[ad_1]
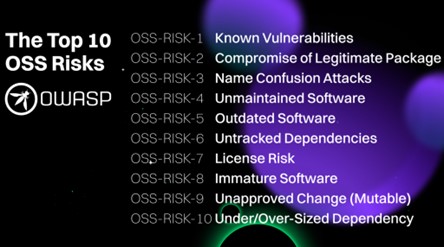
The highest 10 open supply dangers
OWASP
1: Recognized vulnerabilities
This part covers OSS parts with recognized vulnerabilities corresponding to software program flaws, usually inadvertently launched by software program builders and maintainers after which subsequently disclosed publicly, usually by safety researchers in the neighborhood.
These vulnerabilities could also be exploitable relying on the context by which they’re used inside a corporation and software. Whereas this level could seem trivial, it isn’t — failing to offer builders with this context results in important toil, wasted time, frustration and infrequently resentment in the direction of Safety.
There are efforts to deal with this problem, such because the CISA Recognized Exploited Vulnerability (KEV) catalog and Exploit Prediction Scoring System (EPSS).
Organizations can take actions to mitigate the chance of OSS parts with recognized vulnerabilities corresponding to scanning for vulnerabilities in all OSS parts they use, prioritizing findings based mostly on strategies corresponding to recognized exploitation, exploitation chance, reachability evaluation (which may cut back as much as 80% of noisy findings), and extra.
2: Compromise of a authentic package deal
Subsequent up on the checklist of Prime 10 OSS Dangers is the compromise of a authentic package deal. Malicious actors notice the worth of compromising a authentic package deal to influence downstream customers, each organizationally and individually.
There are a number of strategies they’ll use to pursue this assault vector, corresponding to hijacking the accounts of the challenge maintainers or vulnerabilities within the package deal repositories.
[ad_2]


