[ad_1]
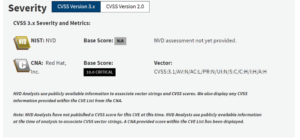
CVE-2024-3094 is a reported provide chain compromise of the xz libraries. The ensuing interference with sshd authentication may allow an attacker to achieve unauthorized entry to the system.
Overview
Malicious code was recognized throughout the xz upstream tarballs, starting with model 5.6.0. This malicious code is launched by a classy obfuscation approach in the course of the liblzma construct course of. A prebuilt object file is extracted and cleverly hidden inside a check file within the supply code. This object file then alters particular capabilities throughout the liblzma code. Consequently, any software program that depends on this compromised model of liblzma could unknowingly work together with a modified library. This manipulation permits for the interception and alteration of knowledge dealt with by the library.
An amazing breakdown could be discovered on linuxiac.com.
CVE-2024-3094 was possible detected earlier than it may considerably influence downstream manufacturing, stopping widespread points. This early detection is reassuring and highlights the significance of vigilance, but it shouldn’t result in a false sense of safety. You must take the next steps:
- Detect your publicity
At the beginning, establish your degree of publicity by checking when you’re utilizing XZ instruments variations 5.6.0 and 5.6.1. These working Fedora Linux 40 or any Fedora Rawhide occasion are at direct danger of receiving the backdoored bundle. Notably, RedHat Enterprise situations must be spared from this vulnerability. - Assess SSH Entry
Given the character of the risk, evaluating your SSH entry to potential risk vectors is crucial. Limiting your SSH publicity instantly is important to mitigate additional dangers if you end up uncovered. - Take Motion
CISA recommends that builders and customers downgrade XZ Utils to an uncompromised model, reminiscent of XZ Utils 5.4.6 Secure, to search for malicious exercise and report any optimistic findings to CISA. Further recommendation could be discovered right here.
How do I search for the bundle with OX
Take a look at your functions throughout the OX Lively ASPM Platform. (Notice: you may join a free trial when you don’t have OX. The connection is agentless,is predicated on APIs, and takes lower than a minute to deploy.)
- Log in
- The platform will routinely scan your related atmosphere from code to cloud.
- It should detect direct makes use of of XZ libraries and can alert the susceptible ones.
To find the utilization of XZ libraries:
- Seek for CVE-2024-3094 or in Points
- It should discover all direct and oblique xz utils libraries and present the model used. Notice: The secure variations of Linux distros weren’t affected. It’s principally beta/dev branches of these OSs
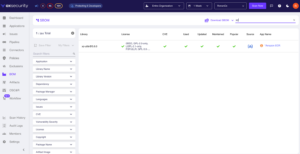
The instance reveals that it isn’t Fedora and is free from malicious code. Operating the scan saves time as you should not have to evaluate a number of functions.
On-going monitoring and group collaboration
Thanks to Andres Freund for his pivotal position in figuring out and reporting CVE-2024-3094, Lasse Collin, the maintainer of xz-utils, for promptly offering updates and dealing alongside the group to mitigate the safety dangers concerned, and to the safety groups whose swift actions have been essential in coordinating a response. Your contributions, underscored by collaborative efforts, are immensely valued and present how group is crucial in averting bigger incidents.
OX Safety will proceed to observe this case and supply updates as occasions unfold. Observe us on Linkedin and examine the OX Safety Weblog for any developments.
Further assets – Courtesy of Latio Tech
Listed here are the primary hyperlinks from completely different suppliers:
The put up Understanding and Mitigating the Fedora Rawhide Vulnerability (CVE-2024-3094) appeared first on OX Safety.
*** It is a Safety Bloggers Community syndicated weblog from OX Safety authored by Lior Arzi. Learn the unique put up at: https://www.ox.safety/understanding-and-mitigating-the-fedora-rawhide-vulnerability-cve-2024-3094/
[ad_2]