[ad_1]

Organizations are continually searching for methods to enhance their defenses towards enterprise logic vulnerabilities. These vulnerabilities, typically troublesome to detect, can result in vital safety breaches if left unchecked. To deal with this problem, we have launched a brand new characteristic inside our platform that empowers groups to create {custom} enterprise logic exams for APIs, enabling the identification and remediation of safety flaws at scale.
To clarify how one can get began with {custom} safety exams, we held a hands-on workshop for our group. Right here’s the video if you happen to’d like to look at it on YouTube:
On this article, we’ll cowl the important steps we went by way of through the workshop. These steps are essential to contemplate when if you wish to begin writing your {custom} safety exams with Escape.
The problem of conventional enterprise logic exams
Conventional enterprise logic exams are sometimes inflexible, requiring intensive upkeep and hard-coded knowledge. This strategy shouldn’t be solely time-consuming but in addition fails to adapt to adjustments in APIs or underlying databases. Consequently, these exams rapidly grow to be out of date, leaving APIs weak to new threats.
To beat these limitations, we have developed a brand new language that simplifies the creation of enterprise logic exams. This language is designed to be user-friendly for each safety engineers and builders, permitting for the environment friendly testing of APIs.
How the {custom} check language works
Our {custom} check language consists of a number of key parts:
- Alert Block: That is the place you outline the character of the vulnerability and its severity. This block is informative, describing the vulnerability for person suggestions.
- Seed Block: This lets you information the scanner to check particular points of your API, akin to hot-starting a scan. Drive a go to to a selected endpoint/area.
- Detect Block: The core of the check, the place you may interpret the ultimate request/response and the place the situations for triggering an alert are specified.
- Remodel Block: Right here, you may specify how one can modify and resend a request/response based mostly on sure triggers, corresponding to detecting an object or a selected route.
Combine the inference engine to supply context to the manipulated knowledge, thus making it accessible to the testing language.
The language is constructed on YAML, making it accessible and simple to make use of. It consists of quite a lot of operators and helpers that help you give attention to the enterprise logic slightly than the intricacies of the API’s technical implementation.
Actual-world purposes and advantages
The pliability of our {custom} check language allows you to handle a variety of vulnerabilities, together with tenant isolation points, mass task vulnerabilities, and misconfigurations in frameworks like Spring Boot. It additionally permits for the simple replication of pen check findings, guaranteeing that vulnerabilities are usually not reintroduced in future updates.
Listed here are a number of examples from the presentation:
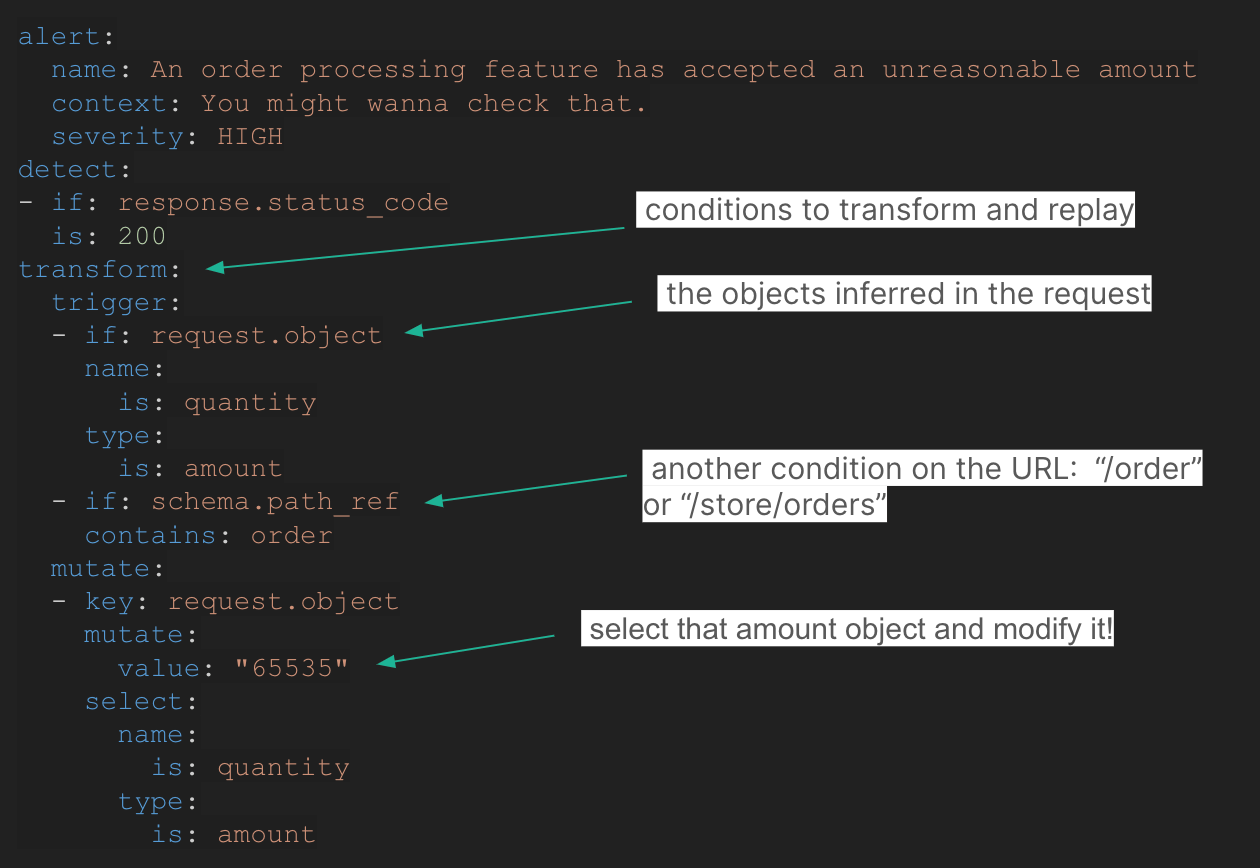
Order processing characteristic vulnerability
A typical vulnerability in e-commerce platforms is the acceptance of unreasonable order portions. A {custom} check will be created to detect if an API endpoint accountable for processing orders permits for the submission of excessively massive portions. By mutating the amount parameter to an abnormally excessive worth and checking the response, the check can determine if there’s a lack of correct validation in place:
Mass Project Vulnerability
Mass task vulnerabilities happen when an API endpoint accepts further, sudden fields within the request payload, doubtlessly resulting in unauthorized adjustments. A {custom} check can detect this by including sudden properties to the request physique, corresponding to an “isAdmin” flag set to true, and observing if the API improperly processes these properties:
alert:
title: An object that incorporates a job property accepted a mass task payload
context: You may wanna verify that.
