations?
Methods to Implement Correct Cybersecurity Coaching
Efficient cybersecurity coaching ought to educate staff of the potential dangers and finest practices for utilizing SaaS purposes securely. Listed here are 5 suggestions that can assist you conduct these trainings effectively:
- Customise the coaching supplies: Handle the distinctive safety considerations of your group and canopy subjects like knowledge encryption, entry controls, authentication programs, and knowledge privateness guidelines.
- Emphasize phishing consciousness: Set a portion of the coaching to show workers about phishing threats and the right way to establish and report suspicious emails, hyperlinks, or attachments. Train them the right way to confirm the sender’s handle and URL.
- Encourage sturdy password practices: Present recommendations on the right way to create advanced passwords and use password administration instruments. Emphasize the necessity to change passwords regularly to cut back the danger of credential-based assaults.
- Practice staff on safe knowledge dealing with practices: Encourage staff to reduce the usage of private accounts for work-related actions and report any suspicious or unlawful entry to delicate knowledge as quickly as attainable.
- Present common updates and reinforcement: Schedule common cybersecurity consciousness programs, workshops, or newsletters to strengthen key rules, present latest safety incidents or developments, and supply on-line security suggestions.
Right here’s a peek on the cybersecurity coaching guidelines from our template:

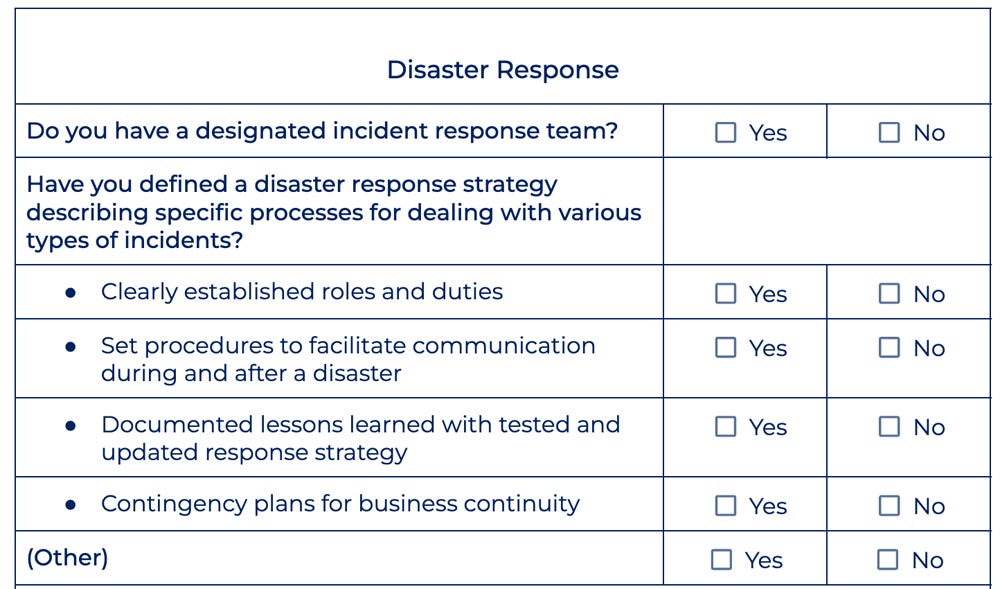
Catastrophe Response
Creating a catastrophe response technique contributes to efficient threat administration towards cyberattacks. Test cybersecurity authorities’ suggestions and develop a plan that features preventive measures, incident response strategies, and communication methods. This methodology prepares you for an assault and facilitates efficient coordination throughout conditions of disaster. It additionally minimizes potential damages, safeguards property, and sustains enterprise continuity.
Inquiries to Reply
To look at your catastrophe response preparedness, verify the next:
- Is there a chosen incident response crew that’s educated and outfitted to hold out the response plan successfully?
- Is there an outlined catastrophe response technique describing particular processes for coping with numerous sorts of incidents?
- Are roles and duties clearly established within the response plan?
- Are there programs in place to facilitate communication and cooperation throughout and after a catastrophe?
- Has the response technique been examined and up to date regularly, making an allowance for classes realized?
