[ad_1]
Internet software safety testing goals to detect, stop, and tackle safety vulnerabilities inside internet purposes. Flaws in internet software coding accounted for 72% of the recognized vulnerabilities. This analysis includes scrutinizing the code, structure, and deployment atmosphere to evaluate the safety posture of the purposes. Safety testing for internet software may be executed manually or by way of automation, with the target of uncovering potential dangers equivalent to cross-site scripting (XSS), SQL injection, buffer overflow, and malicious file execution.
The first goal of internet software safety testing is to confirm that internet purposes are safe and devoid of exploitable vulnerabilities that might lead to knowledge breaches or different malicious assaults.
Why is Internet Utility Safety Testing Essential?
Internet software safety testing performs an necessary function within the general safety technique of organizations. With the growing adoption of cloud know-how by companies, guaranteeing the safety of internet purposes is paramount to safeguarding knowledge and sustaining compliance with business laws. Given the vulnerability of internet purposes to malicious assaults, organizations should conduct common testing and implement protecting measures to mitigate potential threats.
The need for safety testing for internet purposes stems from the publicity of those purposes on public networks, making them accessible to anybody with web connectivity. This accessibility will increase the chance of attackers exploiting vulnerabilities inside internet purposes to achieve unauthorized entry to delicate info or disrupt operations. Furthermore, internet purposes usually function entry factors into different methods, equivalent to databases or servers, amplifying the potential influence of safety breaches if not adequately secured.
Advantages of Internet Utility Safety Testing to Organizations
Enchancment in Safety
Conducting internet software safety testing permits companies to establish each present vulnerabilities and potential dangers throughout the system, empowering them to take proactive measures to mitigate these points. This proactive method can considerably decrease the chance of pricey knowledge breaches and different malicious assaults.
Enhanced Repute
Companies that prioritize safety and recurrently check internet purposes display their dedication to safeguarding clients’ knowledge and upholding a optimistic status, which in flip enhances belief amongst clients.
Value Financial savings
Early detection of potential points by way of internet software safety testing permits companies to avoid wasting prices by stopping the necessity for costly repairs or replacements ensuing from malicious assaults or knowledge breaches. Moreover, conducting internet software safety testing assists organizations in assembly business laws, thereby avoiding substantial fines related to non-compliance.
Enchancment in Efficiency
Constantly testing internet purposes can reveal areas of efficiency lag or inefficient processes inflicting delays or errors. This perception permits companies to implement needed enhancements that improve general efficiency and person expertise.
Elevated Effectivity