severity: HIGH
rework:
set off:
- if: request.physique.json
jq: '. | keys[] | incorporates("position")'
mutate:
- key: request.physique.json
jq: '.isadmin=true'
Take a look at for Mass Project vulnerability
Framework Misconfiguration: Spring Boot Actuator
Frameworks like Spring Boot can generally expose delicate data by way of endpoints just like the actuator, which aren’t all the time documented. A {custom} check will be crafted to particularly goal these endpoints, even when they aren’t a part of the documented API, to make sure they aren’t publicly accessible or leaking delicate knowledge:
alert:
title: Uncovered Spring Boot Actuator Endpoint
context: A Spring Boot Actuator endpoint is publicly accessible and will reveal
delicate data.
severity: HIGH
detect:
- if: response.status_code
is: 200
rework:
mutate:
- key: schema.path_ref
worth: /actuator/beans
set off:
- if: scan.sort
is: RESTElectronic mail Area Validation
This check focuses on validating that an API correctly handles e-mail inputs, significantly in fields labeled as “admin e-mail.” By utilizing common expressions to mutate the area a part of the e-mail handle, the check can verify if the API is appropriately validating e-mail domains and stopping unauthorized area utilization:
rework:
set off:
- if: schema.url
is: "/api/v1/examined/route"
mutate:
- key: request.object
choose:
sort:
is: e-mail
title:
is: "admin_email"
worth:
regex: .*@escape.tech
mutate:
regex_replace:
sample: (.*)@escape.tech
alternative: [email protected]Tenant Isolation
Tenant isolation is essential in multi-tenant environments to forestall customers from accessing knowledge belonging to different tenants. Customized exams will be created to simulate requests from completely different customers, guaranteeing that every tenant’s knowledge stays remoted and inaccessible to others. That is significantly necessary for SaaS purposes the place knowledge segregation is a key safety concern:
alert:
title: Deletion profitable
context: >
For compliance causes, the non-admin person should not be capable to delete some
knowledge through the API.
severity: HIGH
detect:
- if: helpers.request.crud
is: DELETE
- if: request.person
is_not: admin
- if: helpers.response.is_successful
is: trueAdmin Route Accessibility
This check verifies that administrative routes or endpoints are usually not accessible to non-admin customers. By making an attempt to entry URLs with “admin” within the path utilizing a non-admin person’s credentials, the check can determine if correct entry controls are in place to limit delicate areas of the API:
alert:
title: V2 API with V1 tokens
context: >
Your present API appears to be confused between V1 and V2 endpoints.
severity: LOW
detect:
- if: helpers.response.is_successful
is: true
rework:
set off:
- if: helpers.response.is_successful
is: true
- if: request.headers
key:
is: X-API-Model
worth:
is: V2
mutate:
- key: request.headers
title: X-API-Model
worth: V1
These examples display the flexibility and energy of {custom} enterprise logic exams. By abstracting the complexities of API testing, our language permits safety groups to give attention to the logic and conduct of their APIs, guaranteeing that they will rapidly and successfully determine and remediate vulnerabilities.
We have launched Escape’s public {custom} guidelines repository the place customers can share and collaborate on {custom} guidelines, additional enhancing the platform’s capabilities. This community-driven strategy ensures that our platform stays on the forefront of API safety.
Wanting forward
Our roadmap consists of thrilling options corresponding to Git synchronization and bulk import/export capabilities. We’re additionally engaged on extending {custom} rule creation to APIs within the stock, permitting for the detection of vulnerabilities in shadow APIs.
Conclusion
The introduction of {custom} enterprise logic exams represents a big leap ahead in API safety. By offering an easy-to-use language and a platform that automates the testing course of, we empower organizations to safe their APIs towards enterprise logic vulnerabilities successfully. We encourage you to check out this characteristic, share your guidelines with the group, and be part of us in our mission to create safer purposes.
For extra data or to debate your particular use circumstances, be happy to succeed in out to us or be part of our group. We’re right here to help you in leveraging the complete potential of {custom} enterprise logic exams in your API safety wants!
💡 Need to discover extra? Take a look at the next articles and webinars:
*** It is a Safety Bloggers Community syndicated weblog from Escape – The API Safety Weblog authored by Alexandra Charikova. Learn the unique put up at: https://escape.tech/weblog/workshop-how-to-write-custom-security-tests/
[ad_2]


