[ad_1]
This previous week, each JetBrains TeamCity and Atlassian Confluence merchandise have run into extra hiccups as their string of vulnerabilities continues. Apple’s additionally had loads to patch, and Cisco, OpenEdge, and VMware appeared within the information, too. JetBrains and Atlassian customers ought to pay particular consideration since vulnerabilities proceed cropping up in the identical merchandise. And all IT and safety groups ought to comply with vulnerability information for vendor bulletins and updates.
March 4, 2024
JetBrains Server Points Proceed with New Vulnerabilities
Kind of vulnerability: Authentication bypass.
The issue: Two authentication bypass vulnerabilities, CVE-2024-27198 and CVE-2024-27199, permit unauthenticated attackers to use JetBrains TeamCity servers. The extra extreme CVE-2024-27198 permits a risk actor to take over the whole server. Researchers at Rapid7 found these vulnerabilities in late February and launched info concerning them on March 4.
These are completely different JetBrains vulnerabilities than those talked about in previous recaps. We’ve seen a number of over the past couple of months, however these are new and to not be confused with CVEs from 2023. Potential exploits of the brand new vulnerabilities can embrace distant code execution on TeamCity servers.
JetBrains launched a detailed weblog publish explaining the particular timeline of discovering the vulnerabilities, the battle with Rapid7, and JetBrains’ stance on releasing vulnerability info. Its place is that instantly releasing vulnerability information to the general public permits risk actors to use the problems earlier than prospects have enough time to patch them.
Nevertheless, Rapid7’s coverage holds that silent patching limits the methods skilled IT professionals can take part in defending networks and data programs. Due to these variations, JetBrains determined to not coordinate with Rapid7 in disclosing the vulnerability info.
The repair: Deploy JetBrains TeamCity model 2023.11.4 to all servers that may help it. This launch contains set up recordsdata and up to date Docker photos. Based on JetBrains’ weblog publish, the brand new model and the associated safety patch plug-in solves each authentication bypass vulnerabilities.
March 5, 2024
New Apple Vulnerabilities Necessitate Speedy Patching
Kind of vulnerability: A number of points, together with kernel safety bypass vulnerabilities.
The issue: On March 5, Apple launched a safety discover for its new working programs, iOS 17.4 and iPadOS 17.4. These new OS variations fastened a number of CVEs. Two of the extra extreme vulnerabilities are CVE-2024-23225, present in Kernel, and CVE-2024-23296, present in RealtimeKit (RTKit). Each vulnerabilities permit an attacker to bypass commonplace kernel reminiscence protections when the attacker has arbitrary learn and write capabilities throughout the kernel.
Different CVEs fastened within the new replace included CVE-2024-23243, which allowed an utility to doubtlessly view delicate location information, and CVE-2024-23262, which allowed an utility to doubtlessly spoof system notifications and the consumer interface.
The repair: Deploy iOS 17.4 and iPadOS 17.4 to all units that can help them as quickly as doable. These releases repair over 30 vulnerabilities.
If your enterprise doesn’t have a very good methodology of rapidly discovering vulnerabilities, contemplate investing in a vulnerability scanning product particularly designed for web sites, purposes, or DevOps use instances.
VMware Vulnerability Impacts ESXi, Workstation & Fusion
Kind of vulnerability: Use-after-free vulnerability doubtlessly resulting in code execution.
The issue: CVE-2024-22252, a use-after-free vulnerability, may permit a risk actor to execute code utilizing admin privileges on a VMware digital machine. This problem impacts VMware ESXi, Workstation, and Fusion. Based on the Nationwide Instutite of Requirements and Know-how, the exploitation is contained throughout the VMX sandbox in ESXi, however in Workstation and Fusion, the vulnerability may result in code execution on machines the place the merchandise are put in.
Particular merchandise affected embrace:
- VMware ESXi
- VMware Workstation Professional / Participant (Workstation)
- VMware Fusion Professional / Fusion (Fusion)
- VMware Cloud Basis (Cloud Basis)
The repair: VMware created the next desk for customers in order that they know which fastened variations to use:

March 6, 2024
Cisco Provides Fastened Releases for Safe Consumer Vulnerability
Kind of vulnerability: Carriage return line feed (CRLF) injection assault by an unauthenticated distant attacker.