Internet software safety testing aids companies in figuring out system weaknesses, enabling them to streamline processes and improve effectivity all through the group by eradicating pointless steps or redundant duties.
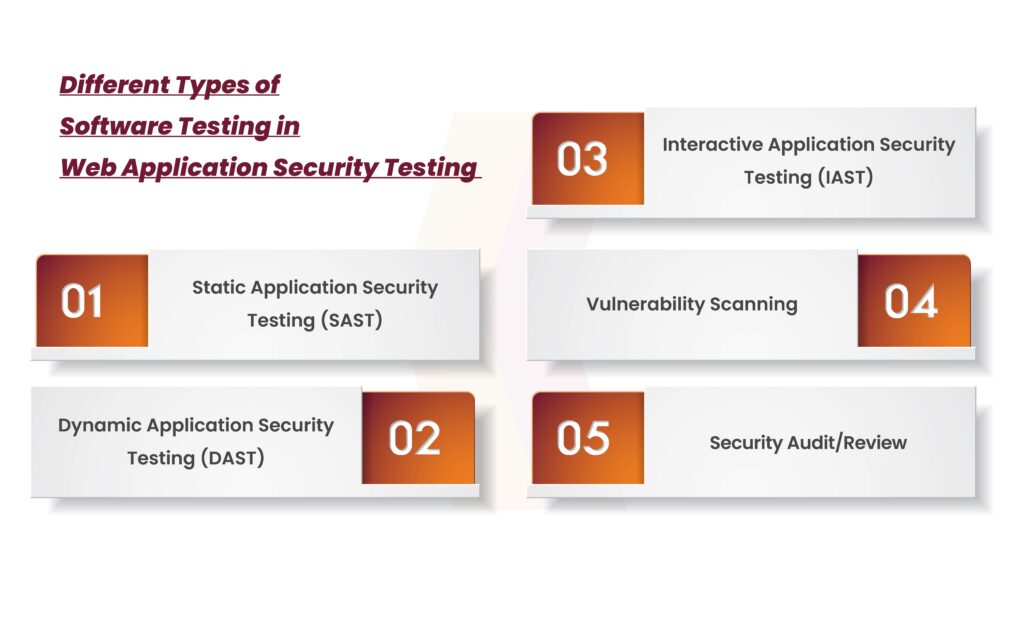
Completely different Varieties of Software program Testing in Internet Utility Safety Testing
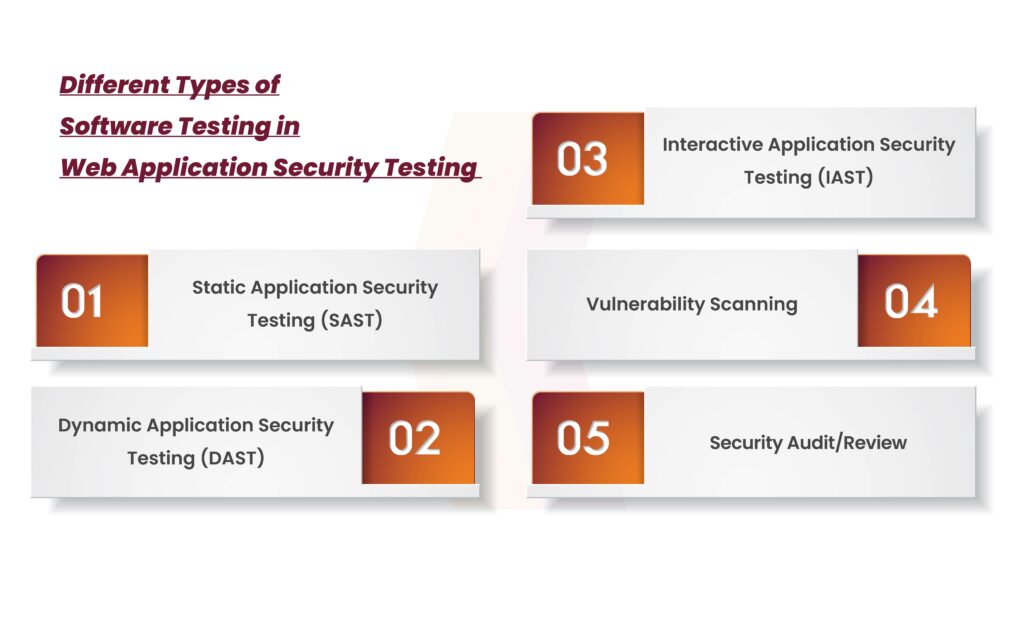
Static Utility Safety Testing (SAST)
This testing technique is called White Field Testing, permitting builders to detect safety vulnerabilities throughout the supply code of an software within the early phases of the software program growth life cycle. Through the use of this method, builders can confirm that the appliance complies with coding tips and requirements.
Dynamic Utility Safety Testing (DAST)
This method entails injecting malicious knowledge into the software program to simulate SQL injection and XSS assaults, aiming to disclose prevalent safety vulnerabilities. It’s a type of black field or gray field safety testing that empowers testers to pinpoint potential weaknesses in internet purposes.
Interactive Utility Safety Testing (IAST)
This technique integrates facets of each Static Utility Safety Testing (SAST) and Dynamic Utility Safety Testing (DAST), using an Interactive Utility Safety Testing (IAST) agent embedded throughout the software to conduct real-time evaluation. Our intensive community contains substantial expertise in offering safety testing providers and figuring out vulnerabilities for shoppers throughout numerous domains.
Vulnerability Scanning
This testing course of makes use of automated software program to examine software vulnerabilities, conducting assessments for points equivalent to cross-site scripting, command injections, and extra inside internet purposes.
Penetration Testing
Penetration testing, generally often known as pen testing, is a safety evaluation carried out by licensed cyber-security professionals to establish and exploit vulnerabilities inside an software. Various kinds of penetration testing embody Inner, Exterior, Black Field, and Gray Field approaches.
Technique of Internet Utility Safety Testing
Internet software safety testing encompasses a number of important procedures geared toward figuring out vulnerabilities and sustaining a safe on-line atmosphere. Let’s take a look on the elementary processes:
Info Gathering
It’s a very important side of internet software safety testing. Throughout this preliminary stage, the main focus is on totally understanding the goal software. Numerous testing strategies contain conducting search engine reconnaissance and discovery to establish potential info leaks, enumerate purposes, and fingerprint apps to find out the entry factors for the appliance.
Authentication Testing
It includes verifying the digital identification of a communication sender. The most typical instance is the login course of. Testing the authentication system requires understanding how the process works and leveraging that understanding to bypass the authentication mechanism. Examples of points embody weak lockout mechanisms, bypassing authentication schemes, vulnerabilities associated to browser caching, and inadequate authentication in different channels.
