[ad_1]
Knowledge loss prevention (DLP) refers to a set of safety options that establish and monitor data content material throughout storage, operations, and networks. DLP options assist detect and forestall potential information publicity or leaks. They apply insurance policies dynamically, handle enterprise information rights, and automate information processes to successfully shield delicate data. An efficient DLP answer supplies the safety staff an entire visibility of their networks.
To find out if the DLP answer is right in your group, discover the way it works, its advantages, finest practices, deployment concerns, and dependable suppliers accessible in the marketplace. Understanding these components permits you to make knowledgeable choices when adopting a DLP answer in your cybersecurity methods.
How Knowledge Loss Prevention Works in 10 Steps
The efficient implementation of knowledge loss prevention encompasses correct setup, steady monitoring, real-time information evaluate, prevention measures, anomaly detection, information visibility, incident response, contextual evaluation, and strengthened prevention and remediation procedures. DLP integrates procedures, expertise, and other people to successfully detect and forestall delicate information leaks.
The ten steps outlined beneath present how information loss prevention works.
1. Provoke Setup & Configuration
This step requires putting in and configuring the DLP software on the group’s community infrastructure. This additionally entails integrating it with current cybersecurity measures reminiscent of firewalls, endpoint safety instruments, monitoring options, and antivirus software program to supply complete information safety and menace mitigation capabilities.
2. Monitor Knowledge Streams
DLP instruments constantly monitor information throughout the group’s community. This contains scanning information in transit between gadgets or networks, in addition to information at relaxation saved on servers, endpoints, or within the cloud, to make sure complete protection for detecting and stopping potential information breaches or unlawful entry.
3. Assessment Knowledge in Actual-Time
DLP options carry out instantaneous evaluation of knowledge packets or recordsdata as they’re noticed. They scan content material for delicate data reminiscent of PII, monetary information, or mental property, permitting for fast identification and response to any information breaches or unauthorized entry, therefore enhancing the enterprise’s community safety and general compliance initiatives.
4. Implement Prevention Measures
To forestall information loss, the DLP’s measures require the answer to reply shortly when suspicious exercise or unlawful entry is detected. Blocking information entry, limiting person privileges, or terminating suspicious processes are all examples of actions that may be taken to bolster safety requirements and cut back the chance of knowledge breaches or unauthorized disclosures.
5. Detect Anomalous Exercise
DLP programs use AI and ML to shortly detect irregular habits. This pertains to deviations from typical information utilization patterns, odd entry makes an attempt, and suspicious information transfers, permitting for preemptive motion to mitigate potential safety issues and shield delicate data from unauthorized entry or information breaches.
6. Improve Knowledge Visibility
DLP programs present full insights into information consumption and movement throughout the group’s community, which helps to enhance information visibility. This elevated visibility facilitates early detection of potential community safety assaults or information breaches and empowers calculated measures to mitigate dangers and efficiently safe delicate data.
7. Facilitate Incident Response
Within the occasion of a safety incident or breach, the DLP answer displays and stories on information entry and motion. This supplies safety groups with crucial insights into investigating and mitigating the injury. DLP permits speedy and efficient response behaviors to include the incident and keep away from additional compromise of delicate data.
8. Analyze Safety Occasions
DLP options assist the safety staff interpret high-risk exercise or habits by analyzing the kind and context of safety occasions. This system improves consciousness of underlying dangers, permitting for extra knowledgeable decision-making to successfully deal with safety threats and prioritize mitigation actions, finally strengthening the group’s resilience to attainable information breaches.
9. Conduct Remediation Actions
If a safety occasion occurs, DLP options assist to handle the issue by figuring out the basis trigger and advising related steps. This entails placing corrective measures in place to cut back future dangers, thereby encouraging a proactive strategy to defending delicate information and adhering to regulatory compliance requirements contained in the group.
