[ad_1]

Within the final decade, safety scanners have developed to determine widespread vulnerabilities like SQL injections.
However that’s simply not sufficient anymore.
In 2024, knowledge leaks in purposes come from exploiting enterprise logic flaws. Within the subsequent few years, purposes will develop in measurement and quantity too quick, so the true benefit will come from having the ability to discover enterprise logic vulnerabilities at scale.
The rising variety of safety instruments modified the way in which we secured our purposes lately. The following paragraphs could properly change the way in which we safe our purposes within the years to return.
Static evaluation and Nuclei templates usually are not sufficient
Within the safety trade, we have witnessed a big inflow of safety instruments lately, providing options for numerous elements like Cloud safety testing, IaC, Container scanning, ASPM, Secret scanning, SAST, DAST.. . You title it.
We’ve closely shifted in the direction of securing purposes earlier than their launch in manufacturing and serving to builders write safer code. Particularly for the latter – tooling to assist builders write safer code has improved. We’re not used to lengthy scan occasions or instruments trying like security-oriented linters, turning complete IDE in purple for little or no worth.
SCA instruments like Snyk have appeared to make sure the packages we use don’t include any vulnerabilities.
Static evaluation instruments, which discover injections and different dangerous coding practices, have grow to be extra developer-friendly and accessible with options like Semgrep.
Easy instruments to check identified vulnerabilities on net purposes even have appeared, with some open-source ones like Nuclei being superb at it.
But, it didn’t cease knowledge leaks from taking place. Let’s be sincere, static instruments include a number of limitations. Simultaneous to these enhancements within the trade, from 2015 to 2022, knowledge breaches within the healthcare trade rose greater than twofold, from 270 to 707 per 12 months.
How is that potential? How can we get higher tooling to jot down safe code and discover software program vulnerabilities, and but our purposes are getting increasingly more hacked?
There are two explanations for this:
- Our apps get safer, however we expose increasingly more of them to the web. Exponentially extra, really.
- Even when we obtained higher at discovering technical vulnerabilities, nothing in our present tooling, from Snyk, to Semgrep to Nuclei, can discover something associated to enterprise logic flaws and entry management vulnerabilities. As purposes get extra advanced, with extra options, consumer roles, and entry management guidelines, these flaws grow to be more and more widespread. As an illustration, Gitlab’s API has entry management vulnerabilities uncovered nearly each month of the 12 months now.
Why is it onerous to check enterprise logic at scale?
Discovering enterprise logic flaws at scale is difficult from a technical perspective. Let’s say you may have an software that enables your customers to entry their financial institution accounts.
The appliance relies on an API with a GET /consumer/[id]/account route.
One of the apparent enterprise logic flaws could be to overlook to implement correct entry management on the route, in a manner that enables any authenticated consumer to entry info from different accounts simply by changing the ID within the URL.
GET /consumer/{victim_account_id}/account => 200 OK
This kind of vulnerability is named a BOLA, or Damaged Object Degree Entry Management, and it’s part of the ten most typical vulnerabilities in API in keeping with OWASP.
Now, suppose that you just need to write a take a look at utilizing Nuclei to make sure that consumer A can not entry consumer B’s account:
requests:
- technique: GET
path:
- "{{BaseURL}}/consumer/{{victim_account_id_1}}/account"
- "{{BaseURL}}/consumer/{{victim_account_id_2}}/account"
headers:
Authorization: "Bearer {{token_user_A}}"
matchers-condition: and
matchers:
- sort: standing
standing:
- 200
Whereas this would possibly work, it has a number of necessary limitations:
- To write down this take a look at, you even have to explain precisely the vulnerability. In follow, most vulnerabilities seem in instances the builders didn’t take into consideration within the first place.
- This assessments just one potential vulnerability on a single route of your software. You’ll have to take into consideration all potential exploitations in all routes of your software and write a take a look at for every if you wish to guarantee correct testing.
- This take a look at depends on the variables
victim_account_id_1andvictim_account_id_2present within the database throughout your assessments. If the database evolves, if any route sample adjustments, your take a look at turns into out of date, and you have to replace it accordingly. And what’s worse than writing assessments? You bought it, sustaining assessments.
Consequently, writing and sustaining a correct set of enterprise logic safety assessments for an API and an software is proportional to (variety of options) x (variety of potential vulnerabilities) x (variety of fixture parameters)
Let’s attempt to consider what which means for an average-sized software:
- As for the variety of options, it’s proportional to the variety of API routes. From our expertise at Escape, most purposes common 100 routes at the very least.