Authorization Testing
After efficiently authenticating with clear credentials linked to particular roles and privileges, the penetration tester will proceed to validate authorization. This course of includes checking for insecure direct object references, potential privilege escalation, and bypassing permission guidelines. Permission testing entails understanding how the authorization system capabilities and utilizing this data to navigate round it successfully.
Testing for Error Dealing with
In the midst of an online software penetration check, testers usually encounter a spread of error codes generated by purposes or internet servers. These points may be revealed by way of particular requests crafted manually or utilizing instruments. Error codes are priceless to penetration testers as a result of they supply insights into databases, safety vulnerabilities, and different technical facets related to on-line purposes. Analyzing error codes and stack traces are just some examples of how testers leverage this info.
Consumer-Facet Testing
In the midst of an online software penetration check, testers usually encounter a spread of error codes generated by purposes or internet servers. These points may be revealed by way of particular requests crafted manually or utilizing instruments. Error codes are priceless to penetration testers as a result of they supply insights into databases, safety vulnerabilities, and different technical facets related to on-line purposes. Analyzing error codes and stack traces are just some examples of how testers leverage this info.
Reporting
The objectives of the reporting part embody presenting, rating, and prioritizing findings, and offering undertaking stakeholders with a concise, actionable report accompanied by related knowledge. At Kratikal, we view this stage as probably the most important and place important emphasis on successfully speaking the importance of our findings and providers.
How Does Safety Testing for Internet Functions Mitigate Danger for Organizations?
Safety testing for internet purposes is important for organizations to mitigate cyber threats and shield digital property. This testing includes assessing internet software design, performance, and codebase to make sure resilience towards assaults and compliance with business laws. Its goals embody figuring out and mitigating vulnerabilities like XSS and SQL injection, stopping knowledge breaches, guaranteeing compliance with laws, averting damaging publicity from breaches, and repeatedly enhancing safety posture by way of proactive danger evaluation and mitigation.
Guide a Free Session with our Cyber Safety Consultants

Conclusion
Safety testing for internet software is crucial for organizations to mitigate cyber threats, shield digital property, and guarantee compliance with business laws. By figuring out and addressing vulnerabilities equivalent to XSS, SQL injection, and authentication points, safety testing helps stop knowledge breaches and different malicious assaults. Furthermore, safety testing enhances organizational status by demonstrating a dedication to safeguarding buyer knowledge and sustaining compliance. Common testing and enchancment in safety posture by way of numerous testing strategies allow organizations to remain forward of evolving threats and guarantee a safe on-line atmosphere. General, investing in internet software safety testing is important for organizations to successfully handle and mitigate dangers related to cyber threats.internet software safety testing is crucial for organizations to mitigate cyber threats, shield digital property, and guarantee compliance with business laws.
By figuring out and addressing vulnerabilities equivalent to XSS, SQL injection, and authentication points, safety testing helps stop knowledge breaches and different malicious assaults. Furthermore, safety testing enhances organizational status by demonstrating a dedication to safeguarding buyer knowledge and sustaining compliance. Common testing and enchancment in safety posture by way of numerous testing strategies allow organizations to remain forward of evolving threats and guarantee a safe on-line atmosphere. General, investing in internet software safety testing is important for organizations to successfully handle and mitigate dangers related to cyber threats.
Kratikal a CERT-In empanelled auditor gives companies with a variety of cybersecurity options & providers. Trusted by over 450+ SMEs and Enterprises worldwide, Kratikal delivers sturdy cybersecurity options. We’re one of many fastest-growing companies dedicated to safeguarding firms and organizations of various sectors, for example, SaaS, Fintech, Healthtech, Govt., and so on., towards cyber dangers.
FAQ
- Q1: What Is The Commonplace Adopted For Internet Utility Testing?
Ans: The VAPT of internet purposes usually adheres to business safety frameworks equivalent to OWASP Prime 10, SANS 25, NIST, and different related requirements.
- Q2: What Does A Internet Utility Safety Testing Report Consist Of?
Ans: The report defines goals and gives detailed danger descriptions for every vulnerability discovered, together with Proof-of-Idea (POC) proof. Vulnerabilities are categorized by severity ranges (Crucial, Excessive, Medium, Low, Data) based mostly on their CVSS rating, with suggestions for mitigation included.
The submit What’s Internet Utility Safety Testing? appeared first on Kratikal Blogs.
*** This can be a Safety Bloggers Community syndicated weblog from Kratikal Blogs authored by Shikha Dhingra. Learn the unique submit at: https://kratikal.com/weblog/what-is-web-application-security-testing/
[ad_2]