10. Strengthen Risk Prevention Measures
DLP enhances menace prevention by evaluating high-risk behaviors and delivering its insights to safety professionals. This permits the refining of safety insurance policies, the deployment of recent controls, and the advance of worker coaching applications with a view to successfully cut back potential dangers and shield delicate information from unlawful entry or publicity.
Why Ought to Corporations Put money into Knowledge Loss Prevention?
DLP promotes danger discount and endpoint safety by classifying and monitoring delicate information, detecting and blocking suspicious exercise, automating information classification and compliance administration, and growing menace visibility. This safety strategy assists companies in stopping information breaches, safeguarding delicate data, making certain compliance, and defending towards rising cyberthreats.
Danger Discount & Endpoint Safety
Implementing DLP options lowers the chance of knowledge breaches by defending endpoints and stopping unauthorized entry. This improves general cybersecurity posture, particularly on gadgets which might be delicate to threats. DLP enforces safety rules, protects information, and displays utilization for compliance and danger mitigation.
Delicate Knowledge Classification & Monitoring
DLP supplies delicate information classification and monitoring, making certain regulatory compliance whereas additionally defending mental property and shopper data. DLP detects suspicious exercise in actual time by constantly monitoring information consumption and entry, permitting for proactive danger discount whereas additionally boosting community safety posture and information governance procedures inside companies.
Detection & Blocking of Suspicious Exercise
DLP options use superior detection capabilities to establish and forestall suspicious exercise throughout electronic mail, the net, and detachable storage gadgets. DLP makes use of content material inspection, habits evaluation, and machine studying to detect abnormalities that point out information breaches or coverage violations. When detected, automated response steps, reminiscent of stopping information transmission or producing notifications, keep away from information loss and keep confidentiality.
Automation & Compliance Administration
This DLP functionality ensures accuracy and effectivity in intensive environments. DLP options automate information classification based mostly on insurance policies and rules, using metadata components to precisely establish delicate materials. This real-time safety, together with highly effective reporting and auditing capabilities, makes enterprises simply display compliance.
Improved Visibility & Risk Preparedness
DLP boosts visibility into information entry and utilization, supporting steady menace detection and mitigation. It helps companies spot rising safety traits, person habits patterns, and vulnerabilities by giving detailed insights into information flows, person actions, and safety incidents. With this data, companies can effectively reply to incidents and restrict the implications of knowledge breaches and cyberattacks.
Knowledge Loss Prevention Finest Practices
DLP finest practices make sure that delicate information is correctly recognized, categorised, and guarded. Moreover, educating stakeholders and conducting common safety testing improve general information safety whereas lowering the probability of breaches.
Comply with these finest practices to ascertain a profitable information loss prevention technique:
- Establish and classify delicate information: Label and safeguard delicate information with DLP insurance policies to forestall unauthorized entry or disclosure.
- Use information encryption: Encrypt information at relaxation and in transit to forestall unauthorized entry and protect the confidentiality and integrity of delicate data.
- Safe your programs: Enhance safety by proscribing system entry to licensed customers. This lowers the opportunity of unauthorized information breaches or system compromises.
- Implement DLP in phases: Step by step combine DLP capabilities, aligned with company priorities, to efficiently fulfill information safety necessities over time.
- Implement a patch administration technique: Apply fixes regularly to resolve vulnerabilities and restrict the chance of exploitation by cyberthreats.
- Assign roles: Outline roles for information safety to allow accountability and efficient administration of duties throughout the group’s safety structure.
- Automate and use anomaly detection: Use automation and machine studying to shortly establish and reply to potential safety breaches.
- Prepare stakeholders: Educate your stakeholders and customers to grasp and perform their information safety duties, and promote a tradition of knowledge safety consciousness.
- Set up metrics: Monitor key indicators to find out the effectiveness of your DLP technique. This permits data-driven decision-making and ongoing enchancment of knowledge safety.
- Conduct common testing, audits, and doc adjustments: Carry out audits to validate DLP efficacy. Doc configuration regularly and guarantee its alignment with what you are promoting wants and safety requirements.