- Sometimes, vulnerabilities from one net software to a different are fairly comparable. OWASP’s Frequent Weak spot Enumeration (CWE) undertaking enumerates the potential defects that result in vulnerabilities showing in software program purposes. Having assessments for his or her OWASP CWE High 25 is sort of an excellent place to begin for making certain correct safety, so the variety of vulnerabilities to check for could be 25.
- Lastly, in the case of fixtures, let’s take the speculation that routes have on common 5 parameters and that our fixtures include 2 totally different values per parameter. That’s 10 fixtures per route.
So, making certain correct enterprise logic safety testing for our software would require writing and sustaining 25 assessments x 100 routes x 10 fixtures = 25,000 assessments for an average-sized software. That’s completely impractical.
Introducing Escape guidelines: Enterprise logic safety testing reinvented
What if as an alternative of specifying our assessments, we may simply write easy guidelines like “No admin routes must be accessible to unauthenticated customers” or “No consumer ought to be capable to entry one other account than his personal”, after which let a program generate take a look at instances for us in keeping with our API construction and what’s in our database?
That is what we predict safety engineers deserve. So we determined to create it. There are three issues we did to make this potential:
- Generalise assessments throughout API routes. This may be achieved fairly simply utilizing templating like deciding on “all routes containing /admin” or “All routes that manipulate private knowledge” as an alternative of writing one take a look at per route. The checklist of routes and parameters may be fetched from numerous simply accessible knowledge sources: OpenAPI/Swagger information, Postman collections, or reside site visitors logs.
- Routinely fill the API route parameters with fixtures that exist within the database. This half is the toughest, technically, and it took us two years of analysis to create an answer that we known as “Suggestions Pushed API exploration”.
- Invent a easy language or syntax to explain the take a look at with route matchers, customized payloads, and an assertion system. We determined to go for a YAML-like syntax for simple take a look at writing.
That is how Escape guidelines have been born, a easy but highly effective YAML based mostly language to jot down API enterprise logic assessments which might be agnostic of the precise API routes and fixture knowledge.
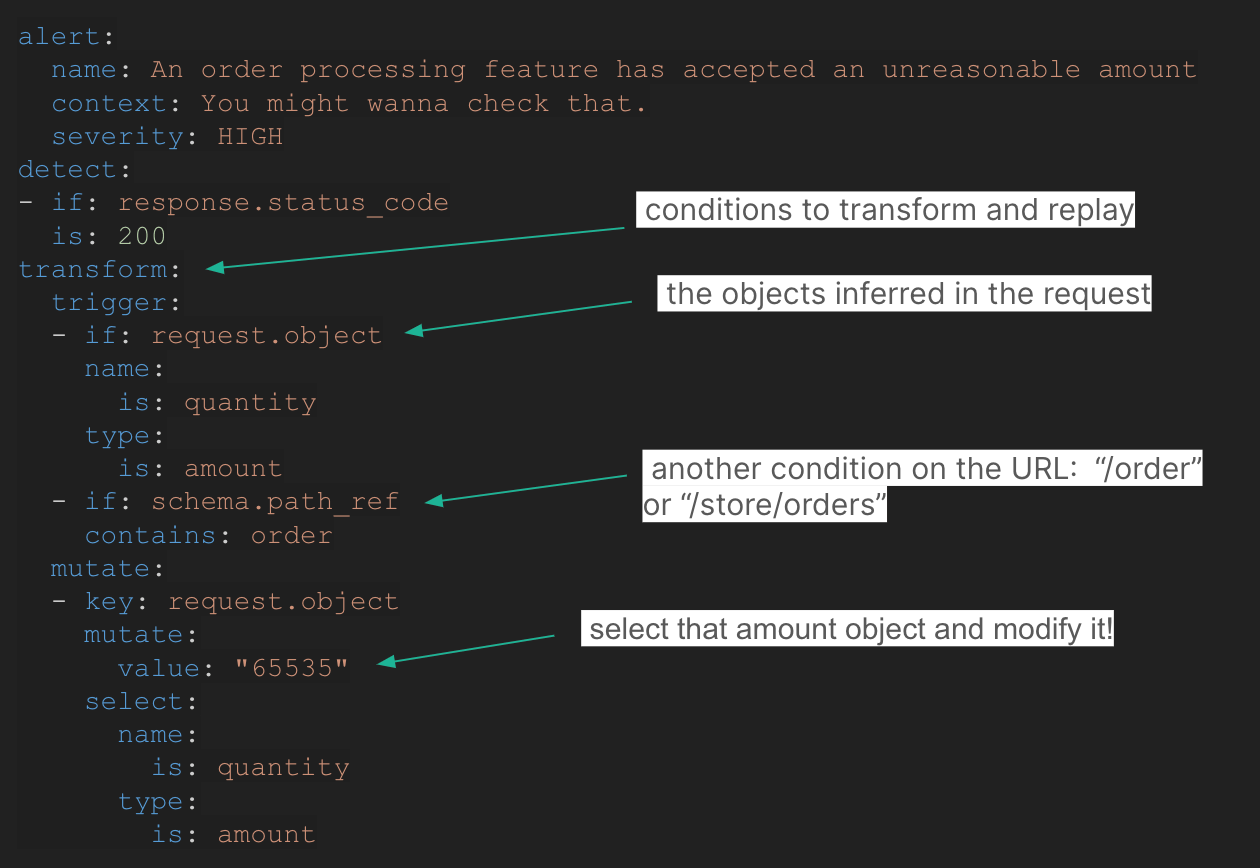
Tailor-made to your APIs, zero upkeep required
Till now, safety engineers needed to steadiness operating generic, low-configuration safety scans versus tailor-made assessments that required quite a lot of upkeep over time. That is over because of Escape’s contextualized rule engine.