The issue: Cisco’s Safe Consumer software program has a vulnerability, CVE-2024-20337, that enables an attacker to finish a carriage return line feed injection assault. Based on Cisco, after exploiting the Safe Consumer vulnerability, an attacker may execute arbitrary code or entry delicate information within the browser, like legitimate SAML tokens. Whichever consumer’s privileges the attacker has exploited may then be used to create a distant entry VPN session.
Inadequate validation of user-supplied enter causes this vulnerability, in response to Cisco. It impacts the next merchandise:
- Safe Consumer for Linux
- Safe Consumer for macOS
- Safe Consumer for Home windows
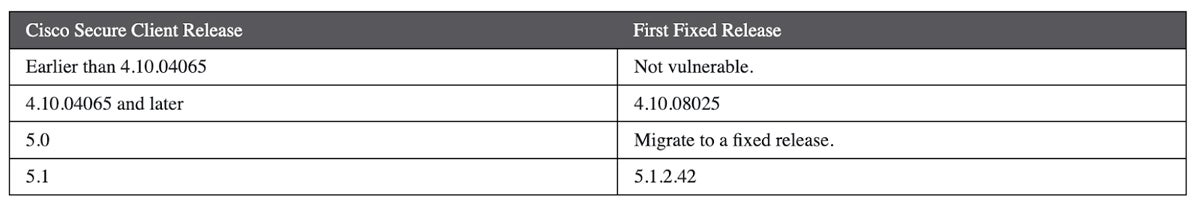
The repair: Cisco offers the next info on fastened software program releases:
Proof of Idea Launched for OpenEdge Vulnerabilities
Kind of vulnerability: Potential authentication bypass.
The issue: Progress Software program’s OpenEdge Authentication Gateway and AdminServer have a vulnerability within the following variations:
- OpenEdge Launch 11.7.18 and earlier
- OpenEdge 12.2.13 and earlier
- OpenEdge 12.8.0
Based on Progress, when OpenEdge Authentication Gateway “is configured with an OpenEdge Area that makes use of the OS native authentication supplier to grant user-id and password logins on working platforms supported by energetic releases of OpenEdge, a vulnerability within the authentication routines could result in unauthorized entry on tried logins.”
The identical unauthorized login entry can happen when OpenEdge Explorer (OEE) and OpenEdge Administration (OEM) hook up with AdminServer. The vulnerability, CVE-2024-1403, has a vital severity score.
Progress additionally notes that AdminServer logins are at all times weak as a result of they solely help OS native logins. OpenEdge Authentication Gateway is simply weak to authentication bypass when admins configure OpenEdge domains to make use of the working system’s native authentication supplier.
Progress launched the discover in late February; on March 6, Horizon3AI launched a proof of idea for an OpenEdge exploit. The proof of idea is on the market on GitHub for customers, in addition to a longer weblog publish that gives detailed code info and walks professionals by Horizon3AI’s course of.
The repair: Progress Software program has launched the next variations of OpenEdge LTS, during which the vulnerability is fastened:
March 8, 2024
Exploits of Confluence Vulnerabilities Proceed
Kind of assault: Distant code execution.
The issue: CVE-2023-22527, a distant code execution vulnerability in outdated variations of Atlassian Confluence Knowledge Heart and Confluence Server, is at the moment being actively exploited. Atlassian disclosed the vulnerability in January, however risk actors proceed to capitalize on the problem: VulnCheck just lately printed a weblog publish and famous that the vulnerability has at the very least 30 distinctive exploits, as of March 8.
VulnCheck additionally noticed that a number of cases of exploitation use freemarker.template.utility.Execute, which can simply be picked up by endpoint detection and response platforms.
The vulnerability impacts the next Confluence Knowledge Heart and Server variations:
- 8.0.x
- 8.1.x
- 8.2.x
- 8.3.x
- 8.4.x
- 8.5.0-8.5.3
The repair: Atlassian recommends updating your occasion of Confluence Knowledge Heart or Confluence Server to one of the crucial latest variations:
- Confluence Knowledge Heart and Server:
- Confluence Knowledge Heart solely:
- 8.6.0 (Knowledge Heart Solely)
- 8.7.1 (Knowledge Heart Solely)
- 8.7.2 (Knowledge Heart Solely)
Learn subsequent:
Featured Companions: Vulnerability Administration Software program
[ad_2]