DLP Adoption and Deployment Issues
When adopting and deploying an information loss prevention answer, companies should consider funds, compliance, safety wants, scope, trusted companions, staff experience, and extra. Whatever the measurement or trade of the group, an intensive evaluation ensures clean implementation, regulatory compliance, and dependable delicate information safety.
Contemplate these key components:
- Price range: Allocate a funds for a DLP answer that balances long-term usability with affordability. Guarantee that the suitable options meet your safety necessities inside monetary limits.
- Compliance: Combine DLP with governance, danger, and compliance (GRC) options for clean regulatory alignment and efficient regulatory compliance processes throughout the group.
- Safety necessities: Outline safety strategies to guard delicate information, together with mental property and private data. Test if sufficient information safety procedures are in place.
- Scope: Totally assess information places and visibility for complete safety measures. Embody all websites the place delicate information is saved throughout the group’s infrastructure.
- Deployment documentation: Create documentation defining deployment strategies and audit data to facilitate profitable implementation and information switch amongst staff members.
- Roles and duties: Outline particular tasks and roles to ascertain accountability and forestall information exploitation, making certain that every staff member understands their half in information safety.
- Reporting: Make use of reporting instruments to acquire perception into information safety and entry, which is crucial for making certain compliance with guidelines and governance requirements inside the corporate.
- Dependable DLP supplier: Conduct intensive analysis to judge vendor capabilities, scalability, and compatibility together with your present infrastructure. Your vendor answer ought to present full options and help for the implementation course of.
- Group experience and enterprise measurement: Have in mind the product’s complexity and the staff’s abilities to ensure an environment friendly implementation that’s tailor-made to the scale and necessities of the enterprise.
3 DLP Suppliers to Assist Safeguard Your Knowledge
Choose an acceptable information loss prevention answer that meets your group’s particular wants. Usually, this could embrace evaluating their information safety capabilities, integration with present programs, and full regulatory compliance help. Guarantee that their capabilities are tailor-made based mostly on the group’s particular operational atmosphere and objectives.
Discover Forcepoint, Symantec, and Proofpoint — three of our beneficial DLP suppliers listed beneath.

Forcepoint DLP
Forcepoint DLP gives full options for administering world insurance policies throughout all predominant channels, together with endpoint, community, cloud, net, and electronic mail. It supplies established templates, insurance policies, and incident administration that enhance visibility and management over information and work environments. This enables enterprises to effectively deal with the dangers of knowledge loss by safeguarding information wherever it’s accessed or stored.
Forcepoint DLP gives a 30-day free trial. For detailed pricing data, contact Forcepoint’s gross sales staff.
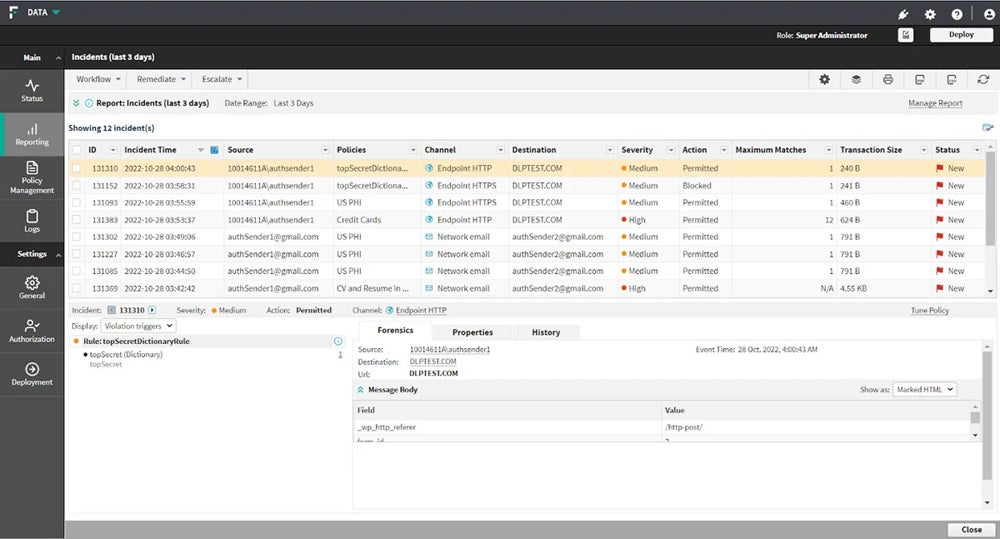

Symantec DLP
Symantec Knowledge Loss Prevention, acquired by Broadcom, is right for shielding giant networks. It contains Symantec DLP Core and DLP Cloud, which give cloud connections for net gateways and cloud entry safety dealer (CASB) controls. It gives full safety for companies, specializing in information safety throughout huge networks, information integrity, and regulatory compliance.