Regardless of their capability to take a look at the enterprise logic, Escape guidelines require zero upkeep. They don’t should be tied to specific routes or HTTP parameters. They adapt to the evolution of your present APIs and new APIs with out the necessity to preserve the ruleset. By design, they’re resilient to evolving database fixtures in improvement environments.
With Escape guidelines, you’ll be able to code a take a look at as soon as and overlook about it, it would run on all of your APIs and all of your API updates, be it in CI/CD, improvement, or manufacturing surroundings.
Designed for maximizing the ROI of your Bug Bounty and Pentest applications
Whereas bug bounty applications and pentests are probably the most in-depth safety evaluation accessible in the present day, the ultimate test between an software and the wild web, they’ve an inherent limitation: they’re sluggish and time limit.
In most organizations, nothing prevents a junior developer from implementing once more the identical situation that had been detected by the bug bounty program and stuck years in the past.
As highly effective as they’re, pentests and bug bounties depend upon the builders’ reminiscence, and any turnover could make the identical points seem repeatedly.
Escape guidelines are altering this. Escape guidelines are so highly effective that they’ll describe and detect a variety of assault eventualities from the fundamental SQL injections or SSRF too, particularly, environment friendly for advanced multi-steps and multi-user entry management issues like tenant isolation points.
Consequently, most of what an API pentest or a bug bounty program can discover may be rapidly applied as an Escape rule for quick detection at scale and within the CI/CD.
With Escape guidelines, you’ll be able to capitalize in your pentest and bug bounty applications, implementing a brand new enterprise logic take a look at each time a brand new situation is manually detected, stopping them from reappearing elsewhere and in the end making a resilient group.
Again within the outdated days, safety engineers have been targeted on their particular purposes. However on this period, sharing information is totally obligatory. And was even sought by among the safety engineers we talked with. Think about you’re operating an e-commerce platform, who stated {that a} enterprise logic take a look at for one couldn’t be reused for one more?
Relaxation assured, we have been aware of that reality when launching Escape guidelines. Whereas many safety instruments solely have in-app functionalities, we created a GitHub repository with all customized safety assessments developed by the neighborhood and accessible to everybody.
Utilizing it, safety engineers from the neighborhood can collaborate on guidelines, create new ones, and share their very own with their friends to create a community impact of detections.
Whether or not you might want to discover it by vulnerability sort or know-how, it’s all there.
Welcome to the world the place enterprise logic vulnerabilities can not escape
Within the new web order, all the things is an API and each API is in danger. Enterprise logic flaws in APIs are have grow to be the most typical safety points discovered by bug bounties and are overwhelmingly current in crucial knowledge leaks.
Till now, it was very onerous for safety engineers to search out them at scale, as a result of they’re tied to the applying’s customized logic, not like vulnerabilities in dependencies and code smells discovered by SCA and SAST.
Due to Escape guidelines, our new easy-to-use but highly effective YAML-based language, we now reside in a world the place safety engineers can rapidly detect enterprise logic stage vulnerabilities at scale in all their APIs and purposes, in all their environments, at zero upkeep price.
Even higher, they’ll share their enterprise logic flaw detection guidelines with the neighborhood and collaborate to create extra resilient purposes and organizations. With Escape guidelines, safety engineers are able to safe an web the place API sprawl is a actuality.
💡 Wish to discover extra about customized safety assessments? Take a look at the next articles and movies:
- Workshop: Methods to write customized safety assessments on your APIs:
*** This can be a Safety Bloggers Community syndicated weblog from Escape – The API Safety Weblog authored by Tristan Kalos. Learn the unique publish at: https://escape.tech/weblog/new-approach-to-identify-business-logic-flaws/
[ad_2]