- Are contingency plans in place for enterprise continuity throughout and after a catastrophe?
Methods to Obtain Catastrophe Response Preparedness
A very good catastrophe response technique mitigates the affect of safety incidents and operation disruptions. Conduct an environment friendly catastrophe response plan with these strategies:
- Determine important apps and knowledge: Carry out a radical evaluate to prioritize the relevance of every utility and knowledge set based mostly on issues similar to enterprise affect, regulatory compliance, and shopper expectations.
- Implement redundancy and backup procedures: Use redundant SaaS or different service suppliers to cut back single factors of failure and unfold your threat publicity. Backup essential knowledge and configurations regularly to a secure distant location.
- Create thorough incident response plans: Outline roles and duties for key workers, set up communication channels, and doc escalation procedures. Conduct common tabletop workouts to evaluate its effectiveness.
- Deploy steady monitoring and alerts: Arrange alerts and notifications for potential safety points similar to unauthorized entry, knowledge breaches, or service outages. Spend money on options that automate menace detection and response procedures.
- Develop clear communication and coordination protocols: Outline communication routes, escalation paths, and key stakeholders’ factors of contact to foster efficient collaboration. Preserve communication for menace intelligence and sharing incident particulars.
Right here’s a preview of the catastrophe response part included in our template:
Coverage Analysis & Updates
Lastly, a retrospective examination of cyber occurrences informs modifications to safety strategies, processes, coaching, and insurance policies. Organizations can enhance their safety by recognizing flaws and classes realized. This iterative course of helps them stay adaptable and strong to evolving cyberthreats, at all times enhancing their safety posture to successfully decrease dangers.
Inquiries to Reply
Assess your present insurance policies and wishes for updates based mostly on the questions beneath:
- Has a proper framework been established for conducting retrospective evaluation of cyber incidents?
- Are detected gaps and classes realized from the evaluation documented and addressed in safety measure updates?
- Do safety processes, procedures, coaching, and insurance policies get reviewed and up to date regularly?
- Is there a devoted individual or crew accountable for overseeing the updating of processes?
- Are safety updates efficiently disseminated to vital stakeholders?
- Are there programs in place to trace and monitor the deployment of modifications to ensure consistency?
Methods to Carry out Coverage Analysis & Updates
When doing all your coverage analysis and updates, set up system protocols based mostly on classes realized and plan for any modifications. Beneath are some tips on the right way to conduct coverage evaluation and updates successfully:
- Doc incident particulars: Embody the character of the assault, the programs or knowledge that had been affected, the timeline of occasions, and the response steps carried out. Collect suggestions from all stakeholders, together with IT, safety, and enterprise departments.
- Conduct an exhaustive root trigger evaluation: Examine all technical and human causes that contributed to the incident, similar to software program vulnerabilities, misconfigurations, insider threats, or a scarcity of safety consciousness.
- Consider the effectivity of present safety protocols: Determine any gaps within the group’s safety posture disclosed by the incident, and see if present measures had been correctly carried out. Decide if extra controls should be carried out.
- Determine factors of enchancment based mostly on classes realized: Perform corrective actions and remedial efforts to shut safety gaps, tighten controls, and lift safety data and readiness throughout the enterprise.
- Replace safety protocols, coaching, and insurance policies: Assess the timeliness and efficacy of incident detection, containment, eradication, and restoration operations, in addition to the gaps in communication. Determine methods to streamline and automate your procedures.
Right here’s a snippet of the coverage analysis and updates portion of our guidelines:

Backside Line: Create a Strong SaaS Safety Guidelines
Following the procedures outlined above establishes the groundwork for a stable safety posture, together with menace safety, regulatory compliance, and knowledge continuity. SaaS safety necessitates continued vigilance. There needs to be steady coaching, testing, and monitoring to be able to effectively adapt to rising cybersecurity threats whereas sustaining an optimum stage of safety.
Evaluation your identification and entry administration (IAM) methods, amongst different safety strategies as prescribed by SaaS {industry} requirements, to safeguard knowledge integrity, availability, and privateness successfully.
[ad_2]