To request for a pricing quote, contact Broadcom’s gross sales staff or their licensed distributors.


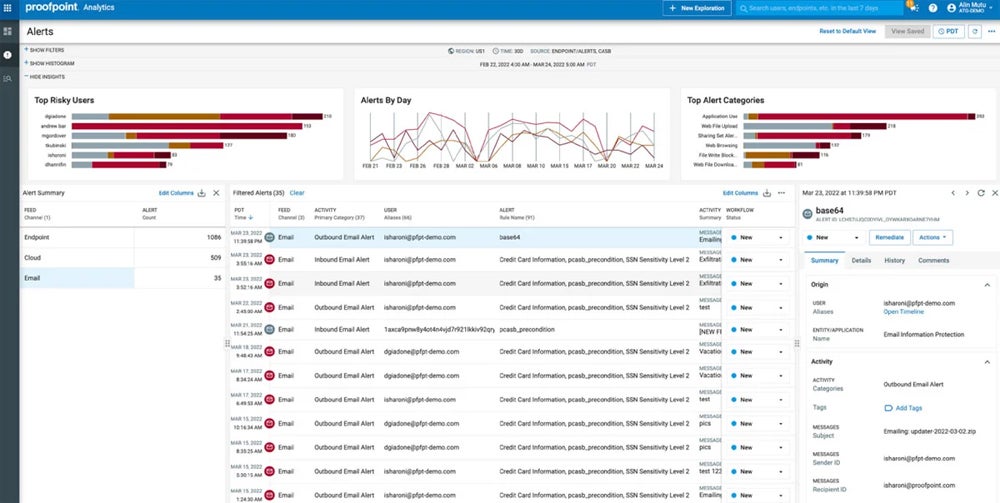
Proofpoint Enterprise DLP
Proofpoint’s Enterprise DLP platform excels in standalone electronic mail safety, together with Endpoint and E mail DLP options. With a people-centric strategy, it combines content material, behavioral, and menace consciousness to supply granular visibility into information interactions. With capabilities together with real-time detection, prevention, and response to information loss conditions, it delivers sturdy safety throughout endpoints and electronic mail channels.
Entry Proofpoint Enterprise DLP’s free trial and pricing data by contacting their gross sales staff.
For the great record of our beneficial suppliers, together with their pricing, choices, and extra, consult with our purchaser’s information on the prime information loss prevention options.
Backside Line: Safe Delicate Property with Knowledge Loss Prevention
Organizations could classify, monitor, and safe delicate information throughout endpoints and networks by setting up efficient DLP options. These options present proactive detection and response capabilities. DLP makes use of highly effective analytics and machine studying algorithms to detect uncommon actions and coverage violations in actual time, permitting safety groups to take speedy motion to forestall information loss or unlawful entry.
Whereas DLP options play an important position in information safety, they alone can’t guard your complete system’s safety. Complement DLP with instruments like EDR and SIEM so you may kind a holistic safety framework that reduces dangers and protects your crucial data.
[ad_2]